
GreyNoise ha rilevato due importanti ondate di attacchi ai dispositivi Fortinet all’inizio di agosto 2025. La prima, un attacco brute-force mirato alla VPN SSL di Fortinet il 3 agosto, che poi è stato seguito da un brusco cambiamento su FortiManager il 5 agosto, con una nuova firma del traffico. I ricercatori avvertono che tali picchi di attività precedono la pubblicazione di vulnerabilità critiche nell’80% dei casi.
Secondo GreyNoise, il picco del 3 agosto ha coinvolto tentativi di accesso basati su dizionario sulla VPN SSL FortiOS . L’impronta digitale della rete JA4+, che utilizza l’impronta digitale TLS per classificare il traffico crittografato, ha indicato una possibile corrispondenza con l’attività osservata a giugno. Tale traffico proveniva da un indirizzo IP residenziale associato all’ISP Pilot Fiber Inc. Sebbene ciò non dimostri un’attribuzione specifica, i ricercatori suggeriscono il riutilizzo dello stesso toolkit o infrastruttura.
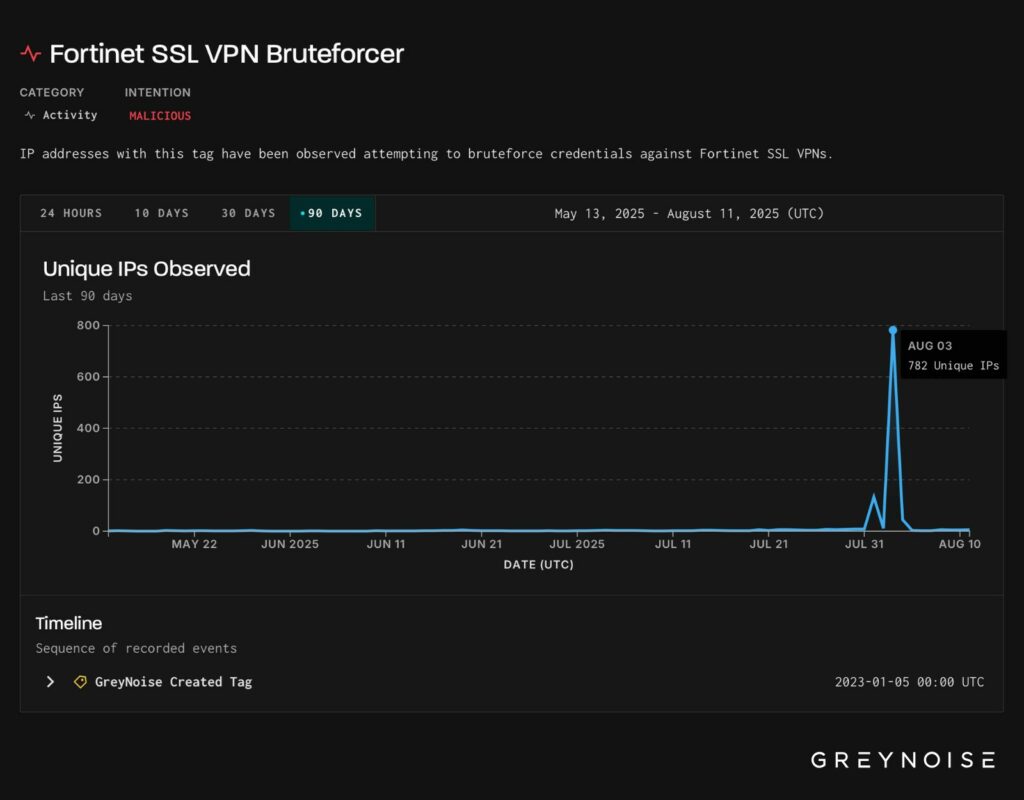
Il 5 agosto, è stata osservata una situazione diversa. L’aggressore è passato da SSL VPN a FortiManager e ha iniziato con attacchi di brute force al servizio FGFM, che fa parte del sistema di gestione Fortinet. Sebbene i filtri GreyNoise continuassero a attivarsi sul vecchio tag “Fortinet SSL VPN Bruteforcer”, la firma del traffico stessa è cambiata. Il nuovo flusso non corrispondeva più a FortiOS, ma corrispondeva esattamente al profilo FortiManager, ovvero FGFM. Ciò indica un cambio di target che utilizza gli stessi strumenti o una continuazione della campagna con un nuovo focus.
GreyNoise sottolinea che queste scansioni non sono solitamente esplorative, poiché le attività esplorative hanno una portata ampia, una frequenza moderata e non comportano l’individuazione delle password. In questo caso, l’attività sembra essere una fase preparatoria prima di un tentativo di sfruttamento. L’obiettivo potrebbe non essere semplicemente quello di scoprire endpoint accessibili, ma di condurre una ricognizione preliminare e valutare il valore dei potenziali obiettivi, con un successivo attacco a una vulnerabilità reale non ancora resa pubblica.
Secondo le statistiche di GreyNoise, i picchi di attività registrati , in particolare quelli contrassegnati con questo tag, presentano un’elevata correlazione con i futuri CVE nei prodotti Fortinet. La maggior parte di questi incidenti si conclude con la pubblicazione di una vulnerabilità entro sei settimane. Pertanto, i responsabili della sicurezza non dovrebbero attribuirli a tentativi di sfruttare bug chiusi da tempo. Al contrario, è giunto il momento di rafforzare le difese, soprattutto sulle interfacce esterne, e limitare l’accesso ai pannelli amministrativi tramite IP.
GreyNoise ha anche pubblicato un elenco degli indirizzi IP coinvolti in entrambe le ondate di attacchi e raccomanda di bloccarli su tutti i dispositivi Fortinet.
Secondo gli analisti, dietro questi indirizzi si cela lo stesso gruppo, che conduce test adattivi e modifica le tattiche in tempo reale. A questo proposito, le aziende che utilizzano FortiGate, FortiManager o SSL VPN di Fortinet dovrebbero urgentemente rafforzare le policy di autenticazione, abilitare la protezione brute-force, applicare limitazioni di velocità e, se possibile, limitare l’accesso alle interfacce di gestione solo tramite VPN affidabili o whitelist IP.
Ti è piaciuto questo articolo? Ne stiamo discutendo nella nostra Community su LinkedIn, Facebook e Instagram. Seguici anche su Google News, per ricevere aggiornamenti quotidiani sulla sicurezza informatica o Scrivici se desideri segnalarci notizie, approfondimenti o contributi da pubblicare.

 Cybercrime
CybercrimeLe autorità tedesche hanno recentemente lanciato un avviso riguardante una sofisticata campagna di phishing che prende di mira gli utenti di Signal in Germania e nel resto d’Europa. L’attacco si concentra su profili specifici, tra…
 Innovazione
InnovazioneL’evoluzione dell’Intelligenza Artificiale ha superato una nuova, inquietante frontiera. Se fino a ieri parlavamo di algoritmi confinati dietro uno schermo, oggi ci troviamo di fronte al concetto di “Meatspace Layer”: un’infrastruttura dove le macchine non…
 Cybercrime
CybercrimeNegli ultimi anni, la sicurezza delle reti ha affrontato minacce sempre più sofisticate, capaci di aggirare le difese tradizionali e di penetrare negli strati più profondi delle infrastrutture. Un’analisi recente ha portato alla luce uno…
 Vulnerabilità
VulnerabilitàNegli ultimi tempi, la piattaforma di automazione n8n sta affrontando una serie crescente di bug di sicurezza. n8n è una piattaforma di automazione che trasforma task complessi in operazioni semplici e veloci. Con pochi click…
 Innovazione
InnovazioneArticolo scritto con la collaborazione di Giovanni Pollola. Per anni, “IA a bordo dei satelliti” serviva soprattutto a “ripulire” i dati: meno rumore nelle immagini e nei dati acquisiti attraverso i vari payload multisensoriali, meno…