
Autore: Eros Capobianco
Data Pubblicazione: 16/03/2022
Emotet è un malware della categoria Trojan Horse, che iniziò la sua prima diffusione nel 2014 che lo portò sul podio tra le principali minacce informatiche del decennio riuscendo a colpire oltre 1,6 milioni di dispositivi come riportato da Bleeping Computer.
Inizialmente Emotet, figlio dell’organizzazione criminale MealyBug era utilizzato con lo scopo di rubare credenziali di servizi bancari. Una volta installato il malware poteva scaricare diversi moduli incaricati dell’esfiltrazione dei dati.
Alcuni di questi moduli utilizzavano algoritmi di forza bruta per scovare password all’interno del dispositivo infetto, ricercando le password tra quelle salvate dal browser e sulla macchina.
Nel corso della sua evoluzione, vista l’efficienza del trojan nella sua diffusione, venne riconfigurato in modo tale da consentire il download di payloads differenti nelle macchine infette, aumentandone drasticamente la pericolosità e passando così dal ruolo di semplice trojan horse a quello ben più minaccioso di trojan-dropper modulare.
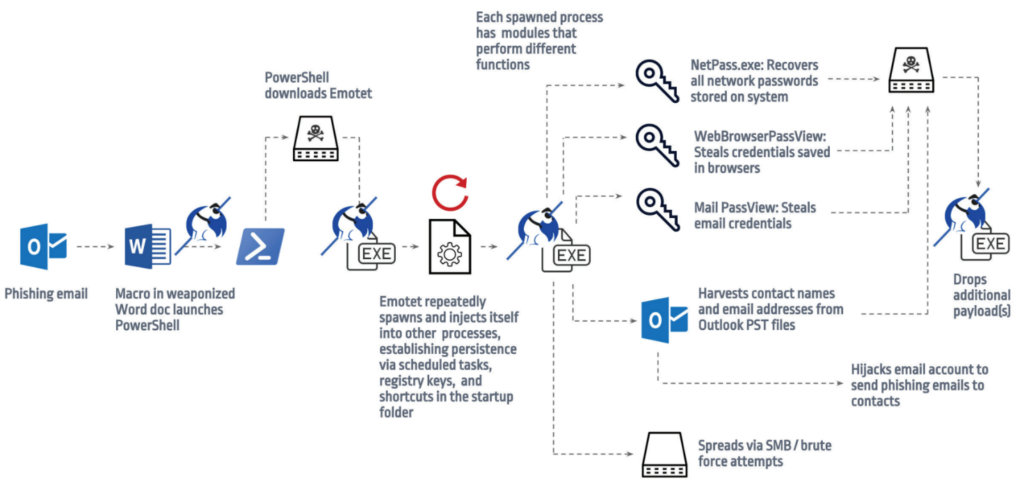
Inoltre, con lo scopo di aumentare i guadagni dell’organizzazione, le botnet create tramite il famoso trojan iniziarono successivamente ad essere affittate nel darkweb, rientrando quindi nella categoria del Malware-as-a-Service. Queste infrastrutture sono state affittate a molte altre organizzazioni criminali tra cui anche la cybergang Ryuk.
Nelle versioni successive in cui era utilizzato come dropper, il malware scaricava ed installava all’interno del dispositivo vittima altri malware tra cui i famosi TrickBot, Qbot e Conti.
La pericolosità di questo malware è dettata principalmente dalla sua caratteristica chiave ovvero essere polimorfico. Si intende perciò che l’impronta del malware, ovvero la sequenza di byte che lo identifica in modo univoco, viene modificata dal malware crittografando il proprio codice ad ogni infezione, in questo modo risulta complesso anche per gli anti-virus tradizionali rilevare la violazione.
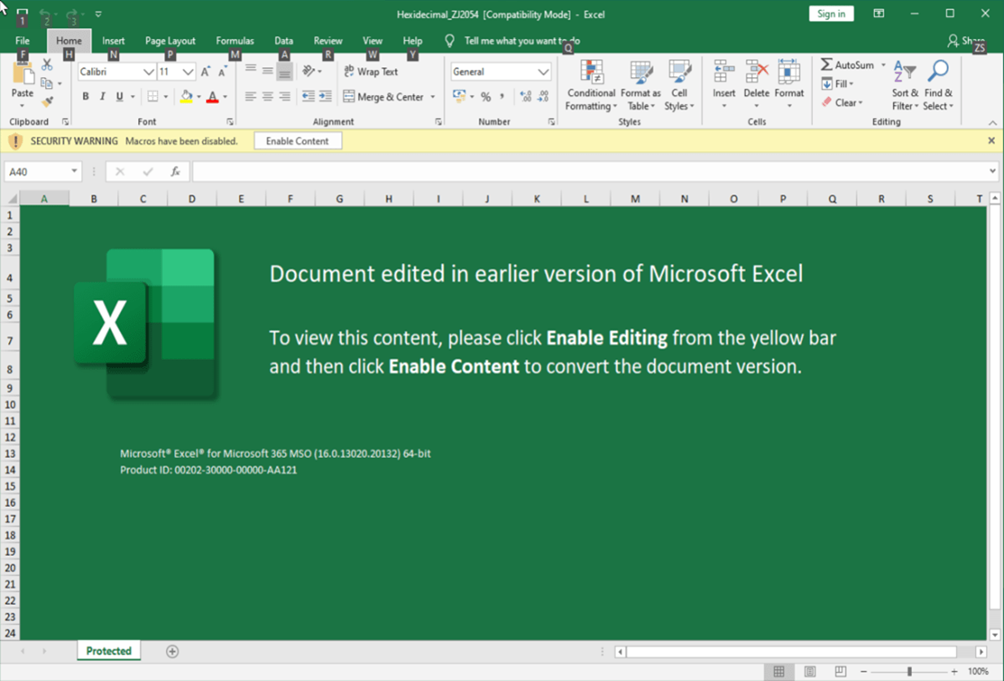
Inizialmente la diffusione era basata tramite mail-spam e una volta installato, svolgeva una ricerca dei contatti segnati come: familiari, amici, lavoro; all’interno di Outlook per poi inviare mail a questi contatti, spesso utilizzando come oggetto ”RE:” ed il titolo di una e-mail ricevuta in precedenza.
Da notare che le e-mail inviate erano scritte in modo da sembrare veramente autentiche e contenevano un file word che una volta scaricato e aperto richiedeva all’utente di abilitare le macro (Figura 2), in questo modo il codice nascosto all’interno del file veniva eseguito ed installato sulla nuova macchina.
Bisogna però considerare che la diffusione di Emotet, come avviene spesso anche con altri malware, non è sempre identica, infatti vengono segnalati casi di diffusione attraverso file Excell, rete Lan, e-mail, sempre eseguendo programmi esterni e più in generale file con estensioni (.doc, .docx, .xls, .xlsx) oppure cartelle compresse .zip protette da password inviata in allegato.
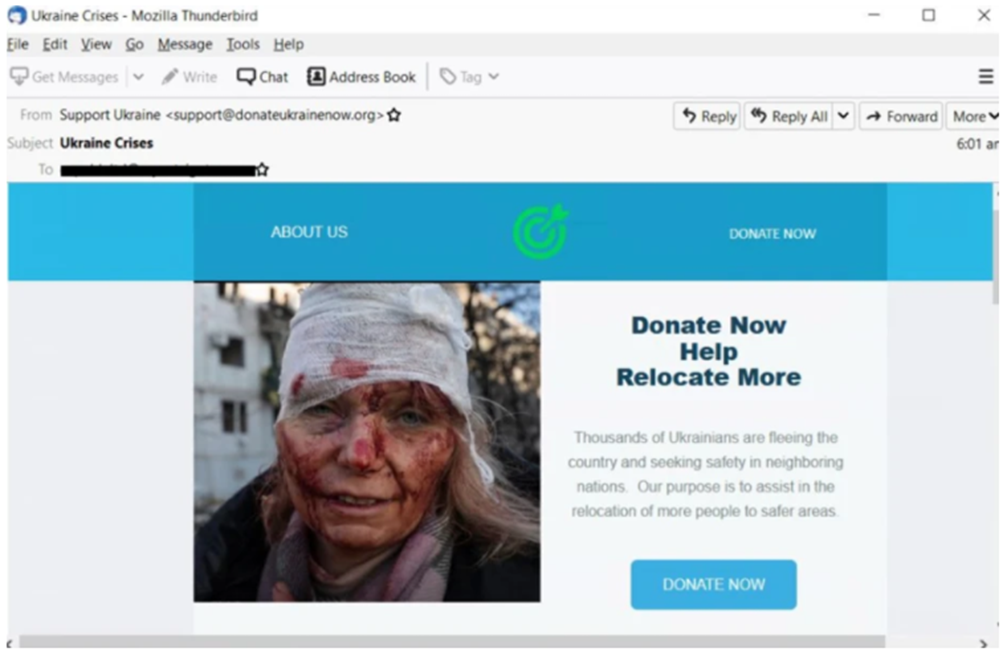
Nel caso specifico dell’Italia, vengono invece segnalate mail malevole con richiami al Mise, spam riguardanti il coronavirus, piuttosto che riguardanti la recente crisi in Ucraina (Figura 3).
Come si può ben immaginare, l’organizzazione criminale alle spalle di questo malware, non trasmette il trojan dal proprio computer di casa, bensì utilizza nella maggior parte dei casi delle botnet, ovvero un vasto gruppo di dispositivi compromessi collegati tramite internet ad infrastrutture di rete sotto controllo dei criminali.
Nel nostro caso, viene associato a termini noti come Epoch (epoche), ciò è utilizzato per indicare la botnet di distribuzione del malware e l’infrastruttura fisica di gestione della rete correlata ad essa, questi termini a loro volta sono associati ad uno specifico numero.
Le epoch 1, 2 e 3, sono quelle botnet incaricate della distribuzione molto attive fino al 2021, anno in cui tramite un’operazione speciale delle autorità di Germania, Paesi Bassi, Stati Uniti, Regno Unito, Francia, Lituania, Canada ed Ucraina coordinata tramite Europol ed Eurojust, le infrastrutture portanti e di supporto delle reti criminali individuate sono state bloccate e smantellate.
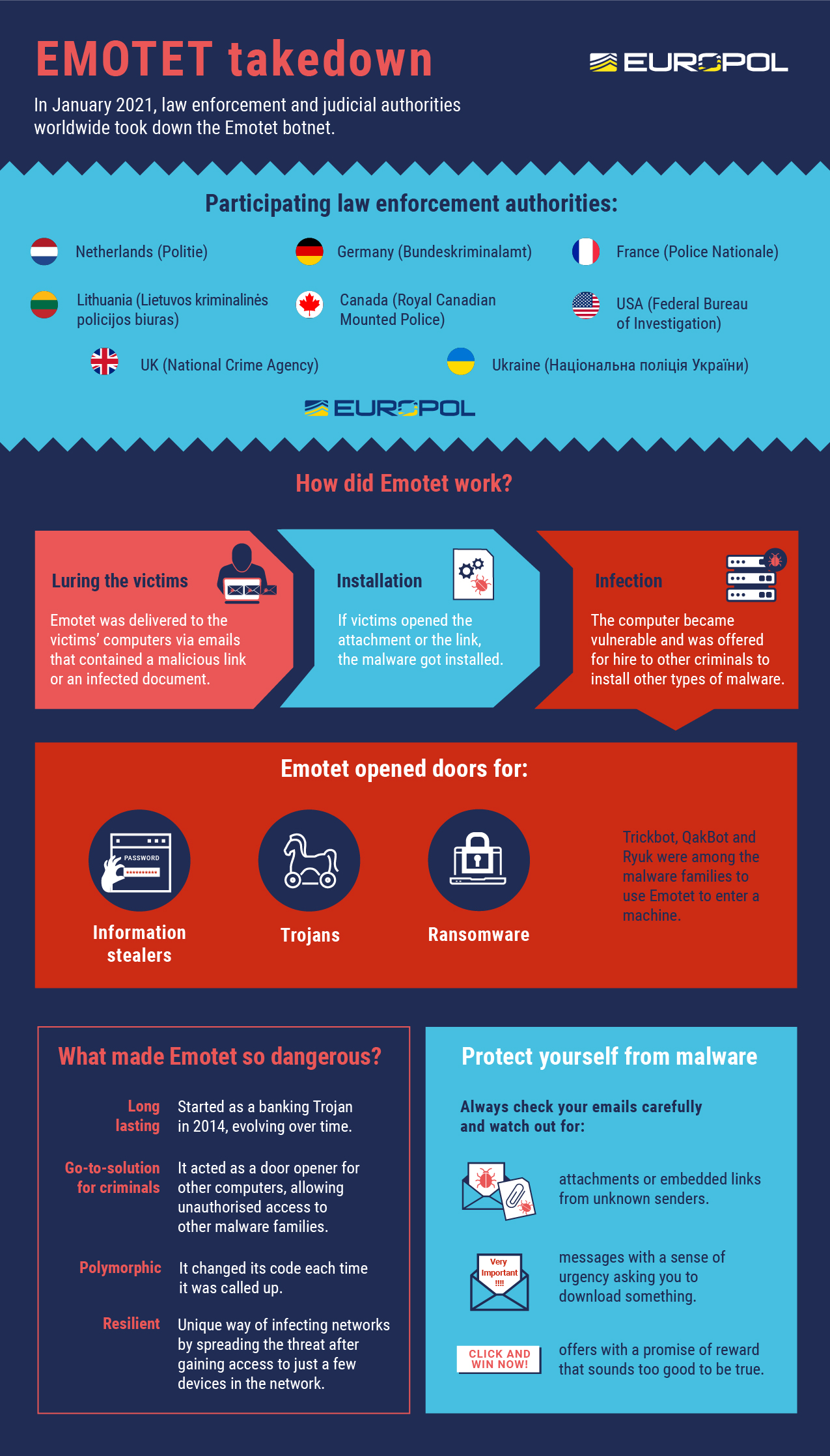
Questa operazione rese innocuo il trojan all’interno dei computer infetti rendendo il malware non più utilizzabile per le sue “mansioni” ed un grande numero di cyber-criminali legati a queste reti furono arrestati.
In seguito tramite l’operazione LadyBird venne sfruttata la funzionalità dropper di Emotet per scaricare su tutti i computer infetti un modulo contenente una procedura automatizzata di disinstallazione, messa in atto dalle forze dell’ordine,.
Nel Novembre 2021 vi è stata una “resurrezione di Emotet” in quanto gruppi di cybercriminali iniziano a ricostruire le reti del trojan tramite nuove campagne di spam-mail, da cui nascono le Epoch 4 e 5.
La caratteristica principale che differenzia queste nuove botnet dalle precedenti è che in questo caso l’infezione da Emotet portava con sé l’attivazione di un beacon Cobalt Strike.
Cobalt Strike è uno strumento utilizzato nella sicurezza informatica per creare simulazioni di attività criminali in una rete, lo strumento in questione, attraverso l’installazione di un beacon permette l’esecuzione di comandi, esfiltrazione di dati, privilege escalation e movimenti laterali.
Il payload di Emotet in questa nuova versione, una volta installato il beacon, cerca di rintracciare un controller di dominio e le credenziali dell’Active Directory in modo da diffondersi attraverso tutti i computer della rete e quindi velocizzare la propria diffusione e la ricostruzione delle botnet.
Nel caso specifico, gli amministratori di rete potrebbe invece ricorrere a metodi quali:
Ti è piaciuto questo articolo? Ne stiamo discutendo nella nostra Community su LinkedIn, Facebook e Instagram. Seguici anche su Google News, per ricevere aggiornamenti quotidiani sulla sicurezza informatica o Scrivici se desideri segnalarci notizie, approfondimenti o contributi da pubblicare.

 Cybercrime
CybercrimeLe autorità tedesche hanno recentemente lanciato un avviso riguardante una sofisticata campagna di phishing che prende di mira gli utenti di Signal in Germania e nel resto d’Europa. L’attacco si concentra su profili specifici, tra…
 Innovazione
InnovazioneL’evoluzione dell’Intelligenza Artificiale ha superato una nuova, inquietante frontiera. Se fino a ieri parlavamo di algoritmi confinati dietro uno schermo, oggi ci troviamo di fronte al concetto di “Meatspace Layer”: un’infrastruttura dove le macchine non…
 Cybercrime
CybercrimeNegli ultimi anni, la sicurezza delle reti ha affrontato minacce sempre più sofisticate, capaci di aggirare le difese tradizionali e di penetrare negli strati più profondi delle infrastrutture. Un’analisi recente ha portato alla luce uno…
 Vulnerabilità
VulnerabilitàNegli ultimi tempi, la piattaforma di automazione n8n sta affrontando una serie crescente di bug di sicurezza. n8n è una piattaforma di automazione che trasforma task complessi in operazioni semplici e veloci. Con pochi click…
 Innovazione
InnovazioneArticolo scritto con la collaborazione di Giovanni Pollola. Per anni, “IA a bordo dei satelliti” serviva soprattutto a “ripulire” i dati: meno rumore nelle immagini e nei dati acquisiti attraverso i vari payload multisensoriali, meno…