
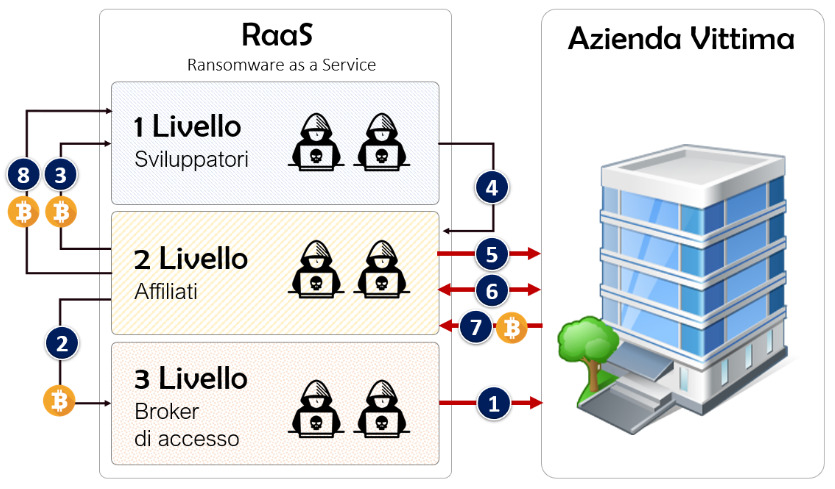
We’ve often talked about how ransomware attacks work and how the ransomware as a service (RaaS) pyramid works, which assigns a role to each team of criminal hackers, as seen in the article What is ransomware?
In the popular imagination, cybercrime is thought to be linked to individuals with exceptional computer skills. But if you want to extort millions of dollars from a large company, you can’t do it all alone; you need a “team” with diverse, advanced, and vertical IT skills.
In fact, the vast majority of cybercriminals do not have all the necessary technical skills to do everything themselves and then create malware, extort money and penetrate companies.
This is precisely why cybercriminals begin to collaborate with each other in an “organized” manner, for a single purpose: to extort as much money as possible from a hypothetical organization.
A web store generally doesn’t have a warehouse. It has products made available to it by a series of suppliers and resells them only when a specific request is made.
This is precisely why cybercriminals don’t spend too much time finding vulnerabilities in systems to land inside the network of a large organization, but rather purchase them from other cybercriminals who put them up for sale on underground markets: hence the Access Brokers.
Access Brokers are cybercriminals with good knowledge of penetration testing techniques. They detect security flaws within the IT infrastructure of large organizations and, once discovered, resell them on underground forums and to other cybercriminals.
These vulnerabilities, which can be put up for sale by Ranging from €500 to €20,000 (depending on the company’s revenue as we saw in a previous article), these allow other cybercriminals to speed up their operations by taking advantage of work already done by other cybercriminals.
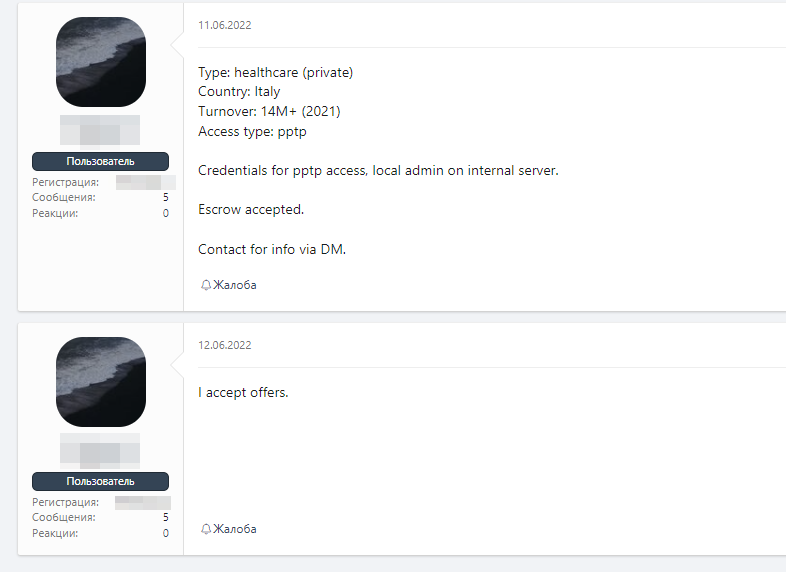
The first example was discovered on the infamous XSS forum, which reports the sale of access to an Italian healthcare company. The post advertises the revenue, type of access, and contact details.
A buyer immediately below expressed interest and told the broker to accept the offer, and who knows how it would have turned out.
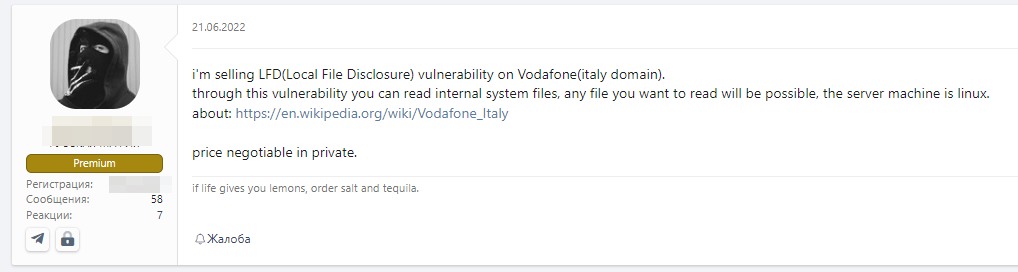
Below, we show another post, where a broker is selling alleged access to Vodafone Italy, asking for a private negotiation.
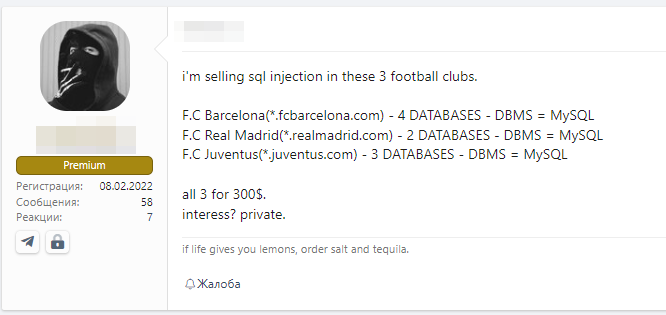
We also found two posts offering alleged access to the Juventus Football Federation’s systems for sale. The first, according to the hacker, involves the sale of a “payload” for access to three SQL databases.
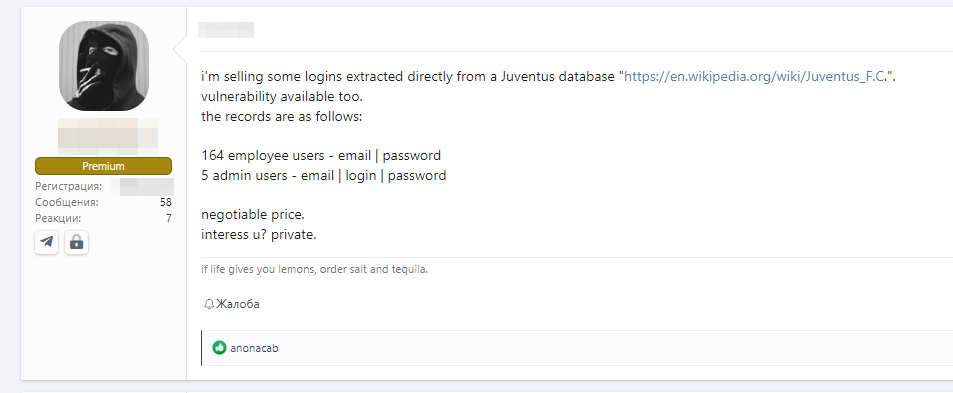
While the second is selling an alleged access (email and password) of 164 employees and 5 administrators, also of the Juventus Football Federation.
Obviously, not We can know for sure whether these logins are actually functional, but typically, within underground forums, login resale works this way, with few scams involving various cybercriminals.
The link you find in the Wikipedia posts serves to show the buyer of the security flaw which company was breached and to display its revenue. This allows the buyer to accurately estimate the hypothetical sum of money that may be demanded as a ransom if the infrastructure is breached and encrypted by ransomware.
All the posts above are from June 2022. Therefore, if companies would like further information, they can contact us via email. editorial staff and we will be happy to assist you.
As we’ve seen, purchasing security vulnerabilities from an access broker allows you to speed up a cyber attack, and it also helps you choose your target based on revenue.
So don’t think that when a ransomware attack hits your company, it’s because cybercriminals have targeted you. It’s likely because access to your network was for sale on underground markets, and your revenues were in line with the ransom demanded after the ransomware was encrypted.
This article also highlights a simple point: the advantage of being the first to know this type of information. Having up-to-date information on what’s being discussed or negotiated within underground markets regarding your assets is of considerable strategic importance.
In the meantime, it’s possible to follow the threat’s evolution and anticipate the attackers’ moves, thus taking action. For example, if it’s known that a negotiation for access is underway, the company could increase its focus on certain types of assets (such as Linux for the broker selling access to Vodafone), or perform security checks on PPTP/VPNs, as in the case of the healthcare organization, and then change administrator passwords. Or perform mass password resets in the case of Juventus.
This is the strategic importance of threat intelligence in today’s threat landscape. Working in this way, it’s possible to compete on an equal footing with cybercriminals and therefore respond promptly to cyberattacks before they happen.
Follow us on Google News to receive daily updates on cybersecurity. Contact us if you would like to report news, insights or content for publication.
