
Un report di FortiGuard relativo alla prima metà del 2025 mostra che gli aggressori motivati economicamente stanno rinunciando sempre più a exploit e malware sofisticati. Invece di implementare strumenti utilizzano account validi e strumenti di accesso remoto legittimi per penetrare nelle reti aziendali senza essere rilevati.
Questo approccio si è dimostrato non solo più semplice ed economico, ma anche significativamente più efficace: gli attacchi che utilizzano password rubate sfuggono sempre più spesso al rilevamento.
Gli esperti riferiscono che nei primi sei mesi dell’anno hanno indagato su decine di incidenti in diversi settori, dalla produzione alla finanza e alle telecomunicazioni. L’analisi di questi casi ha rivelato uno schema ricorrente: gli aggressori ottengono l’accesso utilizzando credenziali rubate o acquistate , si connettono tramite VPN e quindi si muovono nella rete utilizzando strumenti di amministrazione remota come AnyDesk, Atera, Splashtop e ScreenConnect.
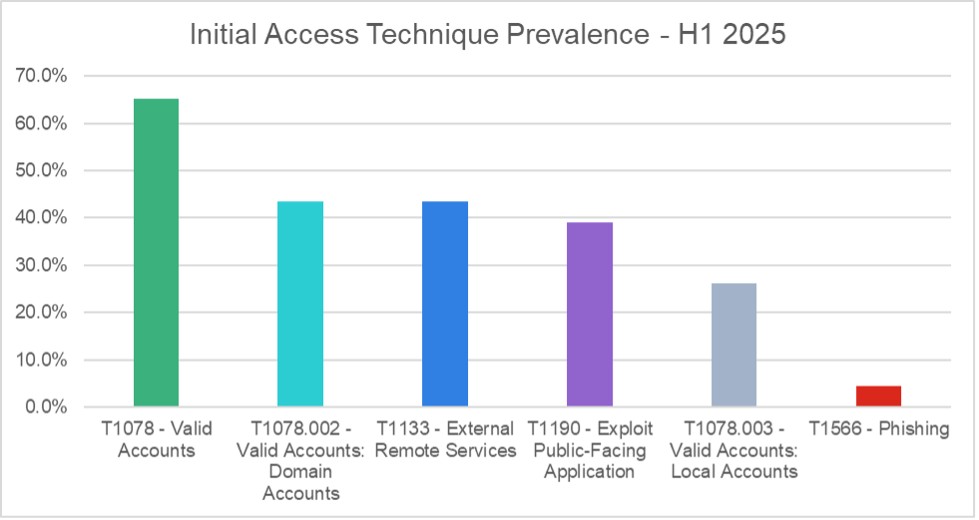
Questa strategia consente loro di mascherare la loro attività come attività di amministratore di sistema ed evitare sospetti. FortiGuard conferma questi risultati nello stesso periodo: le tendenze relative alle perdite di password documentate nei documenti open source corrispondono a quelle identificate durante le indagini interne. In sostanza, gli aggressori non devono “hackerare” i sistemi nel senso tradizionale del termine: accedono semplicemente utilizzando le credenziali di accesso di qualcun altro, spesso ottenute tramite phishing o infostealer venduti su piattaforme clandestine.
In un attacco analizzato, gli aggressori hanno utilizzato credenziali valide per connettersi a una VPN aziendale senza autenticazione a più fattori , quindi hanno estratto le password dell’hypervisor salvate dal browser dell’utente compromesso e hanno crittografato le macchine virtuali. In un altro caso, un operatore ha ottenuto l’accesso tramite un account di amministratore di dominio rubato e ha installato in massa AnyDesk sull’intera rete utilizzando RDP e criteri di gruppo, consentendogli di spostarsi tra i sistemi e di rimanere inosservato per periodi di tempo più lunghi. Ci sono stati anche casi in cui gli aggressori hanno sfruttato una vecchia vulnerabilità in un server esterno, implementato diversi strumenti di gestione remota e creato account di servizio fittizi per spostare e poi rubare documenti di nascosto.
L’analisi ha dimostrato che il furto di password rimane una delle strategie più economiche e accessibili. Il costo dell’accesso dipende direttamente dalle dimensioni e dall’area geografica dell’azienda: per le organizzazioni con oltre un miliardo di dollari di fatturato nei paesi sviluppati, può raggiungere i 20.000 dollari, mentre per le aziende più piccole nelle regioni in via di sviluppo, si aggira sulle centinaia di dollari. Le massicce campagne di infostealing forniscono un flusso costante di dati aggiornati e la bassa barriera all’ingresso rende tali attacchi appetibili anche per gruppi meno addestrati.
| Fatturato aziendale | economie sviluppate | Economie emergenti/in via di sviluppo |
|---|---|---|
| Oltre 1 miliardo di dollari USA | $ 10.000-20.000 USD | $ 3.000-6.000 USD |
| 500 milioni-1 miliardo di dollari USA | $ 4.000-8.000 USD | $ 1.000-5.000 USD |
| 100-500 milioni di dollari USA | $ 2.000-5.000 USD | $ 500-2.000 USD |
| Meno di 100 milioni di dollari USA | $ 500-1.500 USD | $ 100-500 USD |
Il vantaggio principale di questo schema è la furtività. Il comportamento degli aggressori è indistinguibile da quello dei dipendenti legittimi, soprattutto se si connettono durante il normale orario di lavoro e agli stessi sistemi.
Gli strumenti di sicurezza focalizzati sulla scansione di file dannosi e processi sospetti spesso non sono in grado di rilevare anomalie quando l’attacco si limita all’accesso di routine e alla navigazione in rete. Inoltre, quando si rubano manualmente dati tramite interfacce RDP o funzionalità RMM integrate, è difficile risalire ai file trasferiti, poiché tali azioni non lasciano artefatti di rete evidenti.
Secondo le osservazioni di FortiGuard, gli aggressori coinvolti in tali campagne continuano a utilizzare attivamente Mimikatz e le sue varianti per estrarre le password dalla memoria, e continuano a utilizzare l’exploit Zerologon per l’escalation dei privilegi. A volte, utilizzano anche manualmente utility come GMER, rinominate “strumenti di sistema”, per nascondere la propria presenza.
FortiGuard sottolinea che la protezione da tali minacce richiede un ripensamento degli approcci. Affidarsi esclusivamente ai tradizionali sistemi EDR che analizzano il codice dannoso non garantisce più una sicurezza affidabile. Una strategia basata sugli account e sul comportamento degli utenti sta diventando più efficace.
Le aziende devono creare i propri profili di attività normale e rispondere tempestivamente alle deviazioni, ad esempio accessi da posizioni geografiche insolite, connessioni simultanee a più server o attività al di fuori dell’orario di lavoro.
Si raccomanda particolare attenzione all’autenticazione a più fattori, non solo per il perimetro esterno, ma anche all’interno della rete. Anche se un aggressore ottiene una password, richiedere un’autenticazione aggiuntiva ne rallenterà i progressi e creerà maggiori possibilità di essere individuato. È inoltre importante limitare i privilegi di amministratore, impedire l’uso di account privilegiati tramite VPN e monitorarne gli spostamenti all’interno dell’infrastruttura.
FortiGuard consiglia alle organizzazioni di controllare rigorosamente l’uso di strumenti di amministrazione remota. Se tali programmi non sono necessari per motivi aziendali, è opportuno bloccarli e monitorare eventuali nuove installazioni o connessioni di rete ad essi associate. Inoltre, si consiglia di disabilitare SSH, RDP e WinRM su tutti i sistemi in cui non sono necessari e di configurare avvisi per la riattivazione di questi servizi. Secondo gli analisti, tali misure possono rilevare anche tentativi nascosti di spostamento laterale all’interno della rete.
Ti è piaciuto questo articolo? Ne stiamo discutendo nella nostra Community su LinkedIn, Facebook e Instagram. Seguici anche su Google News, per ricevere aggiornamenti quotidiani sulla sicurezza informatica o Scrivici se desideri segnalarci notizie, approfondimenti o contributi da pubblicare.

 Cybercrime
CybercrimeLe autorità tedesche hanno recentemente lanciato un avviso riguardante una sofisticata campagna di phishing che prende di mira gli utenti di Signal in Germania e nel resto d’Europa. L’attacco si concentra su profili specifici, tra…
 Innovazione
InnovazioneL’evoluzione dell’Intelligenza Artificiale ha superato una nuova, inquietante frontiera. Se fino a ieri parlavamo di algoritmi confinati dietro uno schermo, oggi ci troviamo di fronte al concetto di “Meatspace Layer”: un’infrastruttura dove le macchine non…
 Cybercrime
CybercrimeNegli ultimi anni, la sicurezza delle reti ha affrontato minacce sempre più sofisticate, capaci di aggirare le difese tradizionali e di penetrare negli strati più profondi delle infrastrutture. Un’analisi recente ha portato alla luce uno…
 Vulnerabilità
VulnerabilitàNegli ultimi tempi, la piattaforma di automazione n8n sta affrontando una serie crescente di bug di sicurezza. n8n è una piattaforma di automazione che trasforma task complessi in operazioni semplici e veloci. Con pochi click…
 Innovazione
InnovazioneArticolo scritto con la collaborazione di Giovanni Pollola. Per anni, “IA a bordo dei satelliti” serviva soprattutto a “ripulire” i dati: meno rumore nelle immagini e nei dati acquisiti attraverso i vari payload multisensoriali, meno…