
Ransomware continues to represent one of the most pervasive and damaging threats in the global cybersecurity landscape. In the regular “DarkMirror” report produced by Red Hot Cyber’s DarkLab intelligence laboratory, covering the first half of 2025, ransomware attacks showed a significant evolution in both the techniques used and the targets attacked. This report offers an overview of the main trends that have emerged, with a focus on quantitative data and the implications for cybersecurity.
The Italian and global ransomware threat trends for the second half of 2025 are analyzed, with a focus on emerging trends, criminal groups’ tactics, and the impact on various sectors. The Threat Actors section focuses on new threats (insiders), affiliation and monetization models, the evolution of RaaS services, law enforcement operations, Initial Access Brokers (IaB), Common Vulnerabilities and Exposures (CVEs), and mitigation methods.
The report was produced by the DarkLab group and specifically by Pietro Melillo, Luca Stivali, Edoardo Faccioli, Raffaela Crisci, Alessio Stefan, Inva Malaj, and Massimiliano Brolli.
Download DarkMirror H1-2025: Ransomware Threat Report
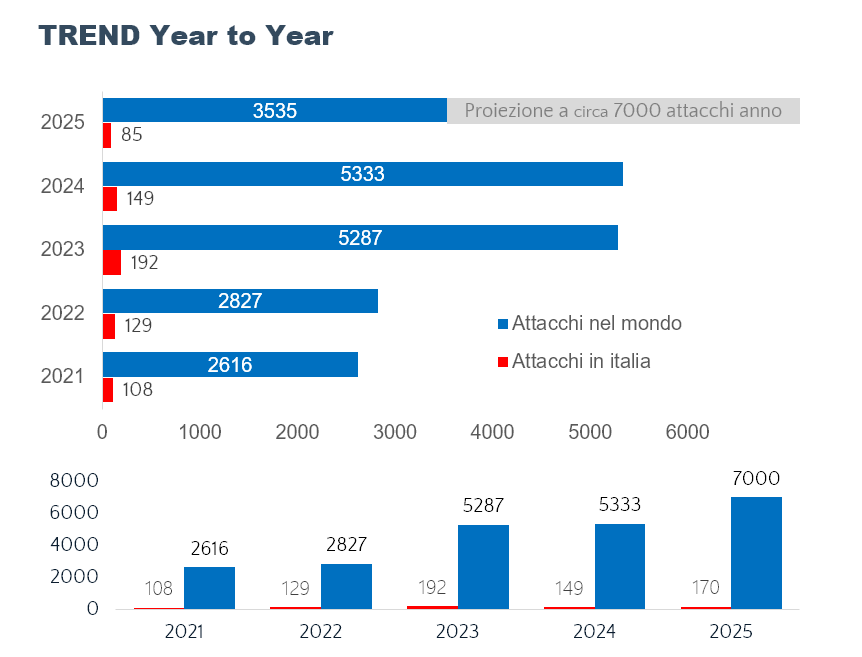
The ransomware phenomenon in 2025 continued to pose a persistent and growing threat (As seen in the excerpt by Pietro Melillo and Inva Malaj), affecting both developed and developing economies alike. According to data collected by Dark Lab, 3,535 attack victims have been documented globally, an increase of approximately 1,000 incidents compared to H1 2024. This number represents only a fraction of the true extent of the problem. The United States remains the most affected country, with 1,861 documented victims, followed by Canada with 202, the United Kingdom with 152, and Germany with 145.
Industry and services emerge as the economic sectors most targeted by ransomware attacks. With 595 recorded attacks, the industrial sector is the most affected, due to vulnerabilities in its IT infrastructure. The services sector follows with 580 attacks, highlighting significant risks in the management of critical data. Retail, with 371, and construction, with 310, are also particularly exposed sectors.
In conclusion, ransomware remains one of the most consolidated and profitable businesses of the criminal underground, showing no signs of slowing down, as evidenced by the trends in this report. This demonstrates that, despite the significant efforts made by organizations in recent years, this threat remains among the most insidious, which companies are forced to confront on a daily basis.
Download DarkMirror H1-2025: Ransomware Threat Report
During the observation period, 85 ransomware attacks were documented in Italy, underscoring the urgency of strengthening security in the most vulnerable sectors. Ransomware activity is mainly concentrated in the industrial and service sectors, considered priorities by threat actors, while public administration, healthcare, and education, although less affected, remain at risk.
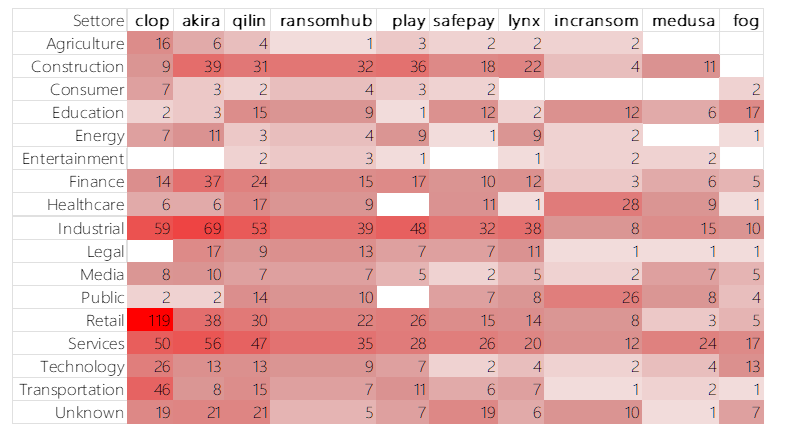
A few groups dominate the landscape, with Akira leading the way and others like Qilin and Sarcoma significantly active, accompanied by a series of less frequent but consistent actors.
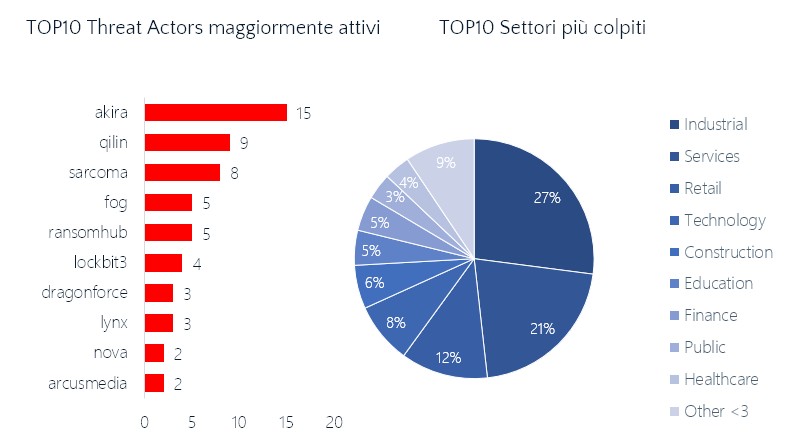
The Akira group stands out as the most active threat actor, responsible for 15 attacks. Qilin follows with 9 attacks, Sarcoma with 8, then Fog and Ransomhub, both with 5 attacks. Lockbit3 totals 4 attacks, while Dragonforce and Lynx each account for 3 attacks. Nova and Arcusmedia close the ranking with 2 attacks each.
Download DarkMirror H1-2025: Ransomware Threat Report
From the sector analysis, ransomware shows a clear predilection for the industrial sector, which is the most affected globally with 595 attacks. It is followed by the services sector (580 attacks) and the retail sector (371 attacks), demonstrating that attacks do not spare critical infrastructure and essential services.
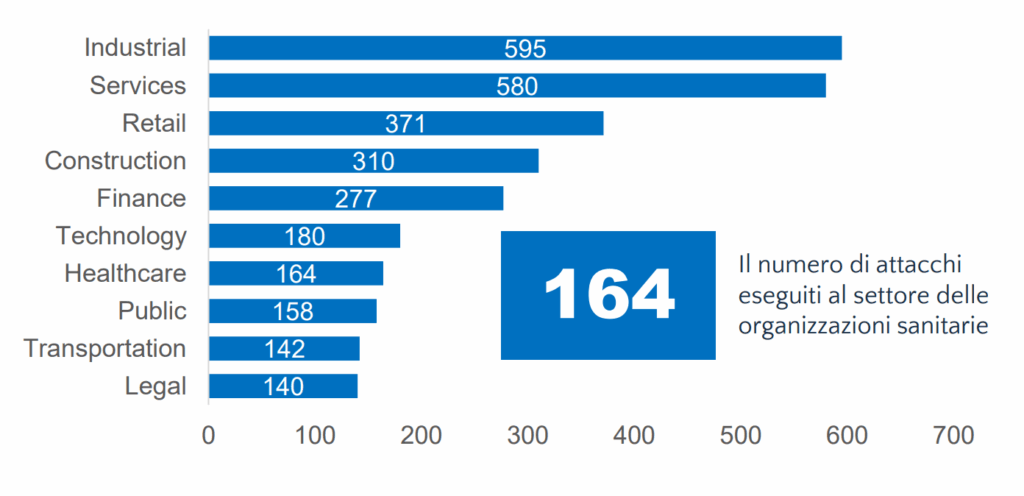
The construction (310 attacks) and finance (277 attacks) sectors also rose to the top spots, highlighting growing concerns about the security and resilience of these sectors.
The healthcare sector, with 164 attacks, remains particularly vulnerable, but is preceded by the industrial, services, retail, construction, finance, and technology sectors (180 attacks). The public, transportation, and legal sectors are also frequently targeted, demonstrating how dependence on digital technologies and data management are factors that increase attractiveness for cybercriminals.
Download DarkMirror H1-2025: Ransomware Threat Report
2024 was a year of major changes for the ecosystem that fuels ransomware and other digital threats. Operations by government agencies and intelligence agencies have severely impacted RaaS like LockBit, infostealer campaigns, and Malware-as-a-Service, as well as arresting (some) of the perpetrators behind these actions. The LockBit backend leak (along with analyses of RaaS wallets) has prompted several analysts to reflect on the decline in ransom payments, which has led to an increase in stolen files published on the groups’ DLS, as predicted by the attackers’ extortion model. This has led to a spike in the number of (visible) victims observed by various threat analysts. In this report, we will present our analysis of these movements, attempting to downplay the threat, which, despite the response from law enforcement, appears to have no intention of abandoning the scene.
Ransomware remains one of the most persistent and impactful threats on the scene, evolving not only operationally but also in terms of business models, advancing alternatives to incentivize operators to continue their campaigns. The emergence of organizations like DragonForce highlights a proactive approach to compensating for the decline of RaaS like ALPHV/BlackCat and LockBit, seeking to regain market share and affiliates who are spreading across existing RaaS or creating new ones.
Collectives like Cl0p and Hunters are changing their monetization methodology and approach, removing the use of their ransomware (Hunters) or focusing on the discovery, creation, and use of zero-days at scale (Cl0p). The players involved are demonstrating extraordinary resilience that goes far beyond the simple rebranding we were accustomed to in previous years. This, combined with the fragmentation of the various RaaS, makes it difficult to protect against ongoing campaigns given their silent nature and difficult technical and operational detection. The other side of the coin draws attention to unidentified actors actively pursuing RaaS deception (such as the LockBit leak and Everest defacement), providing the infosec community with valuable material for analysis.
Today more than ever, given the complexity of the landscape, threat intelligence must be combined with defenders’ technical capabilities to adequately respond to the changing ransomware landscape. Furthermore, we must support law enforcement operations that, while not completely eliminating the RaaS model, are able to disrupt and sabotage RaaS and MaaS functions, attempting to discourage or arrest those responsible, creating an increasingly hostile climate for them. Although some specific individuals cannot be reached (for geographical, political, or technical reasons), other key components (e.g., developers, negotiators, operators, affiliates) have been stopped and brought to justice.
The first half of 2025, despite the (apparent) decline in ransom payments and police/intelligence activities, has put threats to the test. Despite some isolated cases having been disarmed, they still manage to maintain a thriving environment for their activities, underscoring the importance of cybersecurity for organizations, which must be present and continuous over time.
In conclusion, ransomware remains one of the most consolidated and profitable businesses of the criminal underground, showing no signs of slowing down, as evidenced by the trends in this report. This demonstrates that, despite the significant efforts made by organizations in recent years, this threat remains among the most insidious that companies are forced to confront on a daily basis.
Download DarkMirror H1-2025: Ransomware Threat Report
Follow us on Google News to receive daily updates on cybersecurity. Contact us if you would like to report news, insights or content for publication.
