
In the late 1990s, the Internet was still small, slow, and accessible to a select few. Back then, being a ” geek ” meant having a technical knowledge that seemed almost magical in the eyes of others. It wasn’t uncommon for more experienced kids to enjoy scaring their friends by remotely taking control of their PCs—what today we would call, bluntly, trolling .
The CD tray that opened by itself, the mouse buttons that flipped, the desktop colors that suddenly changed: harmless little pranks that transformed the computer into something seemingly possessed. To the unsuspecting user, it truly felt as if a ghost had taken control of the machine, when in reality it was just a curious friend, a shaky connection, and a great desire to experiment (hacking).
That culture of technological pranks, driven by curiosity and still unclear boundaries, was the fertile ground for the first experiments with “unsolicited” software. And we’ll see how, after the concept of ” malware ,” it evolved into the dramas we know today. But back then, it was just “a game.”
Long before the Internet and remote control and mass surveillance, there was a story that is still cited today as the symbolic origin of malware: that of Elk Cloner , one of the first microcomputer viruses to spread outside the environment in which it was created.
The year is 1982. The target is the Apple II , the operating system is Apple DOS 3.3 , and the means of distribution is the floppy disk. The writer is Rich Skrenta , then a fifteen-year-old high school student in Pennsylvania, with a great passion for programming… and pranks.

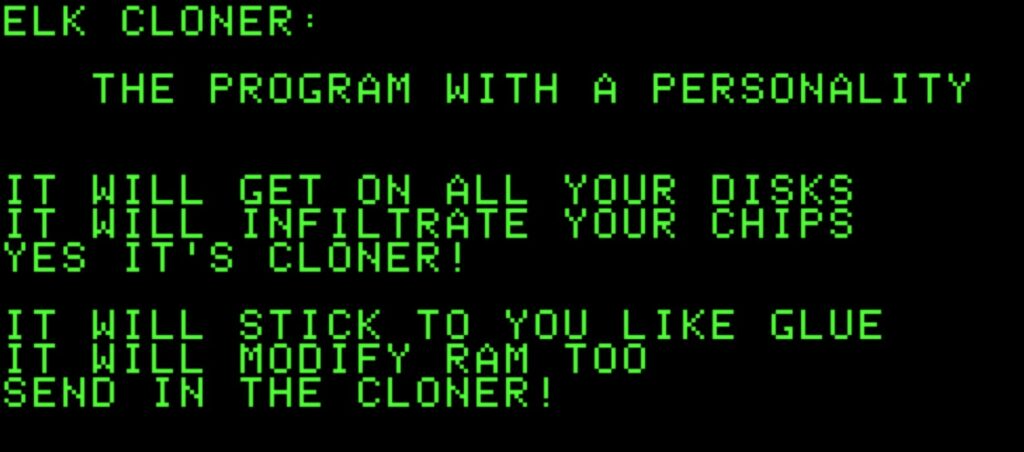
Elk Cloner was hidden inside a floppy disk along with a video game. After the game was launched 50 times, the virus would activate, displaying a blank screen with a poem that read:
Elk Cloner: The program with a personality
It will get on all your disks
It will infiltrate your chips
Yes, it’s Cloner!
It will stick to you like glue
It will modify RAM too
Send in the Cloner!
It didn’t delete data, it didn’t destroy the system: it just wanted to be noticed. But it did so in a new, autonomous, and persistent way.
Skrenta was already known among his friends for this type of prank: modified floppy disks that would shut down the computer or display provocative messages on the screen. At some point, many of them simply stopped exchanging disks with him.
For this reason, Skrenta began looking for ways to alter floppy disks without physically touching them. During a winter break from Lebanon High School , he discovered how to automatically run code on the Apple II, creating a technique that would forever change the way software could be distributed.
On the technical side, Elk Cloner introduced a concept that would become fundamental in the history of computer security: the boot sector virus . If a computer was booted from an infected floppy disk , a copy of the virus was loaded into memory. From there, any subsequent “clean” floppy disk inserted was automatically infected, because the entire DOS— including Elk Cloner —was copied to the disk. No clicks, no confirmation, no suspicion.
Once established in RAM, the virus operated as a resident process that constantly monitored disk drive activity . The software remained in a silent waiting state until a new, blank or uncompromised disk was inserted. As soon as the user issued a standard system command, such as a request to list the files on the disk, Elk Cloner intercepted the operation and instantly copied itself to the reserved sectors of the new floppy disk, turning it into an unwitting vector of infection.
The most sophisticated aspect of its architecture was the infection status monitoring system, designed to avoid excessively corrupting the operating system or revealing itself too early. The code included an internal counter that recorded the number of boot attempts made from a particular disk, allowing the virus to remain latent for long periods. This strategic approach facilitated widespread dissemination through the physical exchange of floppy disks among students, since no one suspected the presence of the “cloner” until the infection network was already vast.
The final act of the operational chain was triggered precisely at the fiftieth launch, the moment at which the virus abandoned its secrecy and revealed itself to the user. Instead of loading the desired programs, Elk Cloner interrupted the operational sequence to display a rhyming poem declaring its identity and pervasive nature . This author’s signature transformed what was technically a cyber attack into a sort of social experiment, demonstrating for the first time how fragile trust in the integrity of software and physical media could be.
In 2007, twenty-five years later , Skrenta called Elk Cloner “a stupid practical joke.” But by then the seed had been planted.
Those were the years that marked the birth of viruses , Trojans and, later, RATs (Remote Access Trojans) : malicious software no longer designed for entertainment, but to gain persistent and unauthorized access to victims’ systems.
From then on, the evolution was rapid and brutal. Malware became tools for data theft, industrial sabotage, espionage, and intelligence operations. Today, entire underground markets exist where any type of malware is available at low cost: ransomware, infostealers, botnets, exploit kits.
Common criminals, APT groups, secret services, and their affiliates: they all use variations of the same concept born over forty years ago: software that spreads without consent, exploits user trust, and remains hidden for as long as possible.
The malware industry moves millions of dollars every year. Yet it all started with a game, a poem on a black screen, what its creator himself simply called “a stupid practical joke.”
This is how the first virus was born.
Follow us on Google News to receive daily updates on cybersecurity. Contact us if you would like to report news, insights or content for publication.
