
Continuiamo la serie di articoli sugli IAB scrivendo di un cyber contractor iraniano che non solo lavora come broker di accesso iniziale ma fornisce supporto alle ransomware gang per riempire di denaro le loro e le proprie tasche.
In un report del CISA pubblicato ad Agosto 2024, CISA, FBI e la divisione crimini informatici del DoD (Dipartimento della Difesa) affermano che un gruppo iraniano rintracciato come “Pioneer Kitten”, “Fox Kitten”, “UNC757”, “Parisite”, “RUBIDIUM” o “Lemon Sandstorm” ha avuto successo nel cyber crime nella vendita di accessi a reti aziendali violabili. Il gruppo ha operato utilizzando anche altri nomi come “Br0k3r” e “xplfinder” ed è stato osservato mentre vendeva accessi ad affiliati di operazioni RaaS come AlphV/BlackCat, NoEscape e RansomHouse.
Il report di CISA indica anche che nei casi in cui gli affiliati allo schema RaaS hanno avuto difficoltà nel crittografare i device nella rete della vittima, i membri dell’APT iraniano (il gruppo è infatti noto anche come APT33) hanno anche fornito aiuto in cambio di una percentuale sul riscatto ottenuto.
Nella ricerca è stato evidenziato come “Br0K3r” ottenga accessi alle reti violando vecchie vulnerabilità/CVE come quelle (pre 2024)
ma anche exploit più recenti (CVE del 2024)
Il rapporto identifica il gruppo come formato da dipendenti di una società iraniana denominata Danesh Novin Sahand, il che fa sperare alcune delle loro vittime che vi sia la possibilità di portare un’accusa ufficiale nel prossimo futuro a tale organizzazione, forse in una corte internazionale.
Fox Kitten utilizza il motore di ricerca Shodan per identificare gli indirizzi IP che ospitano dispositivi vulnerabili a exploit specifici, come Citrix Netscaler, F5 Big-IP, Pulse Secure/Ivanti VPN o firewall PanOS. Una volta sfruttate le vulnerabilità, l’attore installa webshell e cattura credenziali di accesso prima di creare attività dannose per aggiungere malware backdoor e continuare a compromettere i sistemi. Vengono anche creati nuovi account con nomi che richiamano utenze di tipo ADMIN e vengono disattivati i sistemi EDR/Antivirus. In seguito, verrà fornito nell’articolo un maggiore dettaglio citando le TTPs citate nel rapporto CISA nel paragrafo “Tattiche, tecniche e procedure (TTP) “.
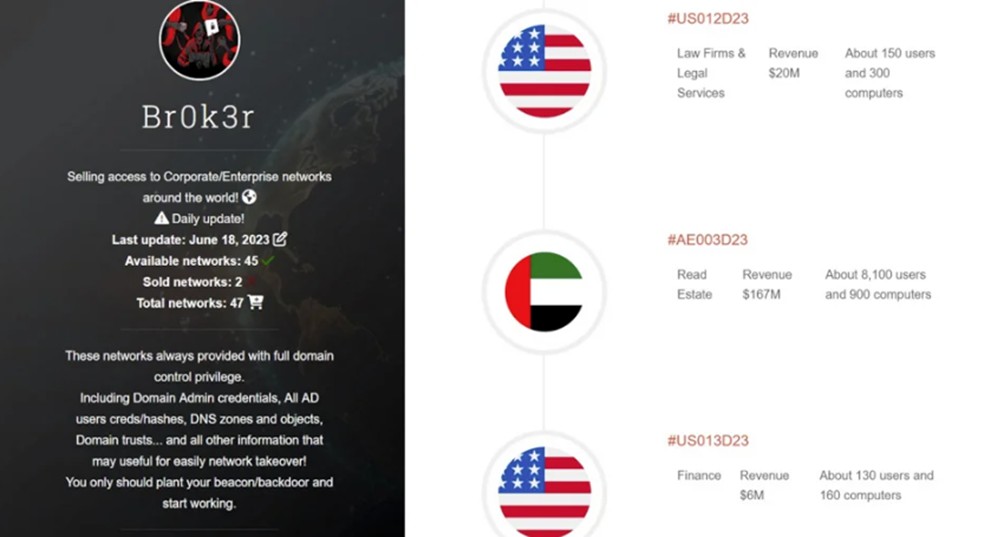
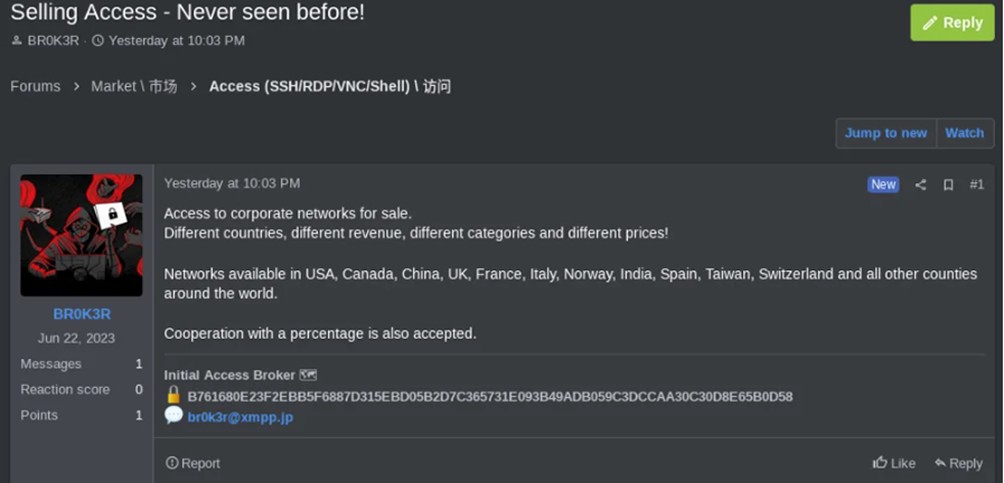
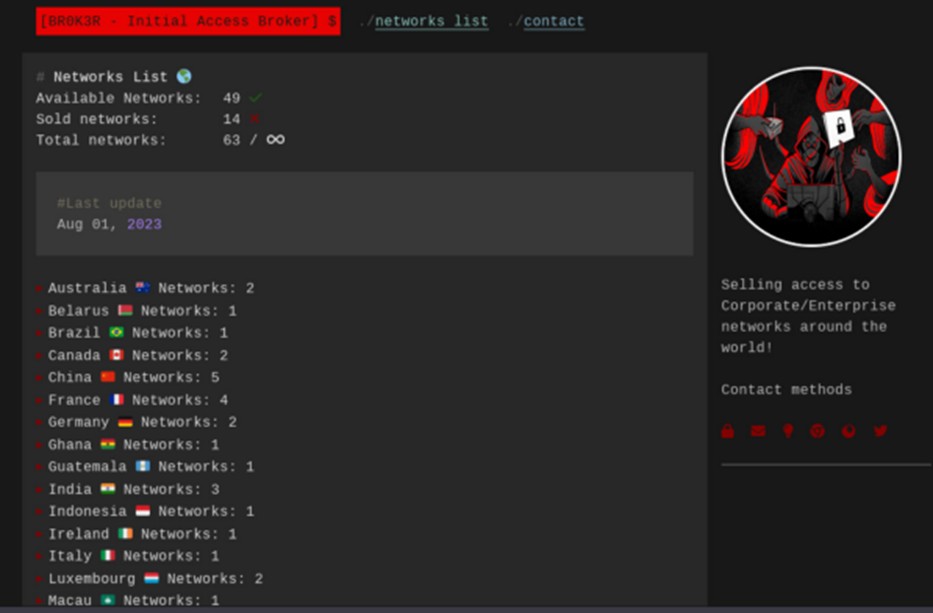
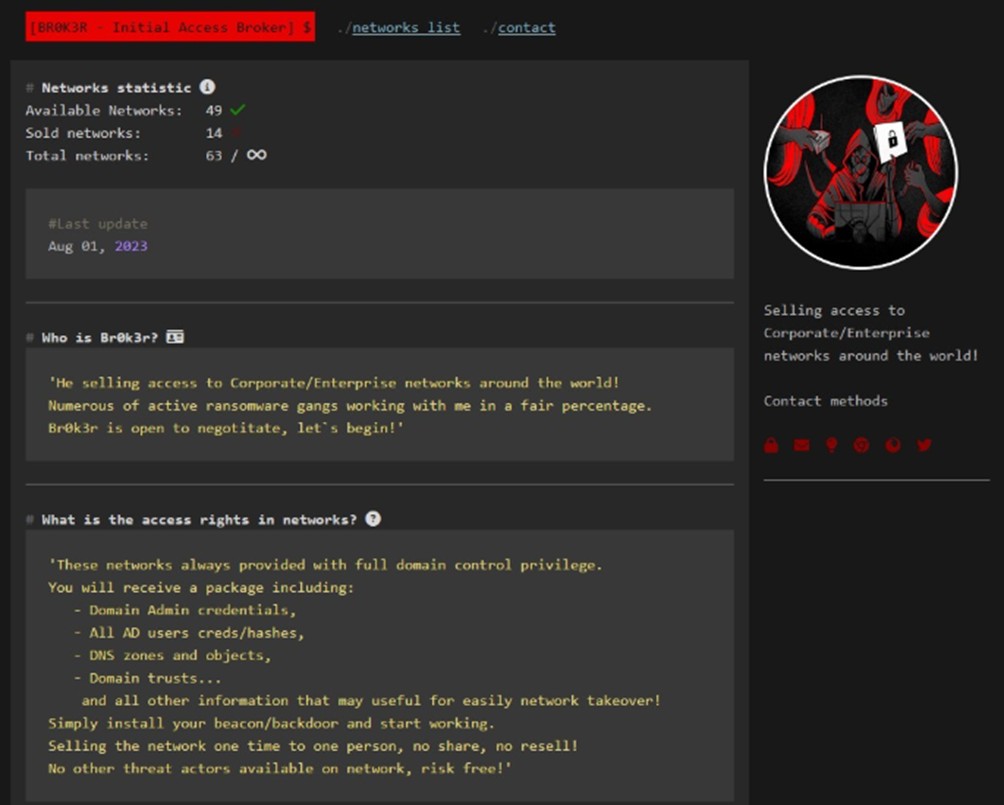
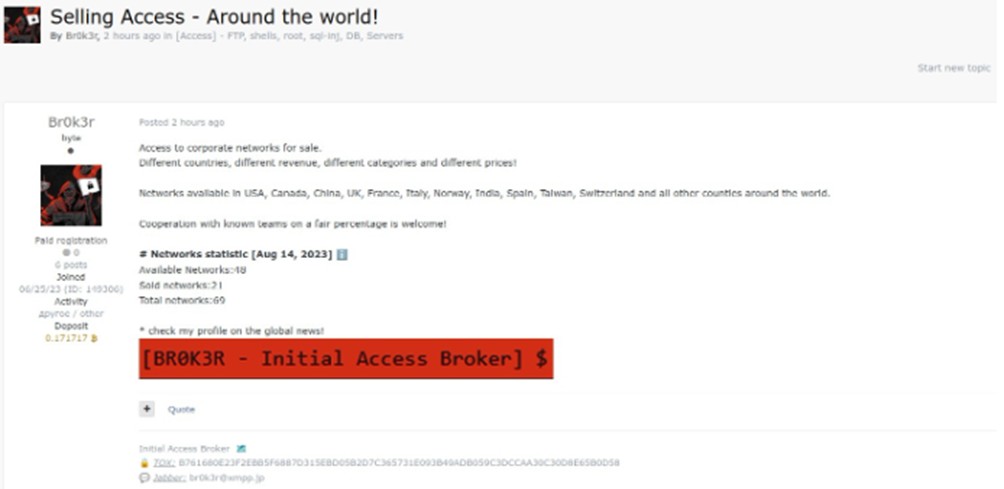
Br0k3r ha adottato un nuovo approccio al modello commerciale IAB, utilizzando un sito ospitato da un singolo fornitore Tor per pubblicizzare i propri accessi su più forum. Questo sito Tor include istruzioni per le richieste e le modalità di acquisto dell’accesso. Secondo Br0k3r, ogni vendita di accesso include credenziali di amministratore di dominio (DA) di Windows, credenziali utente e hash di password di Active Directory (AD), zone e oggetti DNS e trust di dominio di Windows.
Il sito e il sistema sviluppati da Br0k3r sarebbero gestiti dallo stesso Br0k3r e non sarebbero collegati ad altri attori delle minacce. Ciò è dovuto al fatto che Br0k3r può creare fiducia nella sua clientela di criminali informatici. Si tratta di un servizio uno-a-molti e non di un mercato
APT33 risulta essere un gruppo sponsorizzato dallo Stato iraniano attivo almeno dal 2013 (alcune fonti citano però essere attivo dal 2017). Ha preso di mira organizzazioni negli Stati Uniti, in Arabia Saudita e in Corea del Sud, con una forte attenzione ai settori dell’aviazione e dell’energia. Date le sue capacità di attacco e la sovrapposizione di attività con altre minacce costanti iraniane e la vittimologia condivisa, si ipotizza essere un gruppo legato al Corpo delle guardie rivoluzionarie islamiche (IRGC).
L’APT33, come altri gruppi subordinati all’IRGC, si aggiudica contratti nel mondo IT per operare sotto le mentite spoglie di un’azienda privata (per questo APT il nome della azienda è “Danesh Novin Sahand”) per renderne più difficile il tracciamento delle attività / l’attribuzione.
Storicamente, APT33 è stato associato a campagne di hacking e leaking, come l’operazione Pay2Key (https://research.checkpoint.com/2020/ransomware-alert-pay2key/) alla fine del 2020, un’operazione di guerra informatica volta a minare la sicurezza informatica delle infrastrutture israeliane. Nel caso delle attività del gruppo APT33, sembra che si concentrino principalmente sul furto di credenziali e informazioni sensibili.
Br0k3r ora afferma sul sito web che “numerose bande di ransomware attive lavorano con me in una discreta percentuale [sic]”. Ciò evidenzia come Br0k3r esemplifichi il fatto che il rapporto tra gli operatori di ransomware e i broker di accesso iniziale (IAB) sia di reciproco vantaggio.
Lo Shop di Br0k3r consente agli operatori di ransomware di concentrarsi sul movimento laterale, sul furto di dati, sull’implementazione del payload del ransomware e sull’estorsione, anziché dedicare il proprio tempo al lungo lavoro per ottenere l’accesso alla rete. Gli operatori di ransomware forniscono inoltre un flusso di entrate costante a Br0k3r. Il costo dell’accesso è trascurabile rispetto al riscatto richiesto alle vittime, il che ha fatto esplodere il numero di offerte di vendita dell’accesso alle organizzazioni compromesse.
Secondo SANS, chi decide di acquistare accessi da Br0k3r. riceve anche un’anteprima della rete di cui sta comprando credenziali di accesso. Questa include i domini della vittima e un riepilogo dell’organizzazione della vittima tratto da ZoomInfo. Per dimostrare che l’accesso è legittimo, Br0k3r offre anche la prova dei privilegi di amministratore di dominio, del livello di accesso aziendale, delle dimensioni della rete e del sistema antivirus o di rilevamento e risposta degli endpoint (EDR) in uso. Una volta che il potenziale acquirente conferma di avere un portafoglio con fondi disponibili, l’affare viene concluso.
Queste attività di vendita di accessi puntano ad ampliare la portata delle minacce cyber da parte di attori con sede in Iran, riferisce il rapporto. All’inizio del 2024, FBI, CISA e il Dipartimento della Salute e dei Servizi Umani hanno aggiornato il loro allarme di sicurezza informatica su ALPHV (gang cliente dello IAB Br0k3r) per evidenziare nuovi indicatori di compromissione specificamente rivolti al settore sanitario. Nonostante i tentativi di FBI di interrompere le operazioni di gruppi di ransomware come ALPHV, questi gruppi continuano a rappresentare una minaccia significativa.
Motivazioni dello IAB
Spionaggio, sabotaggio, denaro.
Stati/Settori Target
USA, Israele, Azerbaidjan, Arabia Saudita, Corea del sud
Settori: Istituzioni finanziarie, Aviazione, Energia, Istruzione, Governo, Sanità
Vettori di attacco
Uso di proxy, Spearphishing, applicazioni rivolte al pubblico, messaggistica sui social media, pacchetti dannosi (NPM, Pip), Watering hole, attacchi alla Supply Chain
Tools & Malware
Wiper: Shamoon
Custom backdoor: Tickler, FalseFont
Remote Access Trojan: QuasarRAT
TOX id usati da Br0k3r
| TOX Id | TOX Public Key |
| xplfinder | ea2ec0c3859d8d8c36d95a298beef6d7add17856655bfbea2554b8714f 7c7c69 |
| Br0k3r | B761680E23F2EBB5F6887D315EBD05B2D7C365731E093B49ADB059 C3DCCAA30C |
Jabber/XMPP ID br0k3r[@]xmpp[.]jp
Pay2Key (Ottobre 2024)
Due dozzine di aziende israeliane sono state prese di mira nell’ottobre 2024: prove forensi collegano la campagna a Fox Kitten. JNS riporta che una di esse è collegata al sistema di difesa aerea di Israele noto con il nome Iron Dome: “Fox Kitten, nella campagna Pay2Key, ha affermato di essere riuscito a violare il sistema informatico della società Elta Systems, filiale di Israel Aerospace Industries (IAI), che ha sviluppato il radar utilizzato nel sistema di difesa missilistico Iron Dome; Fox Kitten/Br0k3r avrebbe diffuso dati sensibili sul dark web”.
“Knock Knock! Tonight is longer than longest night for @ILAerospaceIAI”
“Toc Toc! Questa notte è più lunga della notte più lunga per @ILAerospaceIAI”
ha twittato dopo l’attacco del 2024.
Panoramica delle tattiche, delle tecniche e delle procedure osservate secondo il rapporto CISA. Le intrusioni iniziali di questo attore iraniano si basano sullo sfruttamento di servizi esterni remoti su risorse esposte in Internet per ottenere l’accesso iniziale alle reti delle vittime.
A partire dal luglio 2024, questo attore è stato osservato scansionare indirizzi IP che ospitano gateway di sicurezza Check Point, alla ricerca di dispositivi potenzialmente vulnerabili a CVE2024-24919. Da aprile 2024, ha condotto una scansione di massa degli indirizzi IP che ospitano i sistemi PAN-OS e GlobalPOS di Palo Alto Networks: era molto probabilmente in atto una ricognizione ed un rilevamento di dispositivi vulnerabili a CVE-2024-3400. Storicamente, questo gruppo ha violato le aziende sfruttando CVE-2019-19781 e CVE-2023-3519 relative a Citrix Netscaler e CVE-2022-1388 relative ai dispositivi BIG-IP F5.
Ricognizione, accesso iniziale, persistenza e accesso alle credenziali
L’attore è stato osservato mentre utilizzava il motore di ricerca Shodan per identificare ed enumerare gli indirizzi IP che ospitano dispositivi vulnerabili a un particolare CVE. L’accesso iniziale degli attori è solitamente ottenuto sfruttando un dispositivo di rete esposto al pubblico, come Citrix Netscaler (CVE-2019-19781 e CVE-2023-3519), F5 BIG-IP (CVE-2022-1388), Pulse Secure/Ivanti VPN (CVE-2024-21887) e, più recentemente, PanOS (CVE-2024-3400).
Dopo aver violato i dispositivi vulnerabili, vengono utilizzate le seguenti tecniche:
Execution, Privilege Escalation, and Defense Evasion
Discovery
| Indicatore di Compromissione | Prima osservazione | Ultima osservazione ad agosto 2024 |
| 138.68.90[.]19 | January 2024 | August 2024 |
| 167.99.202[.]130 | January 2024 | August 2024 |
| 78.141.238[.]182 | July 2024 | August 2024 |
| 51.16.51[.]81 | January 2024 | August 2024 |
| 51.20.138[.]134 | February 2024 | August 2024 |
| 134.209.30[.]220 | March 2024 | August 2024 |
| 13.53.124[.]246 | February 2024 | August 2024 |
| api.gupdate[.]net | September 2022 | August 2024 |
| githubapp[.]net | February 2024 | August 2024 |
| 18.134.0[.]66 | September 2023 | November 2023 |
| 193.149.190[.]248 | September 2023 | January 2024 |
| 45.76.65[.]42 | September 2023 | December 2023 |
| 206.71.148[.]78 | October 2023 | January 2024 |
| 193.149.187[.]41 | October 2023 | November 2023 |
| login.forticloud[.]online | October 2023 | November 2023 |
| fortigate.forticloud.[]online | October 2023 | November 2023 |
| cloud.sophos[.]one | October 2023 | November 2023 |
Il rapporto CISA Iran-based Cyber Actors Enabling Ransomware Attacks on US Organizations | CISA contiene anche IoC in formato STYX scaricabili.
FBI e CISA raccomandano a tutte le organizzazioni di implementare le misure di mitigazione per migliorare la propria postura di sicurezza informatica in base alla attività del gruppo informatico iraniano. FBI ritiene che l’obiettivo del gruppo si basi principalmente sull’identificazione di dispositivi vulnerabili alle CVE citate quindi, qualsiasi organizzazione dovrebbe difendersi dallo sfruttamento delle vulnerabilità note con politiche di patching e sostituzione degli apparati e dei software deprecati/obsoleti soprattutto se esposti su IP pubblici.
Sono sempre da tenere in considerazione, inoltre, le best practice descritte nel precedente articolo sullo IAB miyako al paragrafo “Strategie di difesa contro gli IAB”:
Leet (a volte scritto come “1337” o “l33t”), noto anche come eleet o leetspeak, è un altro alfabeto per la lingua inglese o italiana (o altra lingua) utilizzato soprattutto su Internet. Utilizza varie combinazioni di caratteri ASCII per sostituire le lettere latine con numeri che assomigliano alle lettere o numeri che le possono ricordare.
Br0k3r … ricorda Broker … come m13l3, ricorda miele e scu014, scuola … un ottimo approcio per rendere più complicate le nostre password.
1337 41n’t s0 7rIckY!
Ti è piaciuto questo articolo? Ne stiamo discutendo nella nostra Community su LinkedIn, Facebook e Instagram. Seguici anche su Google News, per ricevere aggiornamenti quotidiani sulla sicurezza informatica o Scrivici se desideri segnalarci notizie, approfondimenti o contributi da pubblicare.

 Cybercrime
CybercrimeLe autorità tedesche hanno recentemente lanciato un avviso riguardante una sofisticata campagna di phishing che prende di mira gli utenti di Signal in Germania e nel resto d’Europa. L’attacco si concentra su profili specifici, tra…
 Innovazione
InnovazioneL’evoluzione dell’Intelligenza Artificiale ha superato una nuova, inquietante frontiera. Se fino a ieri parlavamo di algoritmi confinati dietro uno schermo, oggi ci troviamo di fronte al concetto di “Meatspace Layer”: un’infrastruttura dove le macchine non…
 Cybercrime
CybercrimeNegli ultimi anni, la sicurezza delle reti ha affrontato minacce sempre più sofisticate, capaci di aggirare le difese tradizionali e di penetrare negli strati più profondi delle infrastrutture. Un’analisi recente ha portato alla luce uno…
 Vulnerabilità
VulnerabilitàNegli ultimi tempi, la piattaforma di automazione n8n sta affrontando una serie crescente di bug di sicurezza. n8n è una piattaforma di automazione che trasforma task complessi in operazioni semplici e veloci. Con pochi click…
 Innovazione
InnovazioneArticolo scritto con la collaborazione di Giovanni Pollola. Per anni, “IA a bordo dei satelliti” serviva soprattutto a “ripulire” i dati: meno rumore nelle immagini e nei dati acquisiti attraverso i vari payload multisensoriali, meno…