
Nell’era digitale, la sicurezza informatica è un tema di grande importanza per qualsiasi azienda che gestisce dati sensibili. Tuttavia, non tutti i rischi sono esterni. Infatti, spesso sono gli stessi dipendenti a rappresentare una minaccia per la sicurezza informatica di una organizzazione.
Si chiamano “impiegati infedeli”. Si tratta di dipendenti dell’azienda che vogliono creare un danno alla stessa, magari avendone un vantaggio e rappresentano una minaccia alla quale le organizzazioni oggi devono fare i conti.
In questo articolo esploreremo chi sono gli impiegati infedeli, quali sono le motivazioni che li spingono, quali sono gli effetti, come le cybergang criminali li arruolano dando uno sguardo alle mitigazioni e al tema psicologico.
Un impiegato infedele è un dipendente che compie azioni illecite ai danni della sicurezza informatica dell’azienda per motivazioni diverse, cosa che vedremo nel prossimo capitolo.
Questi comportamenti possono includere l’accesso non autorizzato ai dati, la copia o la vendita di informazioni riservate, l’installazione di software dannoso e molto altro ancora.
Gli impiegati infedeli rappresentano una minaccia significativa per la sicurezza informatica dell’azienda perché hanno accesso a informazioni riservate e possono utilizzare le proprie conoscenze per aggirare le misure di sicurezza. Inoltre, spesso gli impiegati infedeli sono difficili da individuare perché hanno già autorizzazioni di accesso ai dati stessi.
Tra le motivazioni degli impiegati infedeli ci sono la mancanza di soddisfazione lavorativa, l’ambizione professionale, la ricerca di guadagni extra o la vendetta personale. In alcuni casi, gli impiegati infedeli possono agire per motivi ideologici o politici.
La mancanza di soddisfazione lavorativa può portare i dipendenti a cercare nuove opportunità di lavoro o a sentirsi disillusi nei confronti dell’azienda. In alcuni casi, gli impiegati infedeli possono agire per vendetta, ad esempio in seguito a discriminazioni o ritorsioni nei confronti dei dipendenti.
L’ambizione professionale può portare i dipendenti a cercare di guadagnare denaro extra o di acquisire informazioni riservate per avanzare nella propria carriera professionale. In alcuni casi, gli impiegati infedeli possono anche essere mossi da motivazioni economiche, come il desiderio di vendere informazioni riservate a terzi come i propri clienti o la proprietà intellettuale e quindi vanificare gli sforzi dell’organizzazione.
La vendetta personale è una motivazione comune per gli impiegati infedeli, che possono agire contro l’azienda o i loro superiori in seguito a conflitti interni, discriminazioni o ritorsioni nei confronti dei dipendenti. In alcuni casi, gli impiegati infedeli possono agire per motivi ideologici o politici, ad esempio per sabotare l’azienda o per diffondere informazioni riservate.
Le azioni degli impiegati infedeli possono causare danni finanziari e reputazionali all’azienda, nonché la perdita di dati sensibili e la violazione della privacy dei clienti.
Inoltre, gli effetti delle azioni degli impiegati infedeli possono durare a lungo nel tempo. Ad esempio, la perdita di dati sensibili o la violazione della privacy dei clienti possono avere conseguenze a lungo termine sulla reputazione dell’azienda e sulla sua capacità di mantenere la fiducia dei clienti.
La gestione dei rischi associati alle azioni degli impiegati infedeli è una priorità per qualsiasi azienda che desidera proteggere la propria sicurezza informatica e i propri obiettivi commerciali.
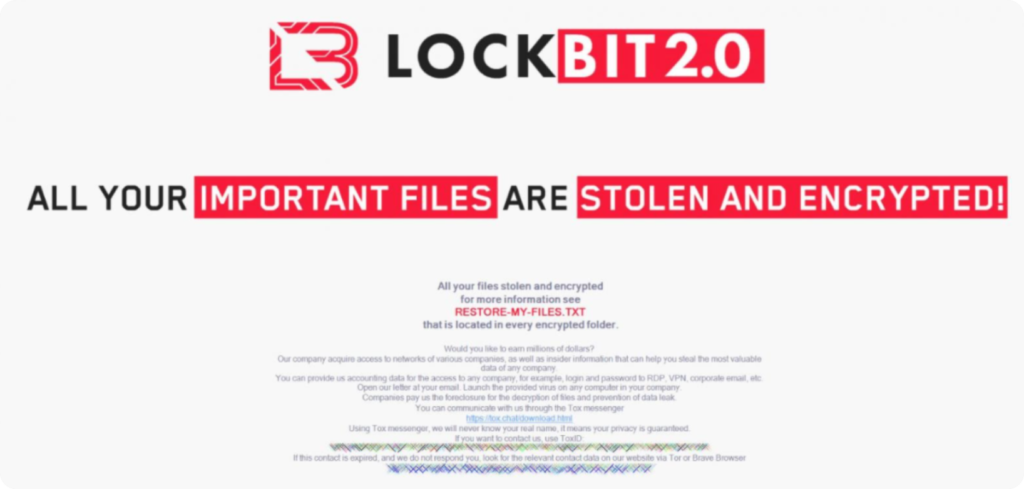
Numerose cybergang, tra cui LockBit e Lapsus, hanno fatto appello agli impiegati infedeli per acquisire informazioni utili per violare i sistemi informatici delle aziende. Questi attaccanti possono tentare di contattare gli impiegati infedeli stessi attraverso canali di comunicazione online o attraverso il loro network di contatti.
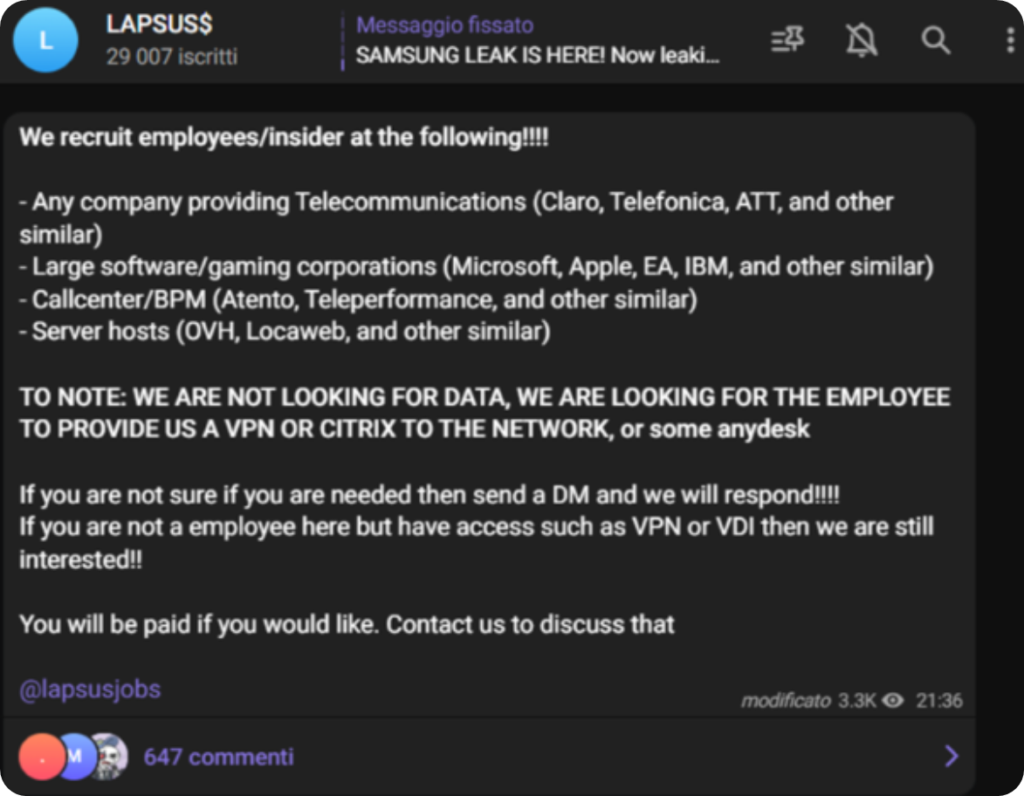
Le motivazioni alla base di questo tipo di reclutamento possono essere varie. Alcune cybergang potrebbero cercare di infiltrarsi nelle aziende per rubare informazioni riservate o per esempio, utilizzare i loro sistemi informatici come parte di una botnet o per estrarre criptovaluta. Altre potrebbero cercare di estorcere denaro o di creare danni ai sistemi informatici delle aziende.
Per prevenire il reclutamento degli impiegati infedeli, le aziende devono adottare politiche di sicurezza solide e formare i propri dipendenti su come riconoscere e segnalare eventuali tentativi di reclutamento istaurando fiducia tra organizzazione e dipendente.
Il comportamento degli impiegati infedeli in ambito di sicurezza informatica è stato oggetto di studio anche dal punto di vista psicologico. Alcuni studiosi hanno cercato di capire quali sono le motivazioni che spingono i dipendenti a tradire la fiducia dell’azienda e mettere a rischio la sicurezza informatica.
Secondo gli esperti, il comportamento degli impiegati infedeli può essere causato da diversi fattori. Uno dei principali è la mancanza di soddisfazione lavorativa, che può portare i dipendenti a cercare nuove opportunità di lavoro o a sentirsi disillusi nei confronti dell’azienda. In alcuni casi, gli impiegati infedeli possono anche essere mossi da motivazioni economiche, come il desiderio di vendere informazioni riservate a terzi o di chiedere un riscatto in cambio del ripristino dei dati.
Inoltre, i dipendenti possono essere vittime di attacchi di social engineering, in cui i criminali cercano di convincerli a rivelare informazioni riservate o ad eseguire azioni dannose per l’azienda. Questi attacchi possono essere particolarmente efficaci se i dipendenti non sono adeguatamente formati sulla sicurezza informatica.
In ogni caso, è importante che le aziende comprendano il comportamento degli impiegati per prevenire eventuali incidenti di sicurezza informatica. Le aziende dovrebbero adottare politiche e procedure di sicurezza informatica solide e formare adeguatamente i dipendenti sulla sicurezza informatica. Inoltre, le aziende dovrebbero monitorare costantemente l’attività dei dipendenti sui sistemi informatici dell’azienda per identificare eventuali comportamenti sospetti.
Le aziende devono fare i conti con il rischio che i loro dipendenti si comportino in modo infedele e mettano a rischio la sicurezza informatica dell’azienda. Ma esistono tecniche che le aziende possono utilizzare per prevenire e ridurre questo rischio.
La prima tecnica è quella di implementare politiche di sicurezza solide. Queste politiche dovrebbero includere procedure di accesso e autenticazione, politiche di password forti, sistemi di monitoraggio dei dati e procedure per la gestione delle credenziali dei dipendenti.
In secondo luogo, la formazione dei dipendenti è fondamentale per garantire che tutti i dipendenti siano consapevoli delle politiche di sicurezza dell’azienda e siano in grado di identificare e segnalare eventuali comportamenti infedeli.
In terzo luogo, l’azienda deve monitorare costantemente l’attività dei dipendenti sui sistemi informatici dell’azienda per identificare eventuali comportamenti sospetti. Questo può essere fatto utilizzando sistemi di monitoraggio e di logging delle attività.
In quarto luogo, le aziende dovrebbero limitare l’accesso ai dati sensibili solo ai dipendenti che ne hanno bisogno per svolgere il proprio lavoro (need to know). In questo modo, si riduce il rischio che i dati finiscano nelle mani sbagliate.
Infine, l’azienda dovrebbe implementare una serie di tecnologie per prevenire comportamenti infedeli da parte dei dipendenti. Queste includono la crittografia dei dati, l’implementazione di sistemi di autenticazione a due fattori e l’utilizzo di strumenti di controllo delle attività dei dipendenti. In questo modo, le aziende possono ridurre il rischio di comportamenti infedeli da parte dei dipendenti e migliorare la sicurezza informatica complessiva dell’azienda.
Gli impiegati infedeli, come abbiamo visto, rappresentano una minaccia per la sicurezza informatica delle aziende e possono causare danni significativi. Per prevenire questi incidenti, è importante che le aziende adottino politiche e procedure di sicurezza informatica solide e che formino adeguatamente i dipendenti sulla sicurezza informatica.
Tuttavia, oltre alle misure tecniche di sicurezza informatica, è anche importante instaurare un clima di fiducia tra l’organizzazione e i dipendenti. Gli impiegati infedeli spesso agiscono in seguito a sentimenti di insoddisfazione, frustrazione o rancore, che possono essere evitati attraverso un ambiente di lavoro positivo e una comunicazione aperta tra l’azienda e i dipendenti.
Inoltre, le aziende dovrebbero prevedere canali di segnalazione anonimi per segnalare eventuali comportamenti sospetti o violazioni della sicurezza informatica, in modo da consentire ai dipendenti di segnalare potenziali problemi senza paura di ritorsioni.
In sintesi, la prevenzione degli incidenti di sicurezza informatica causati dagli impiegati infedeli richiede un approccio olistico che includa sia le misure tecniche di sicurezza informatica sia la creazione di un clima di fiducia e collaborazione tra l’azienda e i dipendenti.
Solo attraverso la combinazione di questi fattori è possibile garantire la sicurezza informatica dell’organizzazione e proteggere le informazioni riservate contro le minacce interne.
Ti è piaciuto questo articolo? Ne stiamo discutendo nella nostra Community su LinkedIn, Facebook e Instagram. Seguici anche su Google News, per ricevere aggiornamenti quotidiani sulla sicurezza informatica o Scrivici se desideri segnalarci notizie, approfondimenti o contributi da pubblicare.

 Cybercrime
CybercrimeLe autorità tedesche hanno recentemente lanciato un avviso riguardante una sofisticata campagna di phishing che prende di mira gli utenti di Signal in Germania e nel resto d’Europa. L’attacco si concentra su profili specifici, tra…
 Innovazione
InnovazioneL’evoluzione dell’Intelligenza Artificiale ha superato una nuova, inquietante frontiera. Se fino a ieri parlavamo di algoritmi confinati dietro uno schermo, oggi ci troviamo di fronte al concetto di “Meatspace Layer”: un’infrastruttura dove le macchine non…
 Cybercrime
CybercrimeNegli ultimi anni, la sicurezza delle reti ha affrontato minacce sempre più sofisticate, capaci di aggirare le difese tradizionali e di penetrare negli strati più profondi delle infrastrutture. Un’analisi recente ha portato alla luce uno…
 Vulnerabilità
VulnerabilitàNegli ultimi tempi, la piattaforma di automazione n8n sta affrontando una serie crescente di bug di sicurezza. n8n è una piattaforma di automazione che trasforma task complessi in operazioni semplici e veloci. Con pochi click…
 Innovazione
InnovazioneArticolo scritto con la collaborazione di Giovanni Pollola. Per anni, “IA a bordo dei satelliti” serviva soprattutto a “ripulire” i dati: meno rumore nelle immagini e nei dati acquisiti attraverso i vari payload multisensoriali, meno…