
Uno specialista di Zero Salarium ha presentato un metodo che disabilita temporaneamente i processi antivirus e gli agenti EDR su Windows utilizzando strumenti di sistema integrati.
L’articolo descrive in dettaglio il concetto e lo strumento operativo, EDR-Freeze, un modo per interrompere specificamente i processi di monitoraggio senza installare driver vulnerabili aggiuntivi, basandosi sul comportamento dei componenti nativi del sistema operativo e sulle condizioni di competizione tra i processi.
Il trucco sta nel fatto che MiniDumpWriteDump sospende forzatamente tutti i thread del processo di destinazione durante la creazione di uno snapshot, e il processo associato che attiva il dump è responsabile della sua ripresa. La ricerca dimostra come forzare WerFaultSecure a essere eseguito con privilegi di processo protetto (PPL) a livello WinTCB e avviare un dump del PID desiderato.
WerFaultSecure si sospende quindi in un momento critico. Di conseguenza, il processo di destinazione rimane “in stato comatoso” perché anche l’initiator, che avrebbe potuto sbloccarlo, è bloccato.
Per illustrare questo approccio, l’autore utilizza CreateProcessAsPPL, i parametri di avvio WerFaultSecure, il controllo dello stato del processo e la chiamata a NtSuspendProcess sul processo initiator al momento opportuno. Il meccanismo in sé non richiede exploit di driver di terze parti e funziona in modalità utente, rendendolo comodo per test rapidi e l’escalation delle capacità di bypass del monitoraggio.
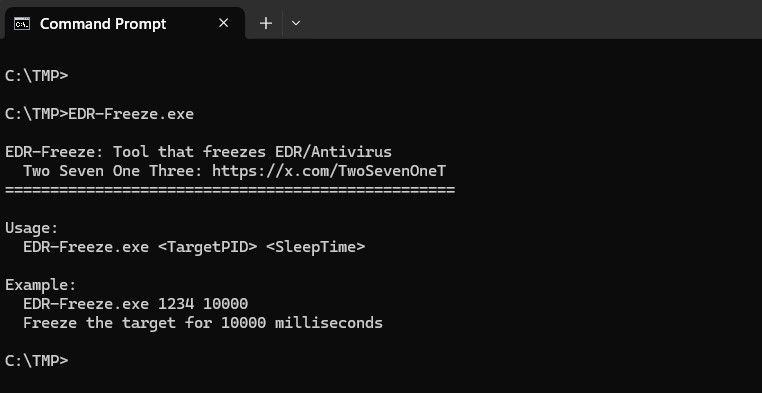
L’articolo descrive lo strumento EDR-Freeze con un repository GitHub ed esempi di runtime: l’utilità accetta il PID del programma di destinazione e il tempo di pausa in millisecondi, quindi esegue quanto descritto e mantiene il processo antivirus sospeso. La dimostrazione dimostra che MsMpEng.exe (un servizio di Windows Defender) su Windows 11 24H2 è stato sospeso con successo per un periodo di tempo specificato e il suo stato monitorato tramite Process Explorer. L’autore sottolinea che questa tecnica funge da alternativa agli approcci BYOVD ed elimina la necessità di trasferire driver vulnerabili al computer di test.
Lo specialista consiglia di monitorare WerFaultSecure per rilevare parametri di avvio anomali: se i suoi argomenti puntano ai PID di servizi sensibili (LSASS, processi antivirus o agenti EDR ), è opportuno indagare. Inoltre, la protezione richiede meccanismi per controllare le catene di avvio dei processi protetti e verificare la presenza di sequenze insolite durante la creazione di dump.
Ti è piaciuto questo articolo? Ne stiamo discutendo nella nostra Community su LinkedIn, Facebook e Instagram. Seguici anche su Google News, per ricevere aggiornamenti quotidiani sulla sicurezza informatica o Scrivici se desideri segnalarci notizie, approfondimenti o contributi da pubblicare.

 Vulnerabilità
VulnerabilitàVenerdì sera l’exchange di criptovalute sudcoreano Bithumb è stato teatro di un incidente operativo che ha rapidamente scosso il mercato locale di Bitcoin, dimostrando quanto anche un singolo errore umano possa avere effetti immediati e…
 Cybercrime
CybercrimeLe autorità tedesche hanno recentemente lanciato un avviso riguardante una sofisticata campagna di phishing che prende di mira gli utenti di Signal in Germania e nel resto d’Europa. L’attacco si concentra su profili specifici, tra…
 Innovazione
InnovazioneL’evoluzione dell’Intelligenza Artificiale ha superato una nuova, inquietante frontiera. Se fino a ieri parlavamo di algoritmi confinati dietro uno schermo, oggi ci troviamo di fronte al concetto di “Meatspace Layer”: un’infrastruttura dove le macchine non…
 Cybercrime
CybercrimeNegli ultimi anni, la sicurezza delle reti ha affrontato minacce sempre più sofisticate, capaci di aggirare le difese tradizionali e di penetrare negli strati più profondi delle infrastrutture. Un’analisi recente ha portato alla luce uno…
 Vulnerabilità
VulnerabilitàNegli ultimi tempi, la piattaforma di automazione n8n sta affrontando una serie crescente di bug di sicurezza. n8n è una piattaforma di automazione che trasforma task complessi in operazioni semplici e veloci. Con pochi click…