
Il malware Industroyer, noto anche come Crashoverride, era un framework sviluppato da hacker russi, distribuito nel 2016 contro la rete elettrica dell’Ucraina. L’attacco lasciò Kiev per un’ora senza energia elettrica.
Il malware venne considerato un’evoluzione di precedenti ceppi come Havex e BlackEnergy, che erano stati utilizzati in precedenza sempre contro le reti elettriche. Tuttavia, a differenza di Havex e BlackEnergy (che erano più simili a malware generici di Windows distribuiti contro sistemi che gestiscono sistemi industriali), Industroyer conteneva componenti appositamente progettati per interagire con le apparecchiature della rete elettrica Siemens
Sei mesi dopo un attacco di hacking che ha causato un blackout a Kiev, in Ucraina, i ricercatori della sicurezza hanno avvertito che il malware utilizzato nell’attacco sarebbe stato “facile” da convertire in altri attacchi ad altre reti elettriche nel mondo.
La scoperta del malware, soprannominato “Industroyer” o “Crash Override”, evidenzia la vulnerabilità delle infrastrutture critiche, solo pochi mesi dopo che il ransomware WannaCry ha mietuto vittime in tutto il globo.
Industroyer, analizzato dai ricercatori della slovacca ESET e della statunitense Dragos, è solo il secondo caso noto di virus costruito e rilasciato appositamente per interrompere i sistemi di controllo industriale. Il primo conosciuto è stato Stuxnet, un worm che ha sabotato il programma nucleare iraniano, che si pensa fosse stato costruito dalla collaborazione tra Stati Uniti ed Israele, anche se non sono presenti fonti ufficiali.
Sei mesi dopo un attacco di hacking che ha causato un blackout a Kiev, in Ucraina, i ricercatori della sicurezza hanno avvertito che il malware utilizzato nell’attacco sarebbe stato “facile” da convertire in infrastrutture paralizzanti in altre nazioni.
La scoperta del malware, soprannominato “Industroyer” e “Crash Override”, evidenzia la vulnerabilità dell’infrastruttura critica, pochi mesi dopo che il ransomware WannaCry ha eliminato i computer NHS in tutto il Regno Unito.
Industroyer, analizzato dai ricercatori della slovacca ESET e della statunitense Dragos, è solo il secondo caso noto di virus costruito e rilasciato appositamente per interrompere i sistemi di controllo industriale. Il primo è stato Stuxnet, un worm che ha sabotato il programma nucleare iraniano , che si pensava fosse stato costruito dagli Stati Uniti e da Israele.
Il virus attacca le sottostazioni elettriche e gli interruttori dei circuiti utilizzando protocolli di comunicazione industriale standardizzati su una serie di tipi di infrastrutture critiche, dall’alimentazione elettrica, acqua e gas al controllo dei trasporti.
Questi protocolli di controllo risalgono a decenni fa, molto prima che le pratiche di sicurezza come la crittografia e l’autenticazione fossero state standardizzate. La loro unica caratteristica è quella di essere attivi anche su reti che non sono direttamente connesse a Internet (reti airgap).
Il malware Industroyer è stato utilizzato in un massiccio attacco informatico in Ucraina il 17 dicembre 2016; l’attacco a tempo ha preso di mira le sottostazioni di distribuzione dell’elettricità a Kiev e ha assunto il controllo degli interruttori di circuito negli ICS per tagliare l’elettricità, portando a sostanziali blackout che sono durati molte ore. “Con ciò, si è unito a un club d’élite di sole tre famiglie di malware note per essere utilizzate negli attacchi contro ICS”, quali BlackEnergy, Stuxnet e Havex.
L’incidente non deve essere confuso con un altro attacco informatico che ha preso di mira l’Ucraina nel dicembre 2015, che ha anche interrotto l’alimentazione elettrica a vaste aree dell’Ucraina occidentale. Questi incidenti sono stati causati da un altro malware ICS chiamato BlackEnergy.
Ma la cosa che Industroyer riuscì a far comprendere, in particolare rispetto ai vasti blackout causati da un altro attacco informatico un anno prima, è che tutto questo poteva avvenire in modo automatico.
Gli attacchi precedenti, sebbene più dannosi, hanno richiesto il controllo umano per poter generare i disservizi attesi, al contrario, Industroyer ha causato tutto questo in modo automatico portando una grande capitale ad un’ora di blackout. Ciò ha portato alcuni a chiedersi se l’attacco di Kiev fosse più un test per vedere se il malware avrebbe funzionato nella pratica o qualcosa di simile. Ma a prescindere, afferma Anton Cherepanov, ricercatore senior di malware presso l’azienda ESET :
“dovrebbe servire da campanello d’allarme per i responsabili della sicurezza dei sistemi critici di tutto il mondo”.
Oltre alle sue funzioni di attacco, Industroyer ha anche la capacità di danneggiare il PC di controllo stesso, rendendolo non avviabile e quindi potenzialmente allungando di fatto il blackout.
Il Dipartimento della sicurezza interna degli Stati Uniti ha affermato che stava indagando sul malware, sebbene non avesse riscontrato prove che suggerissero che avesse infettato l’infrastruttura critica degli Stati Uniti. Non è stata confermata alcuna attribuzione specifica per l’attacco di Kiev, ma il governo ucraino ha incolpato la Russia, come ha fatto per gli attacchi del 2015. I funzionari di Mosca hanno ripetutamente negato la responsabilità.

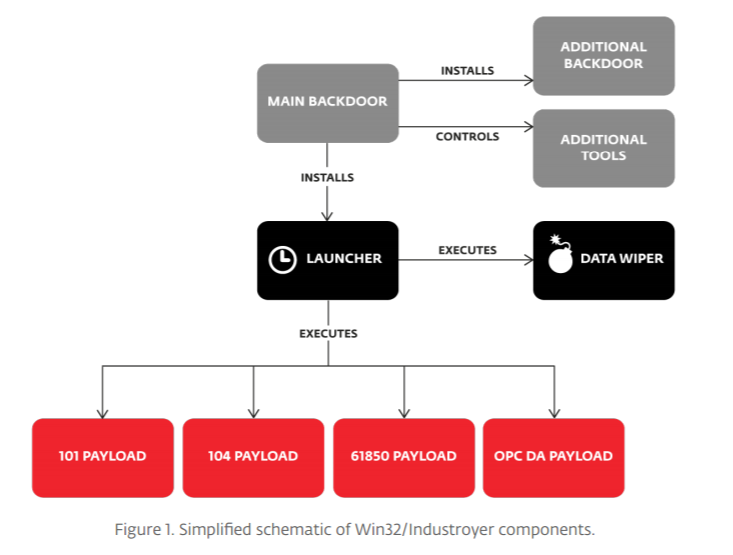
Industroyer, è un sofisticato malware modulare che include diversi componenti come una backdoor, un launcher, un data wiper, almeno quattro payload e molti altri strumenti. Gli esperti hanno concentrato la loro analisi sui payload (IEC 60870-5-101 (alias IEC 101), IEC 60870-5-104 (alias IEC 104), IEC 61850, OLE for Process Control Data Access (OPC DA)) i componenti principali del malware negli attacchi che consentono di controllare gli interruttori elettrici.
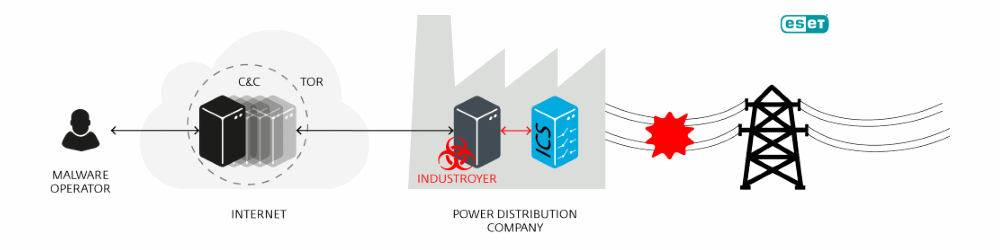
La backdoor di Industroyer consente agli aggressori di eseguire vari comandi sul sistema, mentre il server C&C è nascosto nella rete Tor e può essere programmato per essere attivo solo in determinati momenti, rendendo difficile il suo rilevamento. La backdoor installa il componente di avvio, che avvia il wiper e i payload, inoltre rilascia una seconda backdoor mascherata da una versione trojanizzata dell’applicazione Blocco note di Windows.
Il componente wiper viene utilizzato nella fase finale dell’attacco per nascondere le tracce e rendere difficile il ripristino dei sistemi mirati. I payload consentono al malware di controllare gli interruttori ed implementa protocolli di comunicazione industriale. I ricercatori di ESET ritengono che gli sviluppatori del malware abbiano una profonda conoscenza delle operazioni della rete elettrica e delle comunicazioni della rete industriale per poter aver progettato un malware di tale caratura.
“Oltre a tutto ciò, gli autori del malware hanno anche scritto uno strumento che implementa un attacco denial-of-service (DoS) contro una particolare famiglia di relè di protezione, in particolare la gamma Siemens SIPROTEC”
Ha detto la ESET.
“Le capacità di questo malware sono significative. Rispetto al set di strumenti utilizzato dagli attori delle minacce negli attacchi del 2015 contro la rete elettrica ucraina che sono culminati in un black out il 23 dicembre 2015 (BlackEnergy, KillDisk e altri componenti, incluso un legittimo software di accesso remoto), la banda dietro Industroyer è più avanzata, dal momento che hanno fatto di tutto per creare malware in grado di controllare direttamente interruttori e interruttori automatici”
Sia ESET che Dragos hanno raccolto prove che suggeriscono che Industroyer sia stato coinvolto nelle interruzioni di corrente del 2016 nella regione di Kiev , attribuite agli hacker sponsorizzati dallo stato russo.

Industroyer è un malware altamente personalizzabile. Pur essendo universale, in quanto può essere utilizzato per attaccare qualsiasi sistema di controllo industriale utilizzando alcuni dei protocolli di comunicazione mirati, alcuni dei componenti nei campioni analizzati sono stati progettati per prendere di mira un particolare hardware.
I ricercatori di Dragos, un’azienda specializzata in sicurezza dei sistemi di controllo industriale (ICS), ritengono che il gruppo ELECTRUM APT sia direttamente collegato al gruppo Sandworm APT , ESET ha evidenziato che sebbene non vi siano somiglianze di codice tra il malware utilizzato negli attacchi del 2015 e del 2016 in Ucraina, alcuni componenti sono concettualizzati.
ELECTRUM APT è un gruppo ancora attivo, sebbene le prove suggeriscano che il gruppo non si concentri più esclusivamente sull’Ucraina. L’attività in corso del gruppo e il collegamento al team SANDWORM indicano che ELECTRUM potrebbe arrecare danni anche in altre aree geografiche. Dragos considera ELECTRUM uno dei gruppi di minacce più competenti e sofisticati attualmente in circolazione nel settore ICS.
Ti è piaciuto questo articolo? Ne stiamo discutendo nella nostra Community su LinkedIn, Facebook e Instagram. Seguici anche su Google News, per ricevere aggiornamenti quotidiani sulla sicurezza informatica o Scrivici se desideri segnalarci notizie, approfondimenti o contributi da pubblicare.

 Cybercrime
CybercrimeLe autorità tedesche hanno recentemente lanciato un avviso riguardante una sofisticata campagna di phishing che prende di mira gli utenti di Signal in Germania e nel resto d’Europa. L’attacco si concentra su profili specifici, tra…
 Innovazione
InnovazioneL’evoluzione dell’Intelligenza Artificiale ha superato una nuova, inquietante frontiera. Se fino a ieri parlavamo di algoritmi confinati dietro uno schermo, oggi ci troviamo di fronte al concetto di “Meatspace Layer”: un’infrastruttura dove le macchine non…
 Cybercrime
CybercrimeNegli ultimi anni, la sicurezza delle reti ha affrontato minacce sempre più sofisticate, capaci di aggirare le difese tradizionali e di penetrare negli strati più profondi delle infrastrutture. Un’analisi recente ha portato alla luce uno…
 Vulnerabilità
VulnerabilitàNegli ultimi tempi, la piattaforma di automazione n8n sta affrontando una serie crescente di bug di sicurezza. n8n è una piattaforma di automazione che trasforma task complessi in operazioni semplici e veloci. Con pochi click…
 Innovazione
InnovazioneArticolo scritto con la collaborazione di Giovanni Pollola. Per anni, “IA a bordo dei satelliti” serviva soprattutto a “ripulire” i dati: meno rumore nelle immagini e nei dati acquisiti attraverso i vari payload multisensoriali, meno…