
Si fa un gran parlare da qualche anno a questa parte di deep web e dark web e molti si sono chiesti: ma cosa si intende precisamente?
Il dark web è spesso associando ad attività losche e criminose che vengono svolte o transitano su Internet. Questo non è sempre vero, ma per poter comprendere come entrare nel dark web, dobbiamo prima conoscerlo e comprendere la sua storia e le sue motivazioni.
In questo articolo comprenderemo a fondo cosa è il deep web e il dark web e poi spiegheremo come poter accedere in sicurezza a quest’ultimo.
Siamo un po’ tutti abituati a iniziare le nostre navigazioni Internet partendo dal motore di ricerca. A prescindere da quale sia il preferito, il funzionamento è sempre più o meno lo stesso: noi poniamo una domanda (sotto forma di chiave di ricerca) e il portale ci risponde esponendoci una serie di risultati che secondo lui possono essere afferenti a quanto stiamo cercando. Ma vi siete mai chiesti cosa c’è oltre quei risultati che il motore ci propone?
Ovviamente, Internet non inizia e finisce in quei suggerimenti ma c’è molto, molto di più. Basti pensare che si calcola che Google, che è il motore di ricerca più potente e più usato, è in grado di indicizzare (e quindi rivelare) meno dell’un per cento di tutto il contenuto del web mondiale. Tutto quello che Google non vede, quindi, non è inesistente: è semplicemente invisibile, spesso intenzionalmente.
Ne parlammo anche diverso tempo fa con un video sul canale YouTube di RedHotCyber, ma oggi vogliamo raccontarvi, oltre cosa è il Deep Web, anche come accedervi in sicurezza.
Prima di addentrarci e spiegare quello che si intende come Dark web e le Darknet, dobbiamo ricordare che tale termine prende vita nell’era di Arpanet, precisamente nel 1970, per identificare tutte quelle reti parallele alla rete Arpanet, oggi internet, che non potevano essere indicizzate dai motori di ricerca e che quindi risultavano nascoste e non di dominio pubblico.

Internet infatti, si divide in 3 livelli di profondità, e questa rappresentazione spesso viene rappresentata come un Iceberg alla deriva, che possiamo classificare nel seguente modo:
Ritornando quindi al concetto di iceberg: la punta, quella che emerge dall’acqua e sappiamo essere la parte visibile ma di minore dimensione, è il normale web “in chiaro” o “clear web”, che tutti noi possiamo raggiungere con una connessione senza particolari requisiti e che interroghiamo attraverso i motori di ricerca. Si parla quindi di pagine “indicizzate”.
Appena sotto il pelo dell’acqua c’è una parte di web che non si vede, che è appunto il deep web: si tratta di siti molto spesso perfettamente legittimi ma che per le loro peculiarità di realizzazione e contenuto non vengono catturati dai motori di ricerca, si dicono quindi “non indicizzati”. Come abbiamo detto, rientrano in questo caso le intranet aziendali, i sistemi delle reti private delle aziende e delle università, i nuovi siti web che ancora non sono indicizzati dai motori di ricerca.
Ovviamente tra questi ci sono anche i siti il cui contenuto è considerato illegale e per questo escluso dai risultati di ricerca del motore, oppure risorse che non vogliono essere indicizzate dai legittimi proprietari, ma in questo ultimo caso, basta conoscerne l’indirizzo e questi siti sono normalmente accessibili, senza accorgimenti particolari.
Il deep web, in definitiva, è l’internet che sfugge a Google e soci per scelta o limitazione tecnica. Può voler dire che c’è qualcosa da nascondere, ma non necessariamente.
L’ultima parte dell’iceberg, la più inaccessibile, è il dark web. I contenuti che viaggiano sul dark web, oltre a non essere indicizzati dai normali motori di ricerca, non possono nemmeno essere raggiunti direttamente conoscendone gli indirizzi. Per potervi accedere è necessario passare attraverso dei programmi che fanno da “ponte” tra l’internet in chiaro e il dark web.
Attraverso questi ponti si accede a delle reti particolari dette darknet, dove la più famosa è la rete Onion accessibile con il Browser Tor, su cui si trovano i siti del dark web.
Quando si parla di siti illegali è essenzialmente al dark web che ci si sta riferendo. È qui che avviene ogni tipo di compravendita (dalla droga, alle armi, fino ad arrivare ad esseri umani o organi), in maniera totalmente anonima pagando in bitcoin. Quando si parla di dark web si cita spesso l’emblematico caso SilkRoad. SilkRoad era un forum sul dark web in cui si poteva comprare veramente di tutto, tanto da essersi guadagnato il soprannome di “Amazon della droga”.
La sua proprietà fu fatta risalire al nickname Dread Pirate Roberts e l’FBI arrestò la persona che si riteneva operasse dietro questo pseudonimo. Poco tempo dopo, Dread Pirate Roberts ricomparve, facendo pensare che le identità a capo di Silk Road fossero più di una.
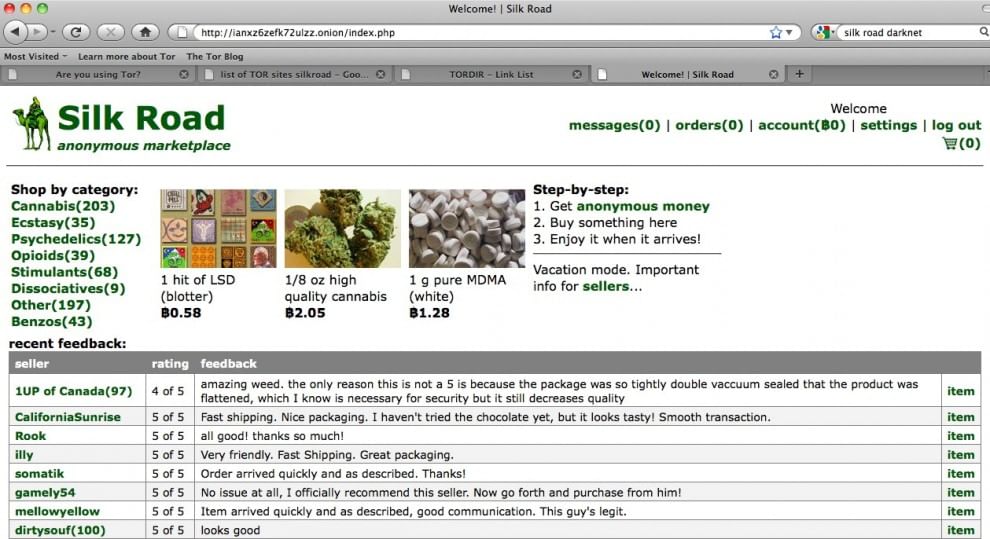
Come si presentava la home page di Silk Road
L’ultimo “pirata” fu identificato con Ross Ulbricht, un brillante studente universitario texano. In qualità di capo di SilkRoad, Ulbricht si era convinto di essere al di sopra della legge e di poter restare impunito. In più, sfruttava la sua popolarità per teorizzare un nuovo sistema economico e sociale più libero e privo di violenza e aggressività facendo proselitismo tra gli utenti. La sua identità però venne scoperta e alcuni degli stessi utenti iniziarono a ricattarlo minacciando di divulgarla. L’FBI riuscì ad arrestarlo quando provò ad assoldare dei killer per uccidere i suoi ricattatori, fu poi processato e condannato all’ergastolo.
Le darknet che costituiscono il dark web includono piccole reti peer-to-peer, friend-to-friend, nonché reti grandi e popolari come Tor, Freenet, I2P (Invisible Internet Project) e Riffle, gestite da organizzazioni e individui pubblici. Gli utenti del dark web si riferiscono al web normale come “Clearnet” a causa della sua natura non crittografata. Il dark web di Tor o onion land utilizza la tecnica di anonimizzazione del traffico con il codidetto onion routing, sotto il suffisso di dominio di primo livello della rete “.onion”.
Onion routing – routing a cipolla – è una tecnica per la comunicazione anonima su una rete di computer. In una rete onion, i messaggi sono “incapsulati” in livelli di crittografia, da pensare come analoghi agli strati di una cipolla. I dati crittografati vengono trasmessi attraverso una serie di nodi di rete chiamati Onion routers (i router della cipolla), ognuno dei quali “si stacca” da un singolo livello, scoprendo la destinazione successiva dei dati. Quando il livello finale viene decifrato, il messaggio arriva a destinazione. Il mittente rimane anonimo perché ogni intermediario (ogni nodo intermedio) conosce solo la posizione dei nodi immediatamente precedenti e successivi ad esso. Sebbene lo onion routing fornisca un alto livello di sicurezza e anonimato, esistono metodi per rompere l’anonimato di questa tecnica, uno di essi è la “timing analysis”.
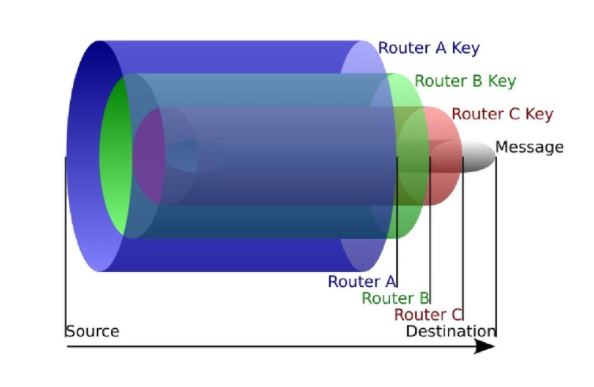
Modello di anonimizzazione della rete Onion.
Si può scegliere di utilizzare il dark web per accedere a servizi e pagine a cui non si può accedere utilizzando i browser standard. Un motivo per utilizzare il dark web potrebbe essere quello di mantenere l’anonimato e ci sono molte ragioni per cui si potrebbe voler mantenere privata la propria identità online. Una di queste potrebbe essere perché si vuole esercitare il proprio diritto alla libertà di parola e il governo in cui si risiede non lo consente. La censura politica ed il bavaglio dei media sono tra i motivi per cui le persone cercano di utilizzare il dark web; il dark web è usato infatti anche per attività di WHISTLEBLOWING in forma anonima.
Infine, il dark web viene utilizzato per traffici illegali come la vendita di farmaci da prescrizione, droghe proibite come la cocaina e sostanze chimiche tossiche; i criminali usano il dark web anche per vendere armi legali e non. Proprio come le “altre sfere” del web, l’utilizzo del dark web può essere pericoloso, vediamo quindi delle precauzioni per proteggersi quando si “visita” il dark web.
Abbiamo parlato di routing onion (cipolla) – Il routing garlic (aglio) è una variante del routing onion che crittografa più messaggi insieme per rendere più difficile per gli aggressori eseguire analisi del traffico e aumenta la velocità di trasferimento dei dati.
Michael J. Freedman della Princeton University ha definito “garlic routing” come un’estensione del routing onion, in cui più messaggi sono raggruppati insieme. Ha chiamato ogni messaggio un “bulbo”, mentre I2P li chiama “spicchi d’aglio”. Tutti i messaggi, ciascuno con le proprie istruzioni di consegna, sono esposti all’endpoint. Ciò consente il raggruppamento efficiente di un “blocco di risposta” di routing onion con il messaggio originale.
Il “routing dell’aglio” è uno dei fattori chiave che distingue I2P da Tor e da altre reti di privacy o crittografia.
Per avere la massima protezione per entrare nel dark web, si deve utilizzare una rete privata virtuale (Virtual Private network), ovvero: “una rete che aiuta a proteggere i tuoi dati e a mantenere riservate le tue informazioni online”.
Quando si utilizza il browser Tor, è comunque possibile che il proprio traffico online venga monitorato. Finché l’ “altra parte” (lo spione) ha abbastanza tempo a disposizione, risorse sufficienti e le giuste competenze, può facilmente risalire a voi dalla vostra attività online.
Potrebbe persino essere divulgato il vostro indirizzo IP, il che può essere molto dannoso. Facendo funzionare una VPN in background mentre si utilizza il browser Tor, questi problemi sono evitabili. Poiché la vostra VPN crittografa il traffico, mantiene anche il vostro indirizzo IP nascosto in modo sicuro dalla sorveglianza del governo e dagli hacker anche nel caso ci fosse un data leak relativo alla traffico sulla rete Tor.
Prendere in considerazione il pagamento per un servizio di rete privata virtuale. I servizi gratuiti di VPN, spesso guadagnano esponendovi ad annunci pubblicitari e vendendo i vostri dati sensibili. E’ anche vero per una VPN a pagamento in quanto il rischio zero non esiste, ma sicuramente partiamo più avvantaggiati a nostro favore.
Infatti, una VPN gratuita non è mai veramente gratuita …. e con hacker e truffatori che si infiltrano ogni giorno nei nodi Tor, il dark web non è il posto giusto per rischiare.
Un elenco di possibili scelte:
NordVPN a quanto pare è la migliore VPN per Tor. Tale servizio ha una funzione inconfondibile: Onion over VPN. Ha tutti i vantaggi di un router Onion (Tor) combinato con la sicurezza aggiuntiva di un tunnel VPN. Questo metodo di connessione garantisce la protezione contro l’accesso non autorizzato da parte del internet provider o delle autorità. Il vostro ISP potrebbe visualizzare che state utilizzando Onion, senza rendersene conto. NordVPN vi protegge da tutte le terze parti e non monitora la vostra attività online: utilizzerete Internet in totale privacy. NordVPN è facile da usare, veloce e offre molti server in tutto il mondo.
Con sede a Panama e con una politica di no-log verificata, Nord è una buona scelta per molte ragioni. Grazie a NordLynx (basato su WireGuard), è la VPN più veloce in circolazione e offre una buona gamma di funzionalità tra cui lo split tunneling su Android e Windows.
ExpressVPN ha i propri server DNS che garantiscono la vostra privacy. Tale servizio non registra mai il vostro traffico Internet, quindi nessuno sarà in grado di identificarvi attraverso indirizzo IP o marca temporale. Nel momento quando effettuate dei pagamenti online, ExpressVPN vi aiuta a mantenere l’anonimato completo. Il servizio non fornisce le vostre informazioni a nessuna fonte governativa e non memorizza i registri del traffico in modo che i vostri dati non finiscono nelle mani sbagliate. Tutto ciò rende ExpressVPN una delle migliori VPN per il browser Tor.
CyberGhost VPN fornisce protezione contro le perdite DNS e il blocco di emergenza delle connessioni. Tutti i dati vengono crittografati utilizzando il protocollo di AES-256. CyberGhost VPN nasconde in modo affidabile il vostro indirizzo IP e rende anonimo il traffico Internet in uscita. Ciò che rende questo provider una delle migliori VPN per il Deep Web è il suo server NoSpy. Solo gli specialisti di CyberGhost hanno accesso ai server NoSpy, possono controllare e gestire tali server. Aiuta a ridurre significativamente i rischi di accesso esterno e di interferenza da parte di individui.
Surfshark ha un’interfaccia chiara e semplice e una ampia gamma di funzioni. Ha app ed estensioni che proteggono i dispositivi e i browser Web più diffusi e costa meno della maggior parte dei suoi concorrenti, nonostante consenta un numero illimitato di connessioni.
Con sede nelle Isole Vergini britanniche con una rigorosa politica di non registrazione e server MultiHop per una maggiore sicurezza e privacy, è un’ottima scelta, anche per navigazione in dark nets.
Un possibile criterio di scelta potrebbe essere la possibilità di usare una VPN con il protocollo WireGuard.
WireGuard è un protocollo di comunicazione e un software gratuito open source che implementa reti private virtuali (VPN) crittografate ed è stato progettato con gli obiettivi di facilità d’uso, prestazioni ad alta velocità e bassa superficie di attacco. Il suo scopo è garantire prestazioni migliori e un maggiore risparmio energetico rispetto ai protocolli di tunneling classici delle VPN (IPsec e OpenVPN). Il protocollo WireGuard passa il traffico su UDP.
Il protocollo WireGuard utilizza quanto segue:
Il software dannoso si trova ovunque, anche nel dark web. Un ottimo modo per garantire la vostra sicurezza durante la navigazione online è installare un programma anti-malware ed un antivirus, da tenere costantemente aggiornati. Evitare comunque di effettuare download di files o download tipo Torrent.
Si deve avere un browser dedicato se intendi utilizzare il dark web (Tor browser per siti .onion). L’utilizzo di TOR browser è molto simile all’utilizzo del browser standard, ma la differenza è che permette di raggiungere i siti Web esistenti nel dark web. Durante l’utilizzo del browser, il modo migliore per rimanere al sicuro è divulgare il minor numero possibile di informazioni su di voi.
Astenetevi da ricerche casuali mentre siete online ed evitate di fornire informazioni personali anche quando un sito Web ve lo richieda. Quando notate collegamenti sospetti, non fate clic su di essi: queste misure garantiranno che ci siano pochissime tracce della vostra presenza sul dark web online.
Assicuratevi di mantenere private le vostre informazioni private in ogni momento. Non si può mai essere troppo attenti. Prendere le dovute precauzioni prima e dopo aver aperto il browser Tor vi renderà meno vulnerabile agli hacker. Prima di entrare nel dark web, chiudete tutte le app non essenziali, ad esempio i password manager.
Inoltre, interrompete l’esecuzione dei servizi non necessari sul vostro dispositivo e coprite la webcam con un pezzo di nastro o carta. È prevalente per gli hacker accedere alle webcam degli utenti senza che gli individui nemmeno se ne accorgano. Ricordate anche di disattivare la vostra posizione, in quanto può essere utilizzata per ottenere il vostro indirizzo IP.
I migliori sistemi operativi per TOR … ci si potrebbe chiedere, cosa rende questi sistemi operativi diversi e adatti a TOR? Se volete usare TOR, siete chiaramente attenti alla privacy. Anche se non siete coinvolti in alcuna attività nel DarkWeb, TOR è ancora uno dei modi migliori per navigare sul web oscuro, ma non è sufficiente.
I sistemi operativi elencati di seguito, a differenza di Windows che fondamentalmente è una sorta di “keylogger sys op”, non vi tracciano o vi seguono. In effetti, si impegnano a eliminare tutte le tracce che potreste lasciare sul sistema.
La maggior parte di questi instrada automaticamente il vostro traffico tramite la rete Onion, diventando automaticamente il migliore amico di Tor! Anche questi nella maggior parte dei casi non hanno bisogno di essere “installati”. Piuttosto, possono essere eseguiti da un disco live (dischi USB/CD). Una volta rimosso il dispositivo, vengono rimosse anche tutte le tracce dell’utilizzo del sistema operativo e delle attività svolte.
Questi hanno anche le proprie app rispettose della privacy per la messaggistica, l’invio di e-mail, l’archiviazione di cripto valute e molto altro. Quindi, nel complesso, forniscono un ambiente più sicuro. L’isolamento e la compartimentazione sono alcune delle funzionalità comuni a tutti questi sistemi operativi:
È il momento di registrarsi per un indirizzo email non rintracciabile. Gmail è fuori questione: se avrete bisogno di un indirizzo email ecco alcuni che potreste prendere in considerazione:
Si noti che questi servizi vengono forniti anche con domini .onion, a cui è necessario accedere utilizzando il browser TOR. Si ricorda che browser regolari come Chrome e Firefox non funzionano verso domini .onion.
Di seguito riportiamo una carrellata di tutti i motori di ricerca del dark web che possono essere utilizzati per “orientarsi” nella vastità della superficie.
L’accesso al dark web non è classificato come illegale nella maggior parte degli stati. Tuttavia, avere il possesso di determinate cose e tenere “certi comportamenti” lo è. Stati diversi hanno leggi diverse che regolano l’attività del dark web e dovreste avere familiarità con le vostre leggi statali o federali che disciplinano le attività nel dark web. Familiarizzare con la legge vi consentirà di evitare attività etichettate come illegali.
Internet è una grande risorsa e offre soluzioni a vari problemi e domande. Come tutto il resto, Internet presenta alcuni problemi che puoi facilmente evitare e da cui puoi proteggerti. Avere le conoscenze di cui sopra ti aiuterà a navigare in Internet in sicurezza.
Stay safe, “wear” a VPN with TOR browser.
Punto di estensione/approfondimento
Timing analysis, cos’è e come opporsi ad essa
Best Linux distros for privacy and security in 2021
WireGuard usato su Debian – Raspberry Pi – Android – iOS
Ti è piaciuto questo articolo? Ne stiamo discutendo nella nostra Community su LinkedIn, Facebook e Instagram. Seguici anche su Google News, per ricevere aggiornamenti quotidiani sulla sicurezza informatica o Scrivici se desideri segnalarci notizie, approfondimenti o contributi da pubblicare.

 Innovazione
InnovazioneL’evoluzione dell’Intelligenza Artificiale ha superato una nuova, inquietante frontiera. Se fino a ieri parlavamo di algoritmi confinati dietro uno schermo, oggi ci troviamo di fronte al concetto di “Meatspace Layer”: un’infrastruttura dove le macchine non…
 Cybercrime
CybercrimeNegli ultimi anni, la sicurezza delle reti ha affrontato minacce sempre più sofisticate, capaci di aggirare le difese tradizionali e di penetrare negli strati più profondi delle infrastrutture. Un’analisi recente ha portato alla luce uno…
 Vulnerabilità
VulnerabilitàNegli ultimi tempi, la piattaforma di automazione n8n sta affrontando una serie crescente di bug di sicurezza. n8n è una piattaforma di automazione che trasforma task complessi in operazioni semplici e veloci. Con pochi click…
 Innovazione
InnovazioneArticolo scritto con la collaborazione di Giovanni Pollola. Per anni, “IA a bordo dei satelliti” serviva soprattutto a “ripulire” i dati: meno rumore nelle immagini e nei dati acquisiti attraverso i vari payload multisensoriali, meno…
 Cyber Italia
Cyber ItaliaNegli ultimi giorni è stato segnalato un preoccupante aumento di truffe diffuse tramite WhatsApp dal CERT-AGID. I messaggi arrivano apparentemente da contatti conosciuti e richiedono urgentemente denaro, spesso per emergenze come spese mediche improvvise. La…