
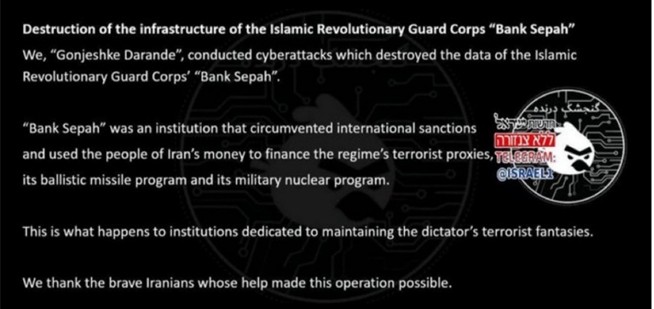
On June 17, 2025, a cyber attack paralyzed Bank Sepah, one of Iran’s major financial institutions.
The attack was claimed by the Predatory Sparrow group, already known for its destructive operations against Iranian critical infrastructure. In this document there is an in-depth analysis of the Threat Actor Predatory Sparrow, its technical capabilities and declared objectives, with particular attention to the geopolitical context and the use of proprietary malware.
Authors:
Main Name: Predatory Sparrow
Alternative Names: – Gonjeshke Darande (گنجشک درنده – Farsi translation) – Indra (partial overlap, similarities in malware code used)
Classification: Pro-Israeli hacktivist group
First Sighting: 2021
Current Status: Active (last documented activity: June 2025)

Predatory Sparrow presents itself as a self-proclaimed hacktivist group, but its technical sophistication and operational capabilities suggest likely government or military involvement. According to a WIRED article, US defense sources told the New York Times that the group was linked to Israel.
The group, founded in 2021, went into a state of dormancy between 2022 and October 2023, returning to operation when hostilities began in the Gaza Strip.
| Adversary | Predatory Sparrow/Gonjeshke Darande |
| Victim | Entities affiliated with the Iranian Ayatollah regime |
| Infrastructure | N/A |
| Capabilities | Advanced wipers and malware capable of compromising industrial systems, physical destruction of industrial equipment, mass data deletion, disruption of infrastructure and telecommunications operations |
The group demonstrates advanced technical capabilities that suggest access to significant resources, in-depth knowledge of Iranian industrial systems, as well as the ability to develop malware tailored to specific targets specific. Furthermore, it highlights relevant skills in SCADA and ICS (Industrial Control Systems), used in the control of critical infrastructures. Compared to most hacktivists who intervene on geopolitical or current affairs issues, Predatory Sparrow stands out for its significantly superior technical know-how, which is typical of actors connected to state apparatuses.
Industrial Control Systems (ICS/SCADA)
Payment Systems
Critical Infrastructure
Based on currently available information, the group is believed to be in possession of variants of the “Meteor” wiper, first appeared in 2021 and was used by a threat actor named “Indra” against Syrian infrastructure. This could indicate a partial overlap between the two threat actors.
The “Meteor” strain includes several versions, known as “Stardust” and “Comet”, both with wiper functionality. “Chaplin” instead turns out to be the malware used in the attack on the Iranian steel mills, not equipped with data deletion capabilities but with the ability to compromise and control industrial systems.
Meteor Express is a three-stage wiper malware, developed through a combination of open source components and legacy software. The code is highly modular and designed for destructive operations targeting strategic infrastructure.
Main Features
Related MITER ATT&CK techniques
wiper malware similar to Meteor but without provocative payloads. Three-stage architecture, with mixed code between open and legacy components.
Main features
Related MITER ATT&CK techniques
Wiper destructive weapon used in targeted attacks against Syrian targets. Similar to Comet, but specifically oriented towards the systematic destruction of sensitive data.
Main features
Related MITER ATT&CK techniques
Evolution of the Meteor malware, classifiable as disruptive malware. It lacks the wipe component, but introduces visually provocative actions.
Main features
Kill Chain
Related MITER ATT&CK techniques
Date: October 2021
Target: Over 4,000 gas stations in Iran (fuel distribution system)
Attack Method: Point-of-Sale Systems Compromised
Impact:
MITRE ATT&CK TTPs:
Malware/Toolset: Unknown
Attribution: Predatory Sparrow
Strategic Impact: Disruption of essential services to increase internal pressure
Date: June 2022
Target: Three major Iranian steel mills (Khouzestan, Mobarakeh, HOSCO)
Attack method: Chaplin malware + manipulation of industrial control systems (ICS)
Impact:
MITRE ATT&CK TTPs:
Malware/Toolset: Chaplin
Attribution: Predatory Sparrow
Strategic Impact: Critical Industrial Capabilities Damaged and Offensive Capabilities Demonstrated Against ICS

Figure 1 – Surveillance Camera
Date: October 2023
Context: Israeli-Palestinian conflict
Message: “Think this is scary? We’re back.”
Target: New attacks on gas stations in Iran
Attack method: Continuation of disruption strategy towards civilian infrastructure
Impact: Not specified in detail but consistent with previous attacks
MITRE ATT&CK TTPs: Presumably similar to October 2021 event
Attribution: Predatory Sparrow
Strategic Impact: Political signal and cyber retaliation in geopolitical terms
Date: June 17, 2025
Target: Bank Sepah – one of the oldest public financial institutions in Iran
Attack method: Destructive cyber attacks with probable use of wipers (e.g. Comet/Stardust)
Impact:
MITRE ATT&CK TTPs:
Malware/Toolset: Alleged wiper variant similar to Meteor / Comet / Stardust
Attribution: Predatory Sparrow (evidence on Telegram + X)
Strategic Impact: Destabilization of the national banking system and loss of confidence in the Iranian government’s ability to protect financial data
At the moment, no details are known about the techniques, tactics and procedures (TTP) used by the threat actor, although the deletion of data and the consequent paralysis of operations suggests that a version of the group’s “proprietary” wipers, such as Meteor, Stardust or Comet, was used. On 16/06, on its Telegram channel the group had released a list of cves that were still working, entitled “cve_poc_codes_export_works”.
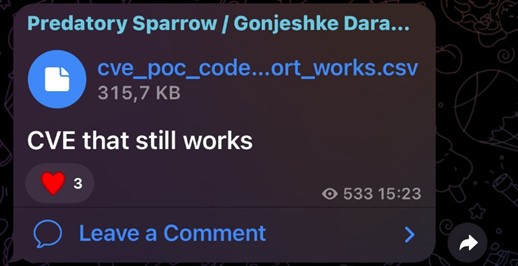
Figure 2 – CVE spread on the Telegram channel of TA
According to sources on X, Iranian citizens were unable to withdraw cash from ATMs in the country.

Figure 3 – Bank teller machine out of service
This factor, combined with fears of theft of sensitive data from the affected banks, contributes to the worsening of the scenario and underlines the cyberwar capabilities possessed by the Threat Actor.

Figure 4 – Bank Sepah Documentation
Unlike many hacktivists, in fact, Predatory Sparrow does not It is limited to a Denial of Service (DoS), but has shown advanced technological capabilities and determination to cause damage on a large scale.
At the moment there is no further information on the status of the services provided by the affected banks, but if these disruptions were to continue, this would represent considerable damage to Iran’s ability to respond to cyber threats and could contribute to generating discontent and tensions among the affected population.
Date: June 18, 2025
Target: Nobitex – Iranian crypto exchange site
Attack method: At the moment there is no information regarding the attack methodology used
Impact:
MITRE ATT&CK TTPs:
Malware/Toolset: Alleged wiper variant similar to Meteor / Comet / Stardust
Attribution: Predatory Sparrow
Strategic Impact: Destabilized Iran’s cryptocurrency exchange system. Severed a funding line that allowed Iran to partially circumvent Western sanctions. Psychological effects such as spreading panic and uncertainty about the resilience of Iranian assets in cyberspace.
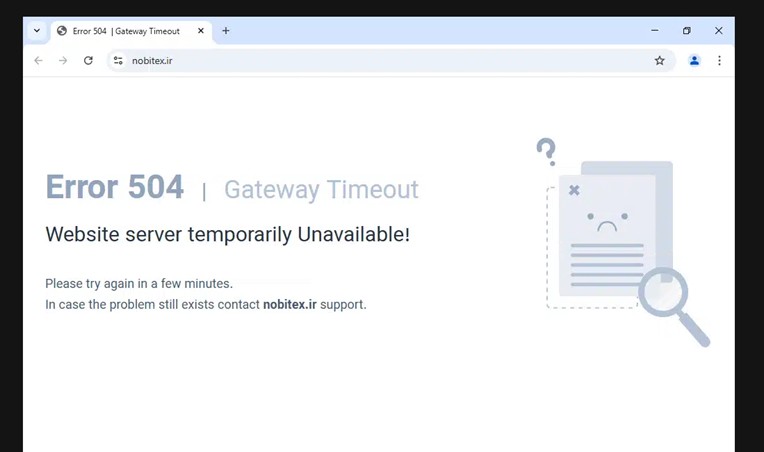
Figure 5 – Nobitex[.]ir still unreachable on 19/06, one day after the attack
Predatory Sparrow attacked the Iranian cryptocurrency exchange “Nobitex” on June 18, just one day after the attack on Sepah Bank. The stated motivation is the same: evading sanctions imposed on Iran and financing terrorism. On X, Predatory Sparrow also highlighted the connection between the regime’s activities and those of Nobitex, stating that, for the Iranian government, service at the cryptocurrency exchange is considered the same as military service.
The Threat Actor did not steal the cryptocurrencies, but effectively burned $90 million of them, sending them to unusable addresses (“burn addresses”), from which they cannot be recovered. The technique used underlines Predatory Sparrow’s goal of causing damage without any monetization or financing purpose, as also implied by the use of wipers.
On 06/20/2025, the threat actor also made the Nobitex source code public, putting the assets still present on the site at risk and making access and exploitation easier for further malicious actors. This source code disclosure amplifies the vulnerability of the system, allowing attackers to quickly identify weaknesses and develop targeted exploits.
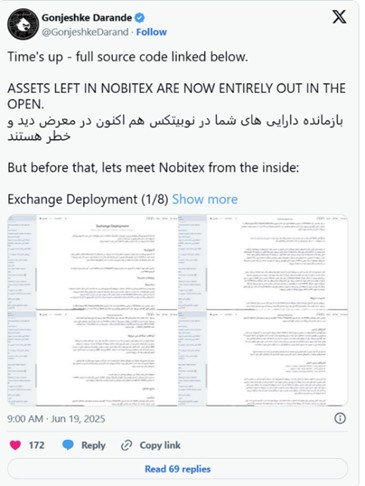
Figure 6 – Post in which Predatory Sparrow makes the Nobitex source code public, https://x.com/GonjeshkeDarand/status/1935593397156270534
There are currently no further details on the techniques, tactics and procedures (TTP) used by the threat actor in this operation.
Based on the evidence presented in the report, some recommendations and countermeasures are formulated to minimize or contain damages coming from the actor described here or from any emulator groups.
Considering the lack of detailed information on the compromises, in the face of the failure to disclose by the affected Iranian entities, some general considerations are presented here aimed at reducing the impact of “wiper” malware such as Meteor and other tools used in cyber warfare and cyber-espionage contexts such as InfoStealer and SpyWare. Furthermore, considering the presence of a list of CVEs with the related links to the Proof of Concept published directly by the Threat Actor on its Telegram channel, where it is highlighted that these are still working exploits, it can be assumed that Predatory Sparrow also uses exposed and vulnerable applications as an initial access vector, therefore recommendations will be suggested to protect the exposed attack surface.
In order to contain the propagation of a wiper within the network, it is advisable to adapt a rigid segmentation, which separates OT networks from IT, also through the use of Zero Trust architectures and strict access control.
At the same time, the separate, air-gapped backup, associated with recovery and disaster recovery plans, allows the recovery of normal operations in the event of a compromise.
Patching, closing unnecessary ports exposed to the Internet and disabling unnecessary services are also useful measures to reduce the attack surface and minimize the risk arising from exposed applications.
Honeypot ICS/SCADA also allows you to detect anomalies and intrusions before malicious actors reach areas critical to industrial operations.
| Threat or vector | Key countermeasure | Expected impact |
| Meteor malware (strain) | Network isolation OT, presence of EDR, immutable backups stored offline | Reduction of sabotage risk, containment of infection, recovery in case of attack |
| C2 communication | Firewalling and deep packet inspection | C2 communication interruption |
| Social Engineering | Staff training, awareness culture and cyber hygiene | Reduction of risk associated with phishing |
| Exploit Public-Facing Application | Patch management, secure configuration, least privilege policy, WAF implementation, disabling unnecessary services, | Reduction of the attack surface, reduction of exploitable vulnerabilities, reduction of the risk of unauthorized access authorized. |
| InfoStealer, SpyWare, cyber espionage tools | EDR, Network Segmentation, Vulnerability Patching, Access Control Policies, Data Encryption, DLP, Deception Honeypot Deployment | Reducing the Risk of Sensitive Data Exfiltration |
Last Updated: June 20, 2025
Primary Sources and Databases
Analysis and Reporting Articles
Follow us on Google News to receive daily updates on cybersecurity. Contact us if you would like to report news, insights or content for publication.
