
A critical vulnerability affecting the FortiOS, FortiWeb, FortiProxy , and FortiSwitchManager product lines has been reported by Fortinet via an urgent security advisory. This advisory was issued in connection with security flaws affecting these products.
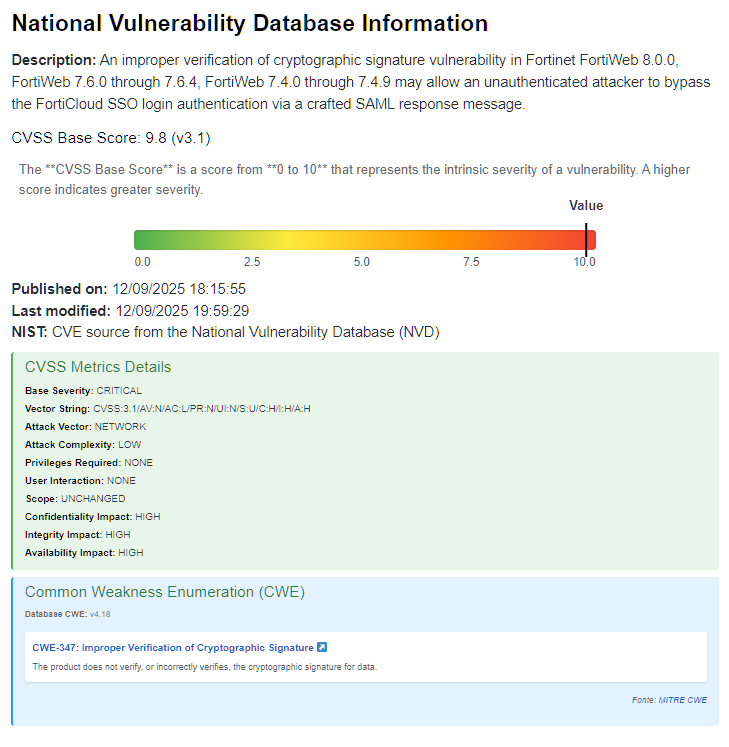
An attacker could gain unauthorized administrative access to the device by crafting a targeted SAML message if the vulnerability is exploited. This vulnerability is caused by the device’s inability to properly verify SAML message signatures.
Fortinet recommends its customers update to the latest versions below. For organizations unable to apply the patches immediately, a workaround has been made available. By disabling the FortiCloud access feature, administrators can mitigate the risk.
| Version | Affected | Solution |
|---|---|---|
| FortiOS 7.6 | 7.6.0 through 7.6.3 | Upgrade to 7.6.4 or above |
| FortiOS 7.4 | 7.4.0 through 7.4.8 | Upgrade to 7.4.9 or above |
| FortiOS 7.2 | 7.2.0 through 7.2.11 | Upgrade to 7.2.12 or above |
| FortiOS 7.0 | 7.0.0 through 7.0.17 | Upgrade to 7.0.18 or above |
| FortiOS 6.4 | Not affected | Not Applicable |
| FortiProxy 7.6 | 7.6.0 through 7.6.3 | Upgrade to 7.6.4 or above |
| FortiProxy 7.4 | 7.4.0 through 7.4.10 | Upgrade to 7.4.11 or above |
| FortiProxy 7.2 | 7.2.0 through 7.2.14 | Upgrade to 7.2.15 or above |
| FortiProxy 7.0 | 7.0.0 through 7.0.21 | Upgrade to 7.0.22 or above |
| FortiSwitchManager 7.2 | 7.2.0 through 7.2.6 | Upgrade to 7.2.7 or above |
| FortiSwitchManager 7.0 | 7.0.0 through 7.0.5 | Upgrade to 7.0.6 or above |
| FortiWeb 8.0 | 8.0.0 | Upgrade to 8.0.1 or above |
| FortiWeb 7.6 | 7.6.0 through 7.6.4 | Upgrade to 7.6.5 or above |
| FortiWeb 7.4 | 7.4.0 through 7.4.9 | Upgrade to 7.4.10 or above |
| FortiWeb 7.2 | Not affected | Not Applicable |
| FortiWeb 7.0 | Not affected | Not Applicable |
The security flaw, identified as Improper Cryptographic Signature Verification (CWE-347), could allow an unauthenticated attacker to bypass FortiCloud Single Sign-On (SSO) login authentication.
When an administrator enrolls a device in FortiCare via the graphical user interface (GUI), the “Allow administrative access via FortiCloud SSO” option is enabled by default. Unless the administrator explicitly disables this option during enrollment, the device is immediately vulnerable to this bypass.
The issue was discovered internally by Theo Leleu and Yonghui Han of the Fortinet product security team, and the information was made public on December 9, 2025. FortiCloud’s SSO feature poses a significant risk, especially in distributed network environments.
Follow us on Google News to receive daily updates on cybersecurity. Contact us if you would like to report news, insights or content for publication.
