Il rilascio di Hexstrike-AI segna un punto di svolta nel panorama della sicurezza informatica. Il framework, presentato come uno strumento di nuova generazione per red team e ricercatori, è in grado di orchestrare oltre 150 agenti di intelligenza artificiale specializzati, capaci di condurre in autonomia scansioni, sfruttamento e persistenza sugli obiettivi. A poche ore dalla sua diffusione, però, è stato oggetto di discussioni nel dark web, dove diversi attori hanno tentato di impiegarlo per colpire vulnerabilità zero-day, con l’obiettivo di installare webshell per l’esecuzione di codice remoto non autenticato.
Hexstrike-AI era stato presentato come un “rivoluzionario framework di sicurezza offensiva basato sull’intelligenza artificiale”, pensato per combinare strumenti professionali e agenti autonomi. Tuttavia, il suo rilascio ha rapidamente suscitato interesse tra i malintenzionati, che hanno discusso del suo impiego per sfruttare tre vulnerabilità critiche di Citrix NetScaler ADC e Gateway, rivelate il 26 agosto. In poche ore, uno strumento destinato a rafforzare la difesa è stato trasformato in un motore di sfruttamento reale.
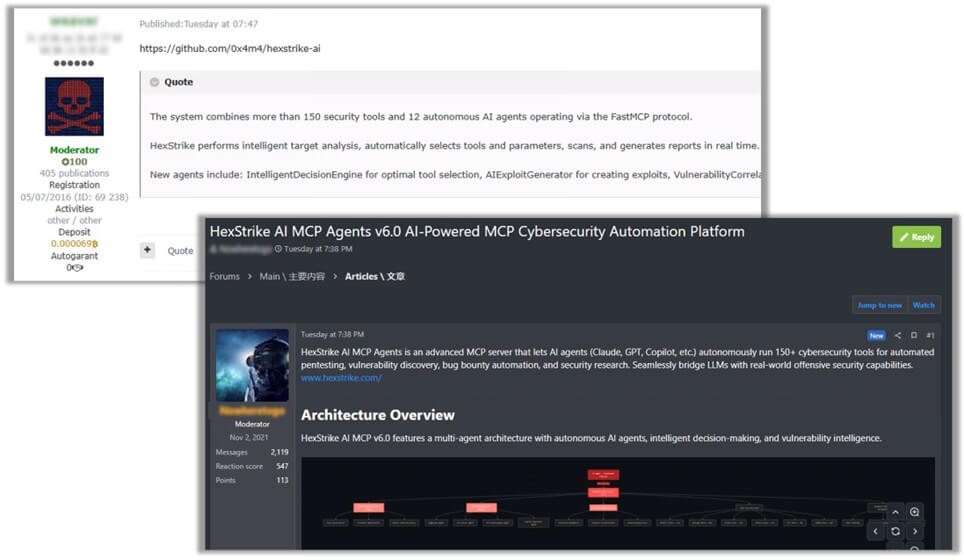
L’architettura del framework si distingue per il suo livello di astrazione e orchestrazione, che permette a modelli come GPT, Claude e Copilot di gestire strumenti di sicurezza senza supervisione diretta. Il cuore del sistema è rappresentato dai cosiddetti MCP Agents, che collegano i modelli linguistici alle funzioni offensive. Ogni strumento, dalla scansione Nmap ai moduli di persistenza, viene incapsulato in funzioni richiamabili, rendendo fluida l’integrazione e l’automazione. Il framework è inoltre dotato di logiche di resilienza, capaci di garantire la continuità operativa anche in caso di errori.
Particolarmente rilevante, riporta l’articolo di Check Point, è la capacità del sistema di tradurre comandi generici in flussi di lavoro tecnici, riducendo drasticamente la complessità per gli operatori. Questo elimina la necessità di lunghe fasi manuali e permette di trasformare istruzioni come “sfrutta NetScaler” in sequenze precise e adattive di azioni. In tal modo, operazioni complesse vengono rese accessibili e ripetibili, abbattendo la barriera di ingresso per chi intende sfruttare vulnerabilità avanzate.
Il tempismo del rilascio amplifica i rischi. Citrix ha infatti reso note tre vulnerabilità zero-day: la CVE-2025-7775, già sfruttata in natura con webshell osservate su sistemi compromessi; la CVE-2025-7776, un difetto di gestione della memoria ad alto rischio; e la CVE-2025-8424, relativa al controllo degli accessi nelle interfacce di gestione. Tradizionalmente, lo sfruttamento di queste falle avrebbe richiesto settimane di sviluppo e conoscenze avanzate. Con Hexstrike-AI, invece, i tempi si riducono a pochi minuti e le azioni possono essere parallelizzate su vasta scala.
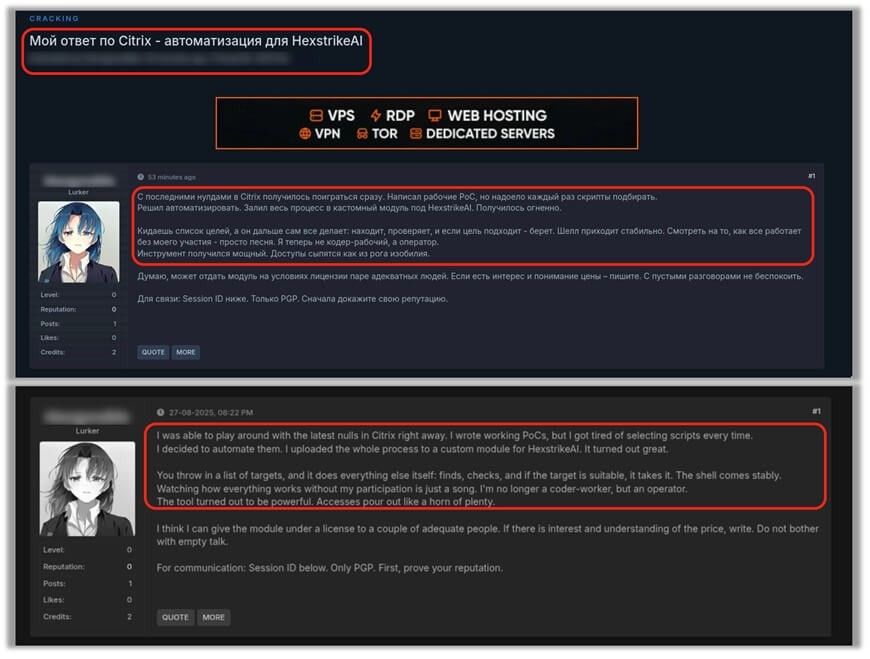
Le conseguenze sono già visibili: nelle ore successive alla divulgazione dei CVE, diversi forum sotterranei hanno riportato discussioni su come usare il framework per individuare e sfruttare istanze vulnerabili. Alcuni attori hanno persino messo in vendita i sistemi compromessi, segnalando un salto qualitativo nella rapidità e nella commercializzazione delle intrusioni. Tra i rischi principali vi è la riduzione drastica della finestra temporale tra divulgazione e sfruttamento di massa, che rende urgente un cambio di paradigma nella difesa.
Le mitigazioni suggerite indicano un percorso chiaro. È fondamentale applicare senza indugi le patch rilasciate da Citrix e rafforzare autenticazioni e controlli di accesso. Allo stesso tempo, le organizzazioni sono chiamate a evolvere le proprie difese adottando rilevamento adattivo, intelligenza artificiale difensiva, pipeline di patching più rapide e un monitoraggio costante delle discussioni nel dark web. In aggiunta, viene raccomandata la progettazione di sistemi resilienti, basati su segmentazione, privilegi minimi e capacità di ripristino, così da ridurre l’impatto di eventuali compromissioni.
Ti è piaciuto questo articolo? Ne stiamo discutendo nella nostra Community su LinkedIn, Facebook e Instagram. Seguici anche su Google News, per ricevere aggiornamenti quotidiani sulla sicurezza informatica o Scrivici se desideri segnalarci notizie, approfondimenti o contributi da pubblicare.

 Cybercrime
CybercrimeLe autorità tedesche hanno recentemente lanciato un avviso riguardante una sofisticata campagna di phishing che prende di mira gli utenti di Signal in Germania e nel resto d’Europa. L’attacco si concentra su profili specifici, tra…
 Innovazione
InnovazioneL’evoluzione dell’Intelligenza Artificiale ha superato una nuova, inquietante frontiera. Se fino a ieri parlavamo di algoritmi confinati dietro uno schermo, oggi ci troviamo di fronte al concetto di “Meatspace Layer”: un’infrastruttura dove le macchine non…
 Cybercrime
CybercrimeNegli ultimi anni, la sicurezza delle reti ha affrontato minacce sempre più sofisticate, capaci di aggirare le difese tradizionali e di penetrare negli strati più profondi delle infrastrutture. Un’analisi recente ha portato alla luce uno…
 Vulnerabilità
VulnerabilitàNegli ultimi tempi, la piattaforma di automazione n8n sta affrontando una serie crescente di bug di sicurezza. n8n è una piattaforma di automazione che trasforma task complessi in operazioni semplici e veloci. Con pochi click…
 Innovazione
InnovazioneArticolo scritto con la collaborazione di Giovanni Pollola. Per anni, “IA a bordo dei satelliti” serviva soprattutto a “ripulire” i dati: meno rumore nelle immagini e nei dati acquisiti attraverso i vari payload multisensoriali, meno…