
Yesterday, the Everest cybercriminal gang claimed responsibility for a cyberattack on McDonald’s on their Data Leak Site (DLS) . From the gang’s post, the cybercriminals claim to have 861GB of data exfiltrated from the company’s IT infrastructure and threaten to release it within eight days.
We don’t yet know whether this data is owned by the company, also because there is no press release regarding the incident on their website yet.
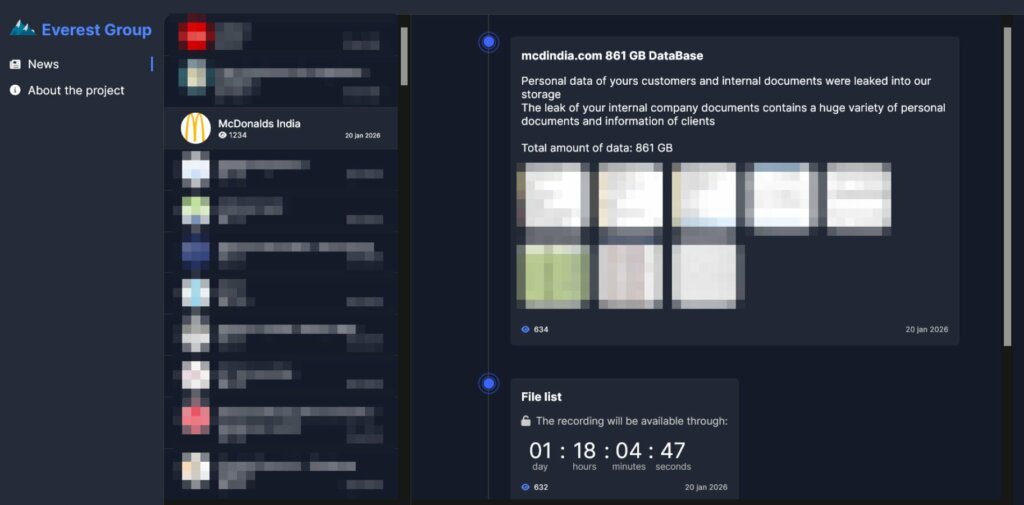
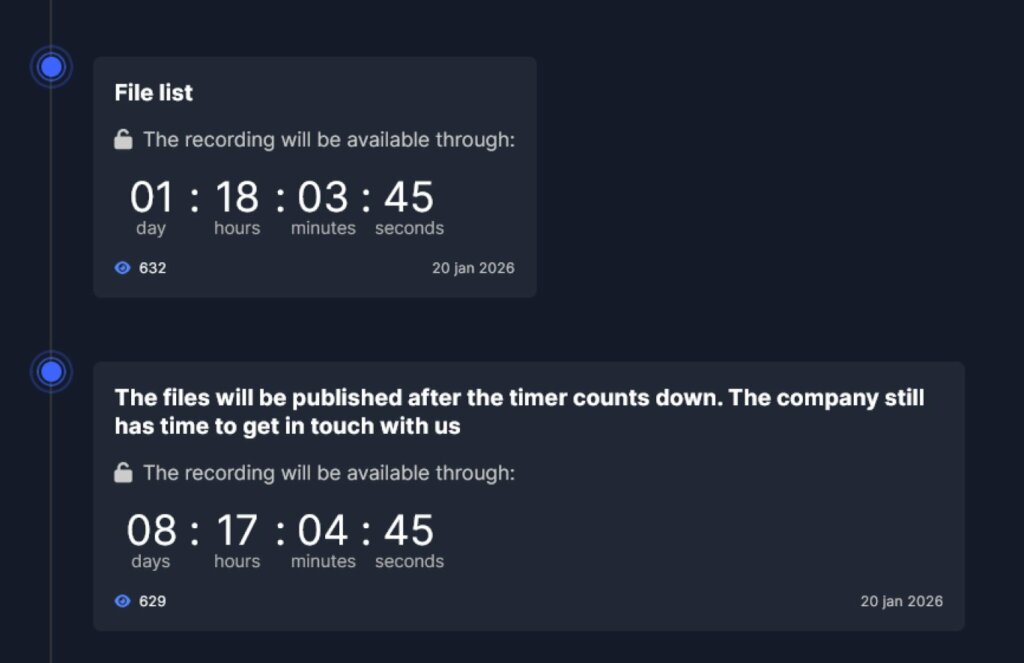
A countdown is active on the gang’s website, indicating that the post will be updated in one day. On that date, the gang will publish the list of files exfiltrated from the company’s IT infrastructure. The data will begin publishing after eight days.
To prove that access to the IT infrastructure was successful, the cyber gang provides a series of samples containing documents relating to the compromised company.
This, as RHC readers know, typically occurs before a ransom payment agreement has been finalized. By threatening to release the data in their possession, they increase pressure on the compromised organization, hoping for faster payment.
As we often report, anyone with normal PC skills can access the Darknet. This is important to highlight, as many claim the opposite, often in press releases following the publication of ransomware cybergang data, and this information is publicly available as open sources.
As we anticipated at the beginning of the article, at the time of writing there is no press release on the victim’s website warning of the cyber incident.
As is our custom, we’ll leave room for a statement from the company if they’d like to provide us with updates on this matter, and we’ll be happy to publish it in a dedicated article highlighting the issue.
RHC will monitor the development of the case and publish further news on the blog if there are any substantial developments. Anyone with knowledge of the matter who wishes to provide information anonymously can access it using the whistleblower’s encrypted email address.
Ransomware is a type of malware that is injected into an organization to encrypt data and render systems unavailable. Once the data is encrypted, the criminals demand a ransom from the victim, paid in cryptocurrency, to decrypt it.
If the victim refuses to pay the ransom, the criminals will proceed with double extortion, namely the threat of publishing sensitive data previously exfiltrated from the victim’s IT infrastructure.
The Everest ransomware emerged in the second half of 2018, carrying out attacks on several companies and large organizations, one example being the attack on the Brazilian government, more specifically on a network of the Attorney General of the National Treasury, these attacks were carried out in August 2021.
Everest ransomware is part of the Everest 2.0 family, which consists of Embrace, PainLocker, EvilLocker, and Hyena Locker ransomware.
The group uses the double extortion technique, seeking to increase the profits from their attacks. In this tactic, payment is demanded not only for the decryption key but also to protect the company’s data. This method is used by most ransomware.
The Everest ransomware uses spam email tactics. This tactic involves filling your spam folder with commercial emails from advertising companies, as this increases the chance that the malicious email will end up in your inbox instead of your spam folder.
These emails contain a Word or Excel file with “financial information” and a payload file containing malicious macros, which execute loaders to gain initial access to the system.
The cybergang was also seen not using ransomware, but conducting extortion exclusively by exfiltrating data from victims’ IT systems, without encrypting the contents but demanding a ransom for data deletion.
Ransomware infections can be devastating to an organization, and data recovery can be a difficult and time-consuming process that requires highly trained operators for reliable recovery. Even without a data backup, many recovery attempts have been unsuccessful.
In fact, users and administrators are advised to take preventative security measures to protect their networks from ransomware infections , and they are in order of complexity:
Both individuals and organizations are discouraged from paying the ransom, as even after payment, cyber gangs may not release the decryption key, or recovery operations may be subject to errors and inconsistencies.
Cybersecurity is a serious matter and today it can profoundly undermine a company’s business.
Today we need to immediately change our mindset and think of cybersecurity as an integral part of business, not just after a cybersecurity incident.
Follow us on Google News to receive daily updates on cybersecurity. Contact us if you would like to report news, insights or content for publication.
