
In the digital age, cybersecurity has become a priority for businesses and individuals. Among the most fearsome threats are cyberattacks, targeted intrusions that can cause significant damage, both financially and to reputation.
In this context, the “cyber kill chain” represents a reference model for defense against cyber threats. It is a proactive approach that analyzes the different phases of a cyber attack, providing a framework for prevention, detection, and response.
Understanding the cyber kill chain is essential not only for attackers, but also for strengthening cybersecurity and protecting against increasingly sophisticated attacks. In this article, we’ll explore the different stages of the kill chain in detail, providing useful information for implementing it in real-world contexts.
Adopting the cyber kill chain offers a number of significant advantages in the context of cyber defense. First, this approach provides organizations with a clear understanding of the stages through which a cyber attack develops. This understanding allows companies to identify and analyze vulnerabilities in their infrastructure and processes, enabling them to take targeted preventative measures.
Furthermore, the cyber kill chain helps make incident detection and response strategies more effective, enabling security teams to quickly identify and neutralize threats before they can cause significant damage. Thanks to its organized structure, the cyber kill chain also allows organizations to plan and implement defense strategies more efficiently, optimizing the use of available resources and ensuring better management of cyber risks.
The conceptualization of the “kill chain” in the military context dates back to the 1980s, when the United States Air Force introduced the concept to describe the process by which a fighter aircraft detects, engages, and destroys an enemy target. This concept was later adapted and applied to the field of cybersecurity, giving rise to the cyber kill chain. However, it is important to note that the concept of the kill chain in the cyber context has been further developed and refined over the years by various organizations and security experts.
Lockheed Martin was one of the first companies to formalize the concept of the cyber kill chain in the context of cybersecurity. In 2011, it introduced its version of the cyber kill chain, which identifies seven distinctive phases through which a cyber attack develops. This model provided organizations with a clear and structured framework for understanding and countering cyberattacks.
In subsequent years, other organizations and cybersecurity vendors developed their own variations of the cyber kill chain, adapting it to industry-specific needs and emerging threats. For example, the MITRE Corporation introduced the ATT&CK (Adversarial Tactics, Techniques, and Common Knowledge) framework, which provides a detailed mapping of the actions and techniques used by attackers during a cyberattack.
Today, the cyber kill chain has become one of the fundamental concepts in cybersecurity, used by organizations around the world to improve their ability to defend against cyber threats. Its evolution over the years has been driven by the relentless advancement of technology and the growing complexity of the cyber threat landscape, and it continues to be a valuable resource for organizations committed to protecting their systems and sensitive data.
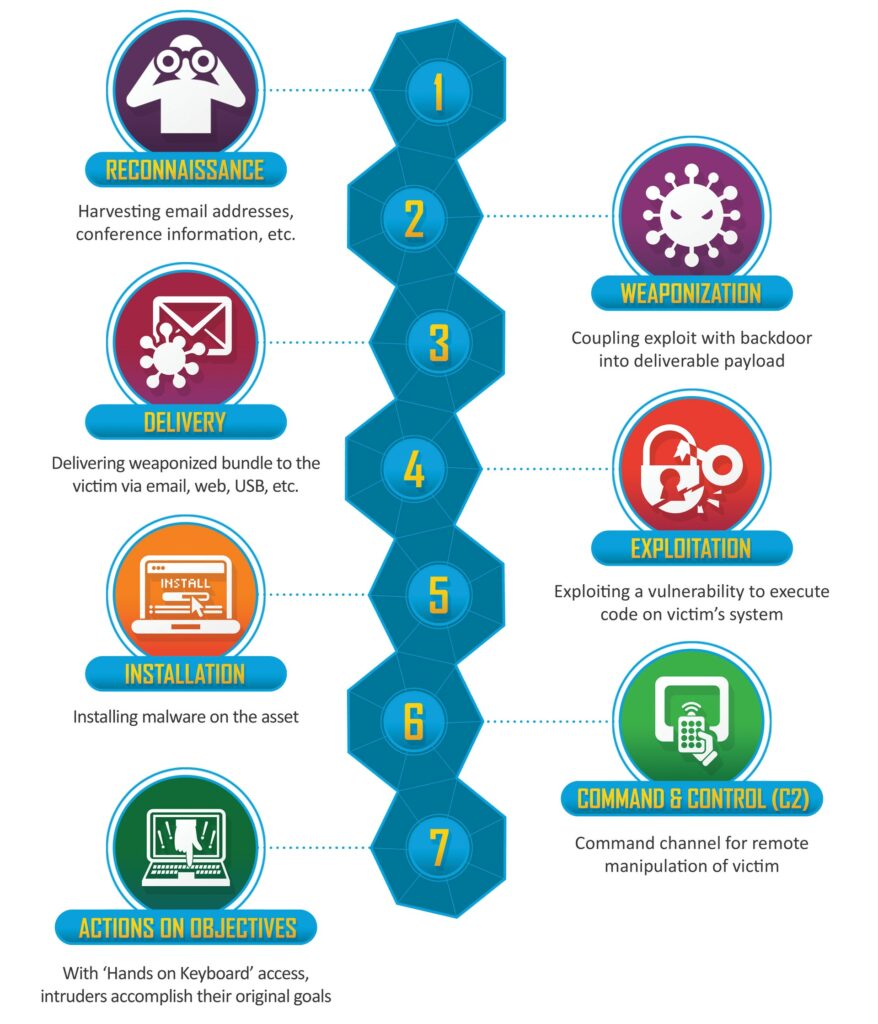
The cyber kill chain represents an essential conceptual model for understanding the lifecycle of a cyber attack, from its initial planning phase to its execution and final impact on the target. This model divides the cyber attack process into several distinctive phases, each of which plays a critical role in the overall effectiveness of the attacker’s operation. Understanding these phases is essential for developing effective cyber defense strategies and protecting networks and systems from increasingly sophisticated and pervasive threats.
Within the cyber kill chain, the main phases can be summarized as follows:
Each stage of the cyber kill chain represents a crucial step in the cyber attack process and offers unique opportunities for defense and threat mitigation. In the next chapter, we’ll understand that each of these phases brings with it the possibility of defining and implementing strong mitigations.
To effectively counter each phase of the cyber kill chain, organizations must adopt a combination of technological, procedural, and human security measures. For example, to counter the reconnaissance phase, it is essential to implement appropriate access controls, limit publicly available sensitive information, and provide security awareness training to employees to prevent social engineering.
For the weaponization phase, for example, organizations should use advanced security solutions such as firewalls, antivirus, and intrusion detection systems to identify and neutralize malware before it can execute. In the delivery phase, it is essential to adopt spam filters and email security solutions to block phishing messages and detect malicious content.
Furthermore, for the subsequent stages of the cyber kill chain, such as exploitation, installation, and command and control, organizations should implement security measures such as regular patching to correct vulnerabilities, network segmentation to limit the propagation of attacks, and the implementation of advanced threat detection solutions to identify suspicious activity and anomalous behavior within the system.
Overall, effective defense against the cyber kill chain requires a holistic, multi-layered approach that combines advanced security technologies, robust processes, and ongoing staff training to mitigate cyber threats at all stages.
The cyber kill chain has proven to be a valuable tool in cybersecurity, providing organizations with a structured framework for understanding, preventing, and responding to cyberattacks. By analyzing the different stages of the attack process, organizations can identify vulnerabilities within their systems and develop targeted defense strategies to mitigate risks.
However, it is important to recognize that the cyber kill chain is only one of the tools available to organizations to protect their data and infrastructure. Cyber threats are constantly evolving, and attackers are constantly adapting their tactics and techniques to evade defenses. Therefore, it is crucial for organizations to adopt a proactive, multi-layered approach to cybersecurity, integrating the cyber kill chain with other advanced defense methodologies and technologies.
Furthermore, collaboration and information exchange between organizations, both in the public and private sectors, as we often report on these pages, are crucial to effectively addressing cyber threats. Sharing threat intelligence and adopting common standards and best practices help strengthen collective defenses and improve the resilience of the cybersecurity landscape as a whole.
In conclusion, the cyber kill chain remains an essential tool for understanding and countering cyberattacks, but it is only one element of a comprehensive cyber defense strategy. Investing in human resources, advanced security technologies, and collaboration between organizations are key to successfully addressing cybersecurity challenges in today’s increasingly complex and interconnected digital world.
Follow us on Google News to receive daily updates on cybersecurity. Contact us if you would like to report news, insights or content for publication.
