Author: Olivia Terragni
Pubblication Date: 13/12/2021
Given that North Korean cyberattacks are not a future threat, but already a FACT, we are already wondering how to deal with the election of the next president of South Korea. To begin the command of the Armed Forces of the Republic of Korea (CFC) and the United States will have to devise a strategy to deter cyber attacks.
The first part of this article can be found here: North Korea’s cyber warfare and its cyber army (part one)
What are the targets? North Korea is capable of deploying advanced technologies, and the main objectives are critical infrastructures: the military force capable of repelling attacks is well established but must be improved and at the same time given the increase in attacks against institutes, organizations government and defense suggests that the next targets – including disinformation and attacks on democratic governance – could be electrical and energy plants, traffic control centers and major government offices.
The human factor remains the weak link in the chain with the absence of an informed leadership instead of Command in the North. This “war” in fact depends precisely on the technical skills of its operators also in the predictive field, where data, transparency and traceability will be important elements.
North Korea, in fact, will use all aspects of the EW to attack the enemy before the shots will be fired on the battlefield.
The cyber army of North Korea
China and North Korea are strengthening their cyber armies in a different way. China is trying to professionalize its “state hacking teams“ for international espionage, through specific schools including a new Wuhan base that is able to train and certify 70,000 people a year in cybersecurity. This makes us think of a future increase in campaigns.

However, while China has started the President Xi’s political goal of reducing corruption in hacking, North Korea is perhaps the only nation in the world known for conducting openly criminal hacking activities for financial gain. Korea training process is very similar to the Russian one, adopted to “hire and train Olympic champions”, except that the Korean Olympics are the ones of mathematics: here they train brains above everything starting from high school to finish at Kim Chaek University of Technology or Kim Il Sung University.
Upon graduation, they are assigned to the General Bureau of Reconnaissance cyberwarfare unit to work as hackers. For all intents, ransomware and cryptocurrency theft aside, North Korea uses keyboards instead of guns.
The most chilling part is taken by the Enemy Collapse Sabotage Bureau responsible for gathering internal information and tactics: ’a name, a promise’, that seems to be able to crush the enemy by pressing a button.
North Korea cyber army – which reports to Bureau 121, Cyber Warfare Guidance Unit – appears to have around 1,000 local experts and another 6,000 recruits (perhaps more at the moment) scattered around the world – Belarus, Malaysia, China and Russia – most in China and Southeast Asia according to Moriuchi, (Recorded Future), who spent years tracking the metadata of North Korean internet users. Here you are Kim Jong Un’s warriors for “a strong and prosperous nation” who are involved in cyber warfare according to the US government report 7-100 US Army Techniques Publication (ATP) 2020.
For all intents and purposes North Korea hackers are part of military forces and they have very specific strategies: surprise preventive attacks, blitzkrieg tactics based on rapid and decisive battles and hybrid warfare, the one that took place between the front and the underground tunnels but which today has become electronic. And not for nothing that this country is popular for having raised – in every sense – specialists in cyber terrorism since the 1990s.
“Cyberwarfare is a multipurpose sword that grants the ruthless strike capability of the North Korean People’s Armed Forces, along with nuclear weapons and missiles”.
Kim Jong-un (2013)

The North Korean Tactics report on the Korean People’s Army (KPA) and its military tactics contains invaluable information on its ability in electronic warfare, while the North Korean Cyber Activity report lists in 2021 the profiles of the actors of the APT threats, the profiles of which have been reported at the end of the article.
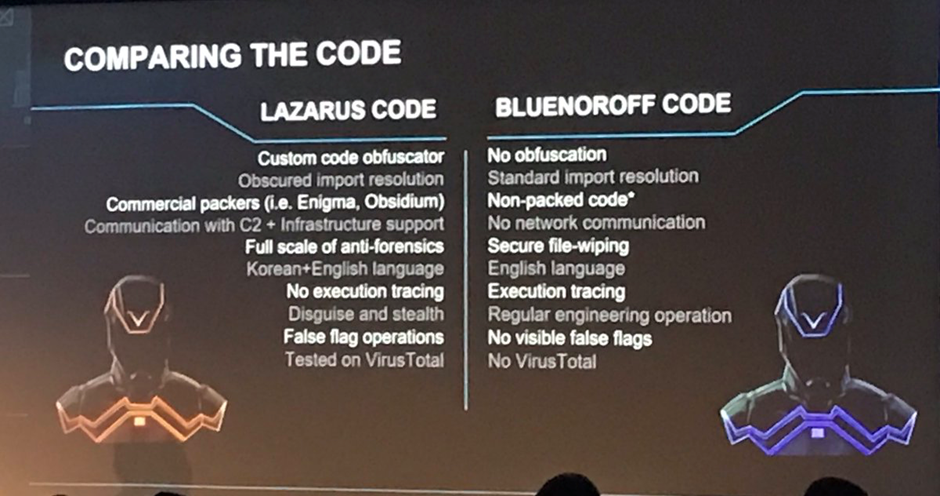
“Regardless of their names, reporting into the insights of the Korean’s People’s Army of the DPRK have connected Lazarus Group, Bluenoroff, and Andariel to the DPRK’s cyber-warfare guidance unit Bureau 121”
Xueyin Peh, senior cyber threat intelligence analyst at Digital Shadows.
Yes, regardless of their names, Lazarus Group, Bluenoroff e Andariel has been connected to the DPRK’s cyber-warfare guidance unit Bureau 121 with 4 principal divisions, three dedicated to cyber warfare and one to electronic warfare:
Since information on North Korean hacker forces is difficult to obtain, determining the role within the nation would be even more difficult. However, it is easy to lead the investigators on a false trail if a scheme is not found by studying methods and tools.
“There is no conclusive evidence that Lazarus is state-sponsored [..] always exhibited the characteristics of a well-resourced and organized cybercriminal or cyber-mercenary collective.” James Scott, a senior fellow at the Institute for Critical Infrastructure Technology, a Washington-based think tank.
Links between Lazarus and North Korea remain unclear, and there is no definitive evidence that it is a state-sponsored group. While it is true that some of the group are working from China, it may include Korean members, FlashPoint analyzed many WannaCry ransom notes – in 28 languages – with Lazarus “fingerprints”- and among its authors it has included Chinese natives who used translation software.
“It is entirely possible that the Lazarus Group is not entirely made up of North Korean actors, but may also have Chinese members.” Jon Condra, director of Asia-Pacific research at cybersecurity firm Flashpoint.
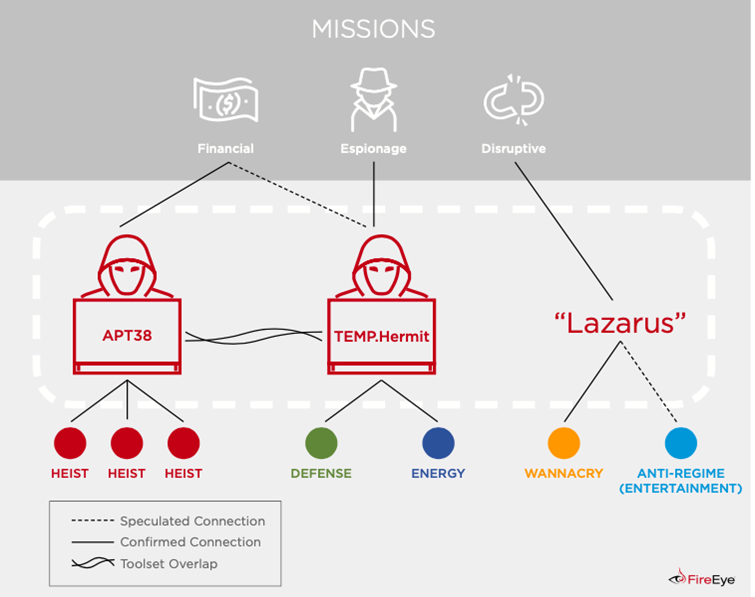
So let’s stay for a moment in China and Southeast Asia where the infamous Lazarus group with its malware factory would be found. Well, what is known about this group is purely speculative. Mercenaries or not, their attack on Sony was contested by North Korea. The FBI itself has argued that its analysis cannot support the direct attribution of a nation-state. This means there is no conclusive evidence.

What is Lazarus? An affiliated group with North Korea, is independent, wholly independent, a secondary operation or an occasional cyber-mercenary collective? Some of his campaigns – as revelas Beau Woods, deputy director of the Cyber Statecraft Initiative at the Atlantic Council – would suggest a less qualified opponent than one might expect from a group that has full state support.
An important trace was found by Kaspersky in 2018, which stated that the level of accuracy of the group, not found in the world of cybercriminals – is “something that requires rigorous organization and control at all stages of the operation”. It is a process that requires a lot of money to continue running the business, which is why the emergence of the Bluenoroff subgroup within Lazarus has its own logic.
Bluenoroff has focused only on financial attacks, placing itself as one of the biggest threats to the banking sector, financial and commercial companies, as well as casinos. To the two groups – as if to form a constellation – is added the Andariel group, sanctioned by the United States Treasury Department in September 2019 for hostile cyber activities on vital infrastructures and accused of having tried to steal bank card data in the past by hacking the branches. to acquire cash or by selling customer data on the black market.
Moreover, the Lazarus group has a relationship with the most sophisticated and resourceful Russian botnet operation in the landscape and it is suspected that it also has ties to Eastern Europe and BAE researchers have discovered that TrickBot operators have communicated with a server controlled by Lazarus only a couple of hours before the same server was used to enter the Chilean interbank network in 2020.Distinguishing and classifying the different groups is quite difficult as they share code, infrastructure and malware with each other, even if each APT group is designed to target a specific sector. The links then regarding Andariel remain obscure.
Returning to Lazarus, it primarily focuses on the governments of South Korea and the United States and the financial organizations of those countries, while Bureau 325 is known for targeting major biotech companies, research institutes, and government entities. The APT38 group focuses primarily on banks, financial institutions and cryptocurrency exchanges: it is an extensive and highly resourceful group, which since 2014 has conducted operations in more than 16 organizations in at least 13 countries, sometimes simultaneously, sharing according to Mandiant , malware codes and other development resources with the North Korean cyber espionage business TEMP.Hermit.

The profiles are reported in the North Korea cyber activity report, published on 25 March 2021 by HHS Cybersecurity program, office for information security.
Suspected attribution: RPDC, Reconnaissance General Bureau
Targets: biotechnology companies, pharmaceutical manufacturers, research institutions, IT companies and government organizations in South Korea, China, and the United States.
Overview: Bureau 121 is considered the cyber warfare guidance unit of the DPRK and coordinates most cyber operations. According to reports thare are over 6,000 members in Bureau 121, and many of them operate in other countries, such as Belarus, China, India, Malaysia, and Russia. There are four subordinate units below Bureau 121: the Andariel Group, The Bluenoroff Group, an Electronic Warfare Jamming Regiment, and the Lazarus Group.
Associated Malware: N/D
Attack vectors: N/A
Suspected attribution: RPDC, Reconnaissance General Bureau
Settori target: principali aziende biotecnologiche, produttori farmaceutici, istituti di ricerca, aziende IT e organizzazioni governative in Corea del Sud, Cina e Stati Uniti.
Targets: major biotechnology companies, pharmaceutical manufacturers, research institutions, IT companies and government organizations in South Korea, China, and the United States.
Overview: established on January 3, 2021 under the Reconnaissance General Bureau (RGB) (Korean: 정찰총국) it receives direct instructions from Kim Jong Un. The group is mainly focused on stealing information on vaccine technology related to COVID-19, and is composed of hackers from various existing DPRK cyber units plus recent grads in IT and computer science. The unit reportedly consists of five teams: with three research institutes overseas (charged with stealing information) and two research centers inside the country (analyzing the hacked data).
Associated Malware: Unknown
Attack vectors: Unknown
Suspected attribution: Democratic People’s Republic of Korea
Targets: Finance, aerospace and defense, manufacturing, healthcare, banking, telecommunications, media.
Overview: the group targeted and compromised a range of victims, some resulting in the exfiltration of data while others have been disruptive in nature. It is probable that actors are likely to continue to use cyber operations to advance their government’s military and strategic objectives. HIDDEN COBRA is known for a campaign of coordinated DDoS attacks on South Korean media, financial, and critical infrastructure in 2011, as well as the Sony Breach in 2014 and various cryptocurrency attacks in 2017. Lazarus doesn’t reveal much about itself and the little known about the group is speculative, but the analysis reveals a chilling – in some ways fascinating – image of a group of tenacious mercenaries
Associated Malware: Copperhedge, Taintedscribe, Pebbledash, Destover, Wild Positron/Duzer, Hangman, DeltaCharlie, WannaCry, RawDisk, Mimikatz, BADCALL, Volgmer, FALLCHILL, HOPLIGHT, FASTCash
Attack vectors: Adobe Flash player and Hangul Word Processor (HWP) vulnerabilities, social engineering and phishing with fake job offers via LinkedIn and WhatsApp, spear phishing emails containing malicious Microsoft Word vulnerabilities, zero day vulnerabilities.
Targets: South Korean government and military, foreign enterprises, government agencies, financial services infrastructure, businesses and private corporations
Overview: Andariel is a sub-group of the Lazarus Group primarily focused on cyber espionage. Since 2009 has carried out numerous operations against the defense industry, mainly in South Korea and has focused on conducting malicious cyber operations on foreign companies, government agencies, financial services infrastructure, private companies and corporations. Andariel is also believed to be conducting computer intrusions for financial reasons.
Associated Malware: Aryan, Gh0st RAT, Rifdoor, Phandoor, Andarat
Attack vectors: ActiveX, vulnerabilities in software local to South Korea, watering hole attacks, spear phishing (macro), IT management products (antivirus, PMS), supply chain (installers and updaters)
Suspected attribution:Democratic People’s Republic of Korea
Targets: mainly South Korea, but also the United States, Japan, Vietnam and the Middle East, across various vertical sectors, including chemicals, electronics, manufacturing, banking, aerospace, automotive, and healthcare.
Overview: alleged North Korean state-sponsored cyber espionage group that has been active since at least 2012. The group previously used a series of zero-day exploits to carry out attacks on victims of interest to the North Korean government, in line with counter-intelligence priorities.
Associated Malware: APT37 employs a diverse suite of malware for initial intrusion and exfiltration. Their malware is characterized by a focus on stealing information from victims, with many set up to automatically exfiltrate data of interest. APT37 also has access to destructive malware. Some include DOGCALL, RUHAPPY, CORALDECK, SHUTTERSPEED, WINERACK, and several 0-day Flash and MS Office exploits.
Attack vectors: tattiche di ingegneria sociale su misura per gli obiettivi desiderati, compromissioni web strategiche tipiche delle operazioni di spionaggio informatico mirate e l’uso di siti di condivisione file torrent per distribuire malware in modo più indiscriminato.

Suspected attribution: RPDC, Reconnaissance General Bureau Settori target: banche, istituzioni finanziarie, exchange di criptovalute
Overview: financially-motivated is backed by the North Korean regime and mainly targets banks and financial institutions, and it has targeted more than 16 organizations in at least 13 countries since at least 2014. The funds stolen by APT38 are likely channeled into the DPRK’s missile and nuclear development programs. APT38 is known to share malware and other resources with TEMP.Hermit. In February 2021, three members of APT38 were indicted by the US DOJ.
Associated Malware: DarkComet, Mimikatz, Net, NESTEGG, MACKTRUCK, WANNACRY, WHITEOUT, QUICKCAFE, RAWHIDE, SMOOTHRIDE, TightVNC, SORRYBRUTE, KEYLIME, SNAPSHOT, MAPMAKER, net.exe, sysmon, BOOTWRECK, CLEANTOAD, Hermes , ELECTRICFISH, PowerRatankba, PowerSpritz
Attack vectors: Drive-by compromise, watering hole schemes, exploit insecure out-of-date version of Apache Struts2 to execute code on a system, strategic web compromise, access Linux servers.
Suspected attribution: RPDC, Lab 110, 6th Technical Bureau of the Reconnaissance General Bureau (RGB)
Targets: primarily government, defense, energy and financial institutions in South Korea, as well as targets around the world aligned with DPRK affairs, including the United States.
Overview: TEMP.Hermit is a FireEye-monitored cyber espionage group that has been active since at least 2013. The group primarily targets the government, defense, energy and finance sectors in South Korea, but also conducts operations against aligned targets around the world with North Korean business. TEMP.Hermit is believed to share significant development resources with APT38.
Associated Malware: MONKEYCHERRY, FALLCHILL
Attack Vectors: Spear phishing, front organizations mainly located in northeast China
Suspected attribution: RPDC
Targets: governments, think tanks and universities; mainly in the United States and South Korea, but also in Australia, Italy, India, Japan, Hong Kong, Hungary and the Philippines.
Overview: TEMP.Firework primarily targets governments, think tanks and universities focusing on strategic DPRK issues such as nuclear safety, non-proliferation, and US and South Korean military capabilities. The group typically operates between 07: 00 and 19:00 KST (GMT +9) Monday through Friday and has only been observed once operating outside of this schedule. In some recent operations, TEMP.Firework was called in for the cyber campaigns leading up to the 2020 U.S. election and conducted spear phishing to gain access to more pharmaceutical companies and medical centers.
Associated Malware: LATEOP, TROIBOMB, Mshta, TeamViewer, Mimikatz, LOGCABIN e comandi Windows integrati
Attack vectors: e-mail di spear phishing, credenziali rubate

Suspected attribution: North Korea (RPDC)
Targets: identified by Proofpoint in three separate groups – TA406, TA408 and TA427 – it targets entities of interest to the North Korean government, then government entities in South Korea, Japan and the United States, as well as universities with biomedical engineering expertise.
Overview: the Kimsuky APT group has most likely been active since 2012 and is most likely tasked by the North Korean regime with a global intelligence gathering mission. Kimsuky has reused infrastructure from previous campaigns in the past. It is a highly motivated group that targets a number of entities in South Korea with targeted, even destructive, attacks.
Associated Malware: BabyShark, GREASE, Win7Elevate, HWP document malware, malicious Google Chrome extension
Attack vectors: Kimsuky employs common social engineering tactics, spear phishing, and watering hole attacks to exfiltrate desired information from victims.
Follow us on Google News to receive daily updates on cybersecurity. Contact us if you would like to report news, insights or content for publication.
