
Il team di FortiGuard Labs ha pubblicato un’analisi dettagliata di una web shell fortemente offuscata utilizzata per attaccare infrastrutture critiche in Medio Oriente. La ricerca si concentra sullo script UpdateChecker.aspx in esecuzione sulla piattaforma Microsoft IIS. È implementato in C# come pagina ASPX e nasconde il suo contenuto reale dietro uno strato di codice codificato e crittografato. Tutti i nomi di variabili e metodi di classe sono stati generati casualmente e poi codificati in Unicode. Tutte le costanti, incluse stringhe e numeri, sono state crittografate o codificate.
Durante l’analisi, gli esperti hanno deoffuscato il codice e convertito nomi casuali in nomi leggibili. La funzione principale Page_Load viene avviata alla ricezione di un comando dall’attaccante. La shell viene controllata tramite richieste HTTP POST con il contenuto specificato come application/octet-stream. In caso contrario, la richiesta viene rifiutata e viene restituita una pagina di errore.
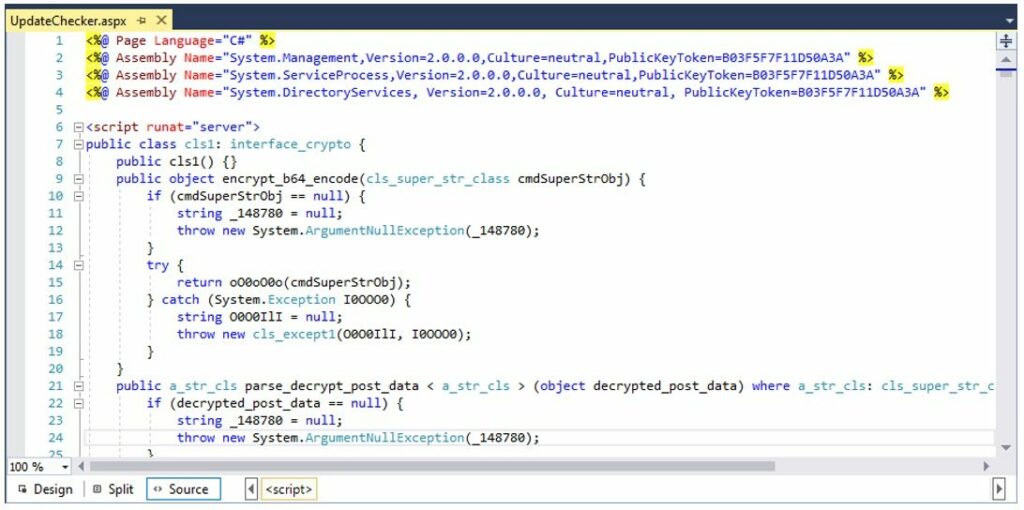
Il corpo della richiesta viene prima codificato in Base64 e poi decrittografato in più fasi. I primi 16 byte contengono la chiave crittografata, che viene decodificata per produrre 15 byte di chiave e un byte di padding. Questa chiave viene utilizzata per decrittografare il resto dei dati del comando. Anche la risposta della web shell è in formato JSON, quindi crittografata e codificata nuovamente in Base64.
Lo script supporta tre moduli principali di gestione del sistema. Il modulo Base consente di ottenere informazioni sul server, il modulo CommandShell esegue i comandi di sistema nella directory di lavoro specificata e il modulo FileManager consente di interagire con file e directory, tra cui la creazione, la copia, lo spostamento e l’eliminazione dei file di directory, nonché la modifica dei metadati e la visualizzazione dell’elenco dei dischi e della directory web principale.
Per illustrare questo concetto, Fortinet ha sviluppato uno script Python che simula le azioni di un aggressore per inviare comandi alla web shell e visualizzare le risposte. Grazie a questo, è stato possibile dimostrare le capacità della shell, tra cui l’esecuzione di comandi, l’elaborazione di file e la ricezione di varie informazioni dal server.
L’analisi di UpdateChecker.aspx ha contribuito a svelare la complessa architettura della web shell e a mostrare come gli aggressori controllano il sistema in modo occulto e sicuro: lo script memorizza il controllo in formato JSON, il che semplifica l’invio automatico di comandi e la ricezione di risposte.
Ti è piaciuto questo articolo? Ne stiamo discutendo nella nostra Community su LinkedIn, Facebook e Instagram. Seguici anche su Google News, per ricevere aggiornamenti quotidiani sulla sicurezza informatica o Scrivici se desideri segnalarci notizie, approfondimenti o contributi da pubblicare.

 Cybercrime
CybercrimeLe autorità tedesche hanno recentemente lanciato un avviso riguardante una sofisticata campagna di phishing che prende di mira gli utenti di Signal in Germania e nel resto d’Europa. L’attacco si concentra su profili specifici, tra…
 Innovazione
InnovazioneL’evoluzione dell’Intelligenza Artificiale ha superato una nuova, inquietante frontiera. Se fino a ieri parlavamo di algoritmi confinati dietro uno schermo, oggi ci troviamo di fronte al concetto di “Meatspace Layer”: un’infrastruttura dove le macchine non…
 Cybercrime
CybercrimeNegli ultimi anni, la sicurezza delle reti ha affrontato minacce sempre più sofisticate, capaci di aggirare le difese tradizionali e di penetrare negli strati più profondi delle infrastrutture. Un’analisi recente ha portato alla luce uno…
 Vulnerabilità
VulnerabilitàNegli ultimi tempi, la piattaforma di automazione n8n sta affrontando una serie crescente di bug di sicurezza. n8n è una piattaforma di automazione che trasforma task complessi in operazioni semplici e veloci. Con pochi click…
 Innovazione
InnovazioneArticolo scritto con la collaborazione di Giovanni Pollola. Per anni, “IA a bordo dei satelliti” serviva soprattutto a “ripulire” i dati: meno rumore nelle immagini e nei dati acquisiti attraverso i vari payload multisensoriali, meno…