
We continue our series of articles on Initial Access Brokers with an article on JohnDoe7 (also known as LORD1), who, as we’ll see later, uses a name/moniker reminiscent of movies or the US legal world.
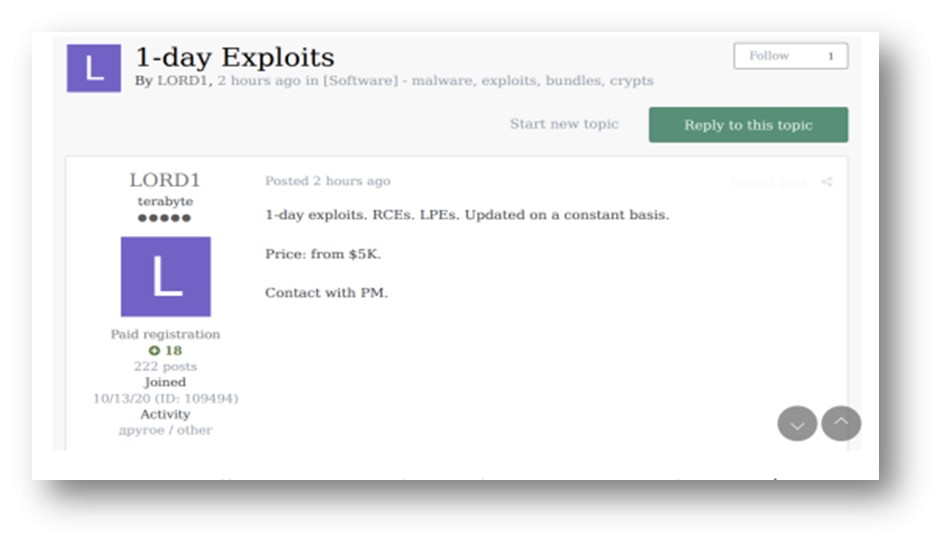
KELA Cyber has observed a steady stream of exploits for 1-day vulnerabilities, confirming that the IAB, like other actors, are interested in targeting organizations that have failed to patch their environments in a timely manner. Pictured here on Exploit in October 2020, LORD1 offers an RCE and LPE exploit priced starting at $5,000.
In June 2023, johndoe7 aka LoRD1 on XSS and Exploit offered a custom malicious script to exploit the Progress MOVEit Transfer vulnerability (CVE-2023-34362). In May 2023, the CL0P ransomware group targeted Progress Software’s MOVEit Transfer, commonly used by organizations to manage file transfer operations. They exploited the zero-day SOL injection vulnerability (CVE-2023-34362) to infiltrate MOVEit Transfer’s web applications and gain unauthorized access to stored databases. This could suggest a connection between johndoe7 and the CL0P gang…
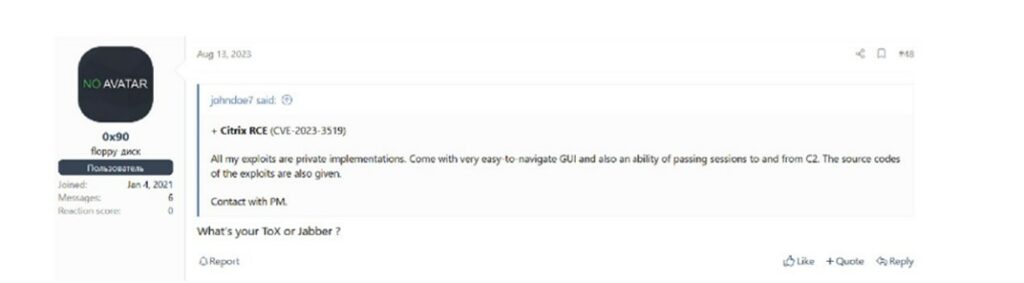
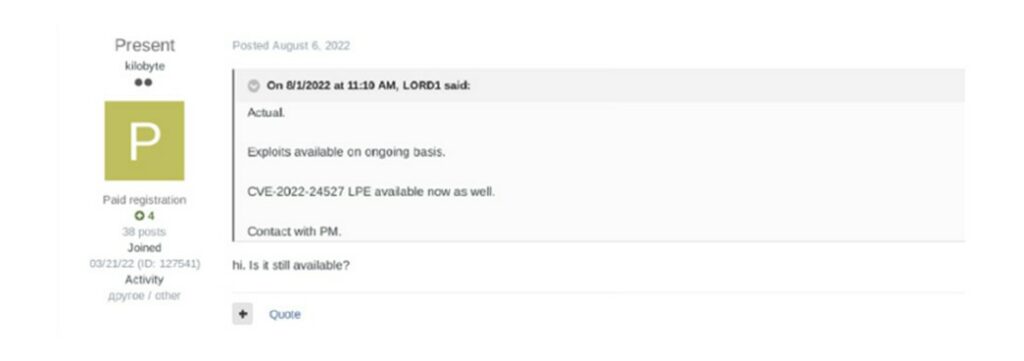
In the following example in the XSS and Exploit forums, the malicious actors “0x90” and “Present” express their interest in purchasing exploits for CVE-2023-3519 (RCE on Citrix) and CVE-2022-24527 (LPE on Microsoft Connected Cache).
–
–
According to a SOCRadar report, LORD1 is very active in compromising credentials related to the world of cryptocurrencies and NFTs; Analysis conducted by the SOCRadar research team reveals that the majority of the approximately 1,700 unique Dark Web threats detected since 2021 involve the sale of compromised user data on a global scale. Therefore, malicious actors targeting the cryptocurrency and NFT industry pose a global threat to all users.
The most widespread threat in the cryptocurrency and NFT industry is the compromise and subsequent sale of personal information of industry users on dark web forums.
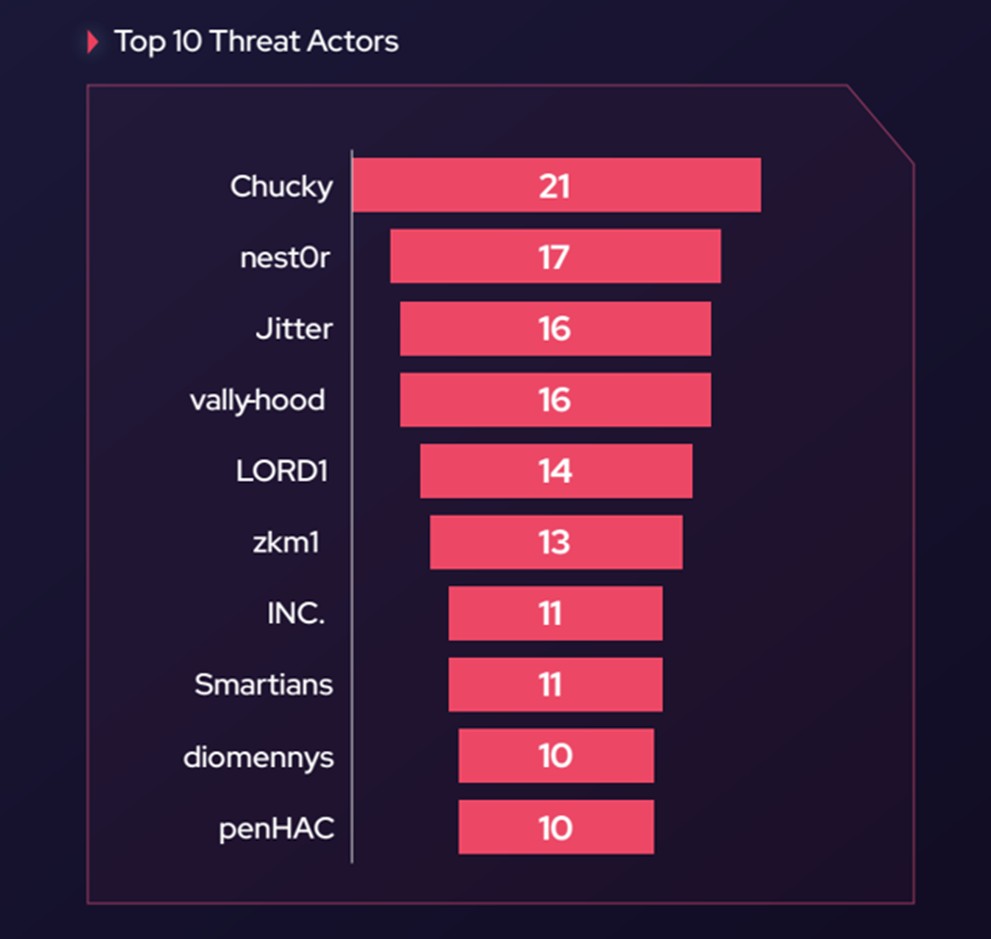
In the previous graph, taking the total number of credential compromise cases analyzed by SOCRadar during the period as 100, each segment shows the percentage of contribution attributed to each malicious actor: LORD1 ranks fifth in the TOP 10 with a contribution of 14 percent.
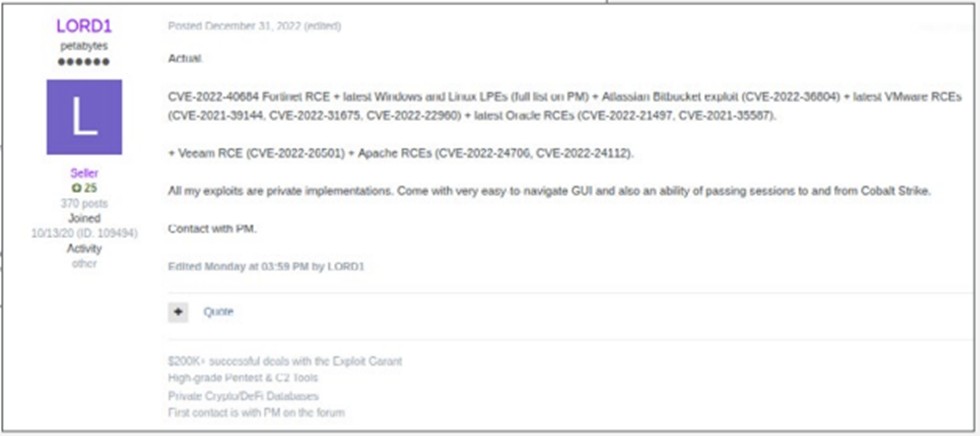
ATLASSIAN BITBUCKET COMMAND INJECTION (CVE-2022-36804)
Disclosed in August 2022, CVE-2022-36804 is a command injection vulnerability affecting multiple Bitbucket server API endpoints. Using this vulnerability, attackers with access to a public repository or with read permissions to a private Bitbucket repository can execute arbitrary code by sending a malicious HTTP request.
FORTINET: AUTHENTICATION BYPASS VULNERABILITY (CVE-2022-40684)
Disclosed in September 2022, this vulnerability allows an unauthenticated attacker to perform operations on the administrative interface of the FORTINET appliance via specially crafted HTTP or HTTPS requests by bypassing authentication using an alternate path or channel [CWE-288] in Fortinet FortiOS versions 7.2.0 through 7.2.1 and 7.0.0 through 7.0.6, FortiProxy version 7.2.0 and version 7.0.0 up to 7.0.6 and FortiSwitchManager version 7.2.0 and 7.0.0.
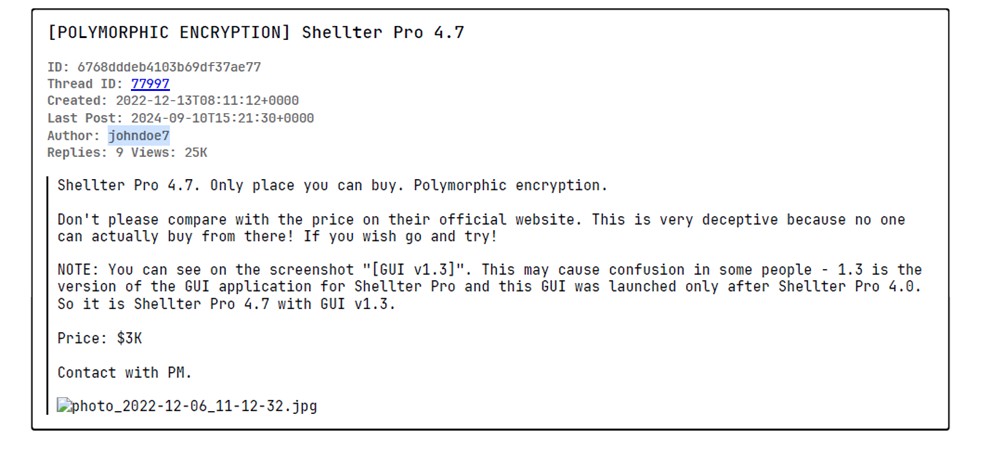
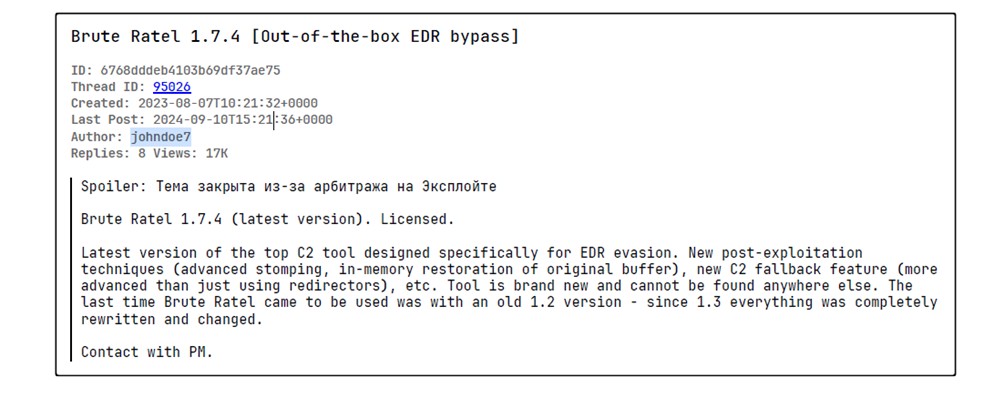
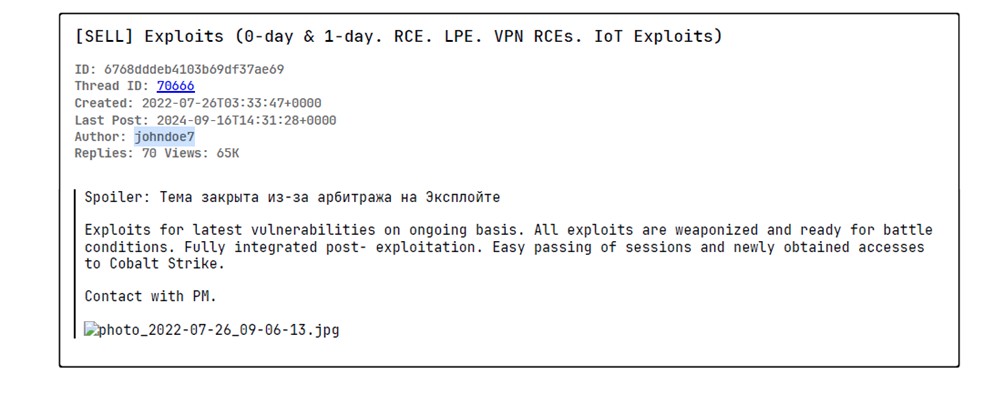
More Johndoe7 tracks from 2022 in the XSS forum ( https://xss.ist/forums/104 )
–
–
–
Curiosity, “John Doe” is the name of the villain from the film SE7EN.
https://villains.fandom.com/it/wiki/John_Doe
In the US, the name John Doe is used for an unknown or anonymous victim or defendant in a legal case. It is also the name officially given to the bodies of unknown individuals.
In Italy, it is the equivalent of Unknown or NN (from the Latin Nomen Nescio).
1-day vulnerabilities are known vulnerabilities for which a remediation patch or a mitigations, but have not yet been applied. The term “one day” refers to the period between the disclosure of the vulnerability and the patching of affected systems.
These vulnerabilities are sometimes referred to as “n-day” vulnerabilities, as the period is often much longer than one day, given that the mean time to apply a patch (MTTP) is typically between 60 and 150 days.
Unfortunately, the exploitation of one-day vulnerabilities is often accelerated by the release of proof-of-concept (PoC) exploit code before affected users have had time to patch their systems. This practice appears to have worsened as some cybersecurity researchers seek to showcase their technical prowess by creating PoCs, despite the resulting harm.
While more sophisticated threat actors reverse-engineer a patch to understand what problem it was intended to fix and then develop their own exploits based on their findings, less technical threat actors adopt/use publicly available PoC code. This allows the vulnerability to be exploited by less technically skilled malicious actors who would otherwise be unable to do so without outside assistance.
A recent and notable example of a one-day vulnerability is CVE-2024-1708, an authentication bypass flaw, and CVE-2024-1709, a path traversal flaw, in ConnectWise’s ScreenConnect servers. Just one day after the vulnerabilities were announced, several researchers released the PoC exploit code and technical details related to the vulnerabilities. This code, combined with the ease of identifying vulnerable ScreenConnect instances via online web scanners, has led to mass exploitation and distribution of ransomware and other malware on unpatched servers.
In this article in the series on initial access brokers, we saw how credential theft can also occur through attacks that exploit RCE and LPE vulnerabilities and how it is essential to apply patches and remediation as soon as possible… So, let’s remember some of the best practices mentioned above to be prepared for any eventuality.
KelaCyber 2022 Q2 Report https://www.kelacyber.com/wp-content/uploads/2022/08/KELA-RESEARCH_Ransomware-Victims-and-Network-Access-Sales_Q2-2022.pdf
Outpost24 IAB Report https://outpost24.com/wp-content/uploads/2024/11/IAB-and-links-to-ransomware.pdf
Soc Radar report https://socradar.io/wp-content/uploads/2024/03/SOCRadar-Cryptocurrency-NFT-Threat-Landscape-Report.pdf
Cyble underground report https://www.osintme.com/wp-content/uploads/2023/03/Cyble_Underground_Report.pdf
XSS Forum https://xss.ist/forums/104
Seven (Film, 1995) https://it.wikipedia.org/wiki/Seven
Follow us on Google News to receive daily updates on cybersecurity. Contact us if you would like to report news, insights or content for publication.
