
Un nuovo e allarmante sviluppo sta scuotendo il panorama della sicurezza informatica: un attore malevolo ha pubblicizzato sul dark web un exploit altamente sofisticato volto a compromettere dispositivi FortiGate.
Si tratta di un nuovo exploit venduto al prezzo di 12.000 dollari per firewall FortiGate che è apparso in vendita sul noto forum underground Exploit. Il post, pubblicato da un utente con lo pseudonimo Anon-WMG, presenta uno strumento capace di compromettere in modo massivo dispositivi Fortinet sfruttando le API esposte.
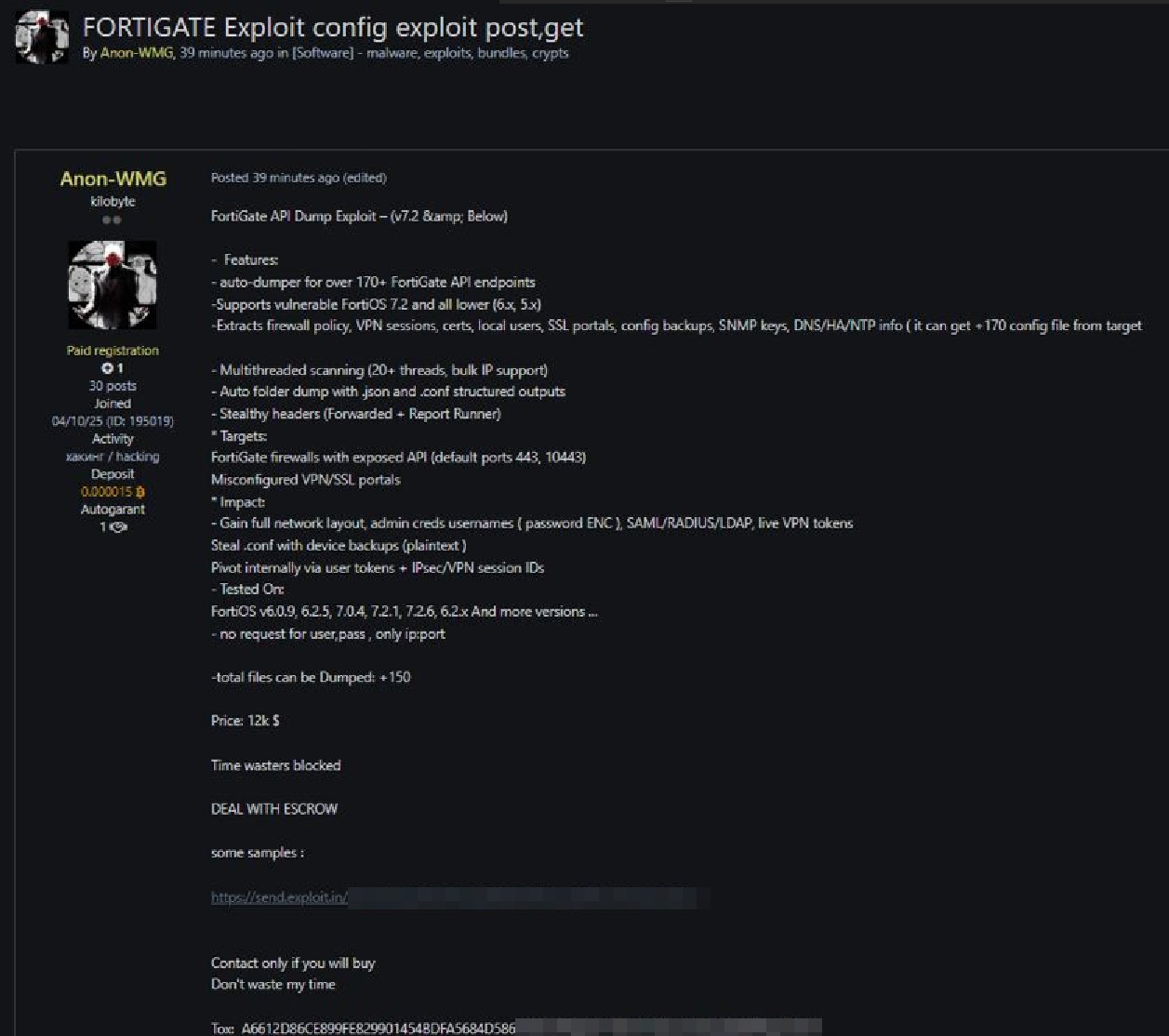
Denominato “FortiGate API Dump Exploit (~7.2 e versioni inferiori)”, il tool è in grado di interagire con oltre 170 endpoint delle API FortiGate, con compatibilità dichiarata per le versioni 6.x e 5.x, e testato anche su 7.2.6 e precedenti. Le funzionalità includono:
Lo strumento prende di mira:
L’autore sostiene che l’exploit sia in grado di compromettere:
Le implicazioni sono gravi e includono:
Il tool risulta testato su numerose versioni di FortiOS: v6.0.9, 6.2.5, 7.0.4, 7.2.1, 7.2.6, 6.2.x e altre.
Le organizzazioni che utilizzano FortiGate devono agire immediatamente, soprattutto se:
Raccomandazioni operative:
La disponibilità di un exploit automatizzato come questo sul mercato underground evidenzia una volta di più quanto sia critico esporre anche solo parzialmente interfacce di gestione non adeguatamente protette. In questo caso, l’accesso non autenticato alle API FortiGate può portare al completo compromesso di una rete.
Ti è piaciuto questo articolo? Ne stiamo discutendo nella nostra Community su LinkedIn, Facebook e Instagram. Seguici anche su Google News, per ricevere aggiornamenti quotidiani sulla sicurezza informatica o Scrivici se desideri segnalarci notizie, approfondimenti o contributi da pubblicare.

 Cybercrime
CybercrimeLe autorità tedesche hanno recentemente lanciato un avviso riguardante una sofisticata campagna di phishing che prende di mira gli utenti di Signal in Germania e nel resto d’Europa. L’attacco si concentra su profili specifici, tra…
 Innovazione
InnovazioneL’evoluzione dell’Intelligenza Artificiale ha superato una nuova, inquietante frontiera. Se fino a ieri parlavamo di algoritmi confinati dietro uno schermo, oggi ci troviamo di fronte al concetto di “Meatspace Layer”: un’infrastruttura dove le macchine non…
 Cybercrime
CybercrimeNegli ultimi anni, la sicurezza delle reti ha affrontato minacce sempre più sofisticate, capaci di aggirare le difese tradizionali e di penetrare negli strati più profondi delle infrastrutture. Un’analisi recente ha portato alla luce uno…
 Vulnerabilità
VulnerabilitàNegli ultimi tempi, la piattaforma di automazione n8n sta affrontando una serie crescente di bug di sicurezza. n8n è una piattaforma di automazione che trasforma task complessi in operazioni semplici e veloci. Con pochi click…
 Innovazione
InnovazioneArticolo scritto con la collaborazione di Giovanni Pollola. Per anni, “IA a bordo dei satelliti” serviva soprattutto a “ripulire” i dati: meno rumore nelle immagini e nei dati acquisiti attraverso i vari payload multisensoriali, meno…