
Dopo estremo oriente e Iran, continuiamo la nostra serie di articoli su attori di tipo IAB con un attore che si pensa sia di base in Europa, in un paese NATO.
Secondo i ricercatori di KelaCyber (vendor di servizi di Cyber Threat Intelligence di Tel Aviv, Israele), l’attore Drumrlu, è uno IAB che presumibilmente ha base in Turchia.
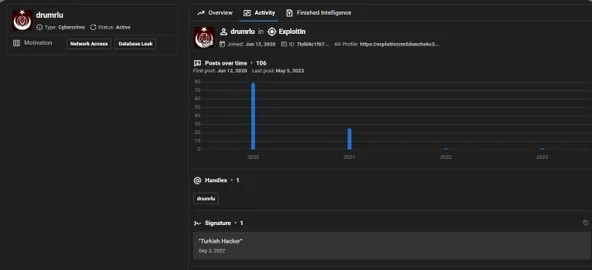
Drumrlu è anche noto con il nome/moniker “3LV4N”.
Come visto nel primo articolo sull’access broker miyako, lo ricerca delle entrate delle vittime da parte dello IAB, è una pratica molto comune per questi attori, i cui post tendono appunto a menzionare le entrate delle vittime per invogliare i potenziali acquirenti. Si parte dal presupposto che organizzazioni con entrate più elevate abbiano il potenziale di garantire un riscatto multimilionario.
–
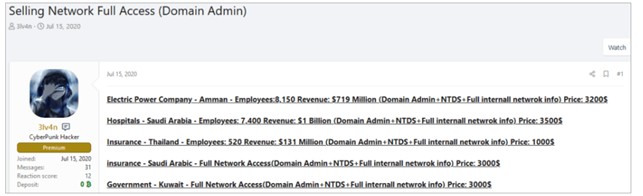
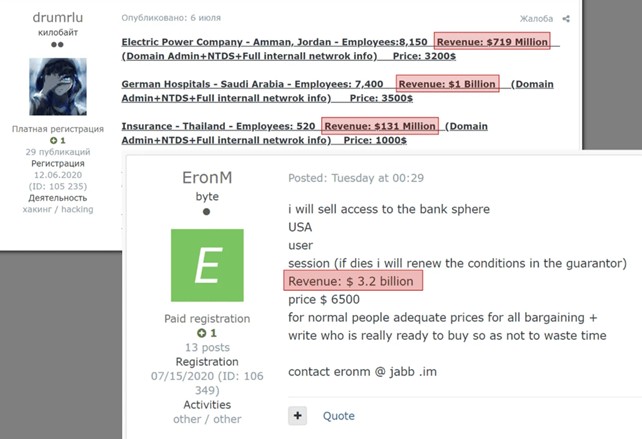
“drumrlu” (alias 3lv4n) è un broker di accesso iniziale e un venditore di database di credenziali attivo nei forum clandestini almeno dal maggio 2020. drumrlu ha venduto accessi a domini di varie organizzazioni in molti paesi del mondo (EMEA, APAC e AMER) nei settori dell’istruzione, dei servizi pubblici, delle assicurazioni, della sanità, delle criptovalute, dei giochi e del governo. Nell’ ottobre del 2020, l’attore ha iniziato a vendere accessi root al software VMware ESXi con prezzi compresi tra 250 e 500 dollari.
Gli analisti di Outpost24 hanno osservato che “Nosophoros”, l’attore dietro il Ransomware as a Service (RaaS) Thanos, probabilmente collabora con (è cliente di) drumrlu. Il 18 luglio 2020, Nosophoros ha postato sul forum “Exploit” il messaggio: “drumrlu è un buon fornitore, ho garantito per lui in passato e continuo a farlo. Sono contento che sia tornato”.
“drumrlu is a good vendor, I vouched for him before and I still do. Glad you are back”.
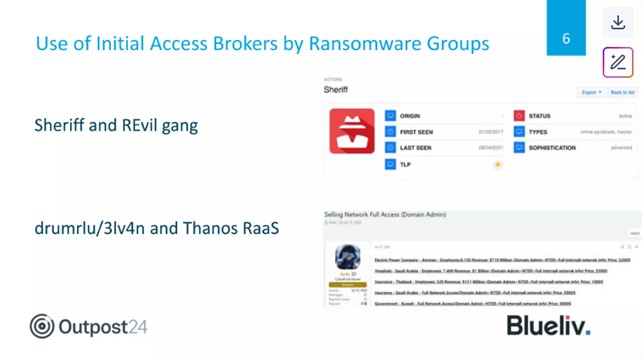
Simon Roe, ricercatore e product manager presso Outpost24, in un suo report evidenza come drumrlu/3LV4N abbia operato nella operazione RaaS Thanos.
drumrlu ha anche lasciato una recensione nel profilo di Nosophoros dicendo di lui: “Best RaaS, Best Programmer”. Un altro commento dell’attore “peterveliki” conferma la potenziale partnership tra drumrlu e Nosophoros: “Ho acquistato un accesso da questo venditore (drumrlu) – è andato tutto liscio. Un tipo molto disponibile. Mi ha anche consigliato di usare Thanos di Nosphorus, che si è rivelato essere molto utile in questo caso. Ottimo venditore, lo consiglio”.
“I bought access from this seller – everything went smoothly. A very helpful dude. He also recommended using Thanos from Nosphorus; which turned out to be very helpful in this case. Good seller, I recommend”
Secondo ProofPoint una catena di attacco su RaaS Thanos con accessi iniziali forniti dallo IAB drumrlu potrebbe essere questa:
1. Invio di e-mail contenenti un documento Office dannoso
2. Un utente vittima scarica il documento e attiva le macro che rilasciano un payload (un RAT e/o InfoStealer)
3. L’attore sfrutta l’accesso backdoor per esfiltrare informazioni di sistema/accessi
4. A questo punto, il broker di accesso iniziale può vendere l’accesso ad altri attori
5. Inoltre può distribuire Cobalt Strike tramite l’accesso backdoor del malware che consente il movimento laterale all’interno della rete
6. Ottiene quindi compromissione completa del dominio tramite Active Directory
7. L’attore affiliato al RaaS distribuisce il ransomware a tutte le stazioni di lavoro collegate al dominio.
Possibile phishing email per furto di credenziali con allegato documento Office dannoso da indirizzo email free GMX.COM.

File EXCEL XSLM con malware GuLoader (aka CloudEyE o vbdropper).
Fonte ProofPoint
Paesi target
Australia, Stati Uniti, Thailandia, Pakistan, Francia, Italia, Svizzera, Emirati Arabi Uniti, Giordania, Israele, Egitto, Kuwait e Arabia Saudita.
Settori target
Istruzione, servizi pubblici, assicurazioni, sanità, criptovalute, giochi e entità governative.
Il DoJ USA presume che un cardiologo sia lo sviluppatore che ha creato il ransomware Thanos: Moises Luis Zagala Gonzalez, 55 anni, cittadino francese e venezuelano residente a Ciudad Bolivar, Venezuela, è accurato di aver commesso tentativi di intrusione informatica e di associazione a delinquere finalizzata al commettere intrusioni informatiche, secondo una denuncia penale statunitense resa pubblica lunedì 16 maggio 2022.
Zagala avrebbe venduto e affittato pacchetti ransomware da lui sviluppati a criminali informatici. È inoltre accusato di aver addestrato gli aspiranti aggressori/gli affiliati sul come utilizzare i suoi prodotti per estorcere le vittime e di essersi successivamente vantato degli attacchi riusciti.
Una serie di errori di Zagala, avrebbe permesso agli investigatori di identificarlo come sospetto, ha dichiarato il DoJ. Nel settembre 2020, un agente dell’FBI sotto copertura avrebbe acquistato una licenza per Thanos da Zagala e scaricato il software. Inoltre, un informatore dell’FBI ha parlato con Zagala della possibilità di istituire un programma di affiliazione utilizzando Thanos, sempre secondo il documento del DoJ.
Zagala si sarebbe vantato pubblicamente nel DarkWeb del fatto che il RaaS Thanos, la sua creatura, era stato usato da parte di un gruppo di threat actors sponsorizzato dallo Stato iraniano per attaccare aziende israeliane.

Fonte PDF (FBI.GOV)
https://www.fbi.gov/wanted/cyber/moises-luis-zagala-gonzalez/@@download.pdf
In questo articolo della serie sugli initial access broker abbia visto come il furto di credenziali avvenga attraverso campagne di phishing con allegati Office contenenti malware/infostealer… Quindi ricordiamo alcune delle best practice menzionate in precedenza per essere pronti ad ogni evenienza
–
KelaCyber
https://www.kelacyber.com/blog/uncovering-your-adversaries-with-kelas-threat-actors-hub
https://www.kelacyber.com/blog/the-secret-life-of-an-initial-access-broker
Report di Outpost24
RaaS THANOS su RecordedFuture
https://www.recordedfuture.com/research/thanos-ransomware-builder
Bleeping Computer su Thanos
https://www.bleepingcomputer.com/news/security/european-victims-refuse-to-bow-to-thanos-ransomware
PortSwigger su Thanos
ProffPoint su Thanos
Malpedia Fraunhofer su GuLoader/CluodEyE
https://malpedia.caad.fkie.fraunhofer.de/details/win.cloudeye
FBI
https://www.fbi.gov/wanted/cyber/moises-luis-zagala-gonzalez/@@download.pdf
Ti è piaciuto questo articolo? Ne stiamo discutendo nella nostra Community su LinkedIn, Facebook e Instagram. Seguici anche su Google News, per ricevere aggiornamenti quotidiani sulla sicurezza informatica o Scrivici se desideri segnalarci notizie, approfondimenti o contributi da pubblicare.

 Innovazione
InnovazioneL’evoluzione dell’Intelligenza Artificiale ha superato una nuova, inquietante frontiera. Se fino a ieri parlavamo di algoritmi confinati dietro uno schermo, oggi ci troviamo di fronte al concetto di “Meatspace Layer”: un’infrastruttura dove le macchine non…
 Cybercrime
CybercrimeNegli ultimi anni, la sicurezza delle reti ha affrontato minacce sempre più sofisticate, capaci di aggirare le difese tradizionali e di penetrare negli strati più profondi delle infrastrutture. Un’analisi recente ha portato alla luce uno…
 Vulnerabilità
VulnerabilitàNegli ultimi tempi, la piattaforma di automazione n8n sta affrontando una serie crescente di bug di sicurezza. n8n è una piattaforma di automazione che trasforma task complessi in operazioni semplici e veloci. Con pochi click…
 Innovazione
InnovazioneArticolo scritto con la collaborazione di Giovanni Pollola. Per anni, “IA a bordo dei satelliti” serviva soprattutto a “ripulire” i dati: meno rumore nelle immagini e nei dati acquisiti attraverso i vari payload multisensoriali, meno…
 Cyber Italia
Cyber ItaliaNegli ultimi giorni è stato segnalato un preoccupante aumento di truffe diffuse tramite WhatsApp dal CERT-AGID. I messaggi arrivano apparentemente da contatti conosciuti e richiedono urgentemente denaro, spesso per emergenze come spese mediche improvvise. La…