IEEE 802.11 wireless networks, better known as Wi-Fi, are the beating heart of modern connectivity. From a niche solution for home use to a technological cornerstone for the Internet of Things (IoT), smart cities, and enterprise infrastructure, Wi-Fi has evolved unstoppably. Today, in 2025, the arrival of Wi-Fi 7 (IEEE 802.11be) brings theoretical speeds of over 46 Gbps and latencies of less than a millisecond, but with it comes new challenges: security, interference, and spectrum management.
In this article, part of Red Hot Cyber’s Wi-Fi series, we analyze the fundamentals of IEEE 802.11 networks, exploring their architecture, signal behavior, advantages, and limitations. The goal is to understand not only the potential of Wi-Fi 7 but also the emerging challenges, particularly those related to cybersecurity and spectrum management.
Imagine a world without Wi-Fi: no connected smartphones, no smart homes, no offices without tangled cables. Wi-Fi has conquered the planet thanks to four strengths:
But all that glitters is not gold. Transmission via radio waves makes it vulnerable: an attacker with a directional antenna can intercept signals from a distance, and even WPA3 isn’t immune to sophisticated exploits. Then there’s interference—microwaves and Bluetooth congest the 2.4 GHz band, while the 6 GHz band requires advanced strategies to avoid overlap. Finally, range: regulations like those of the ETSI (20-30 dBm) limit coverage to 100-200 meters outdoors, and indoors a concrete wall can halve that.

Wi-Fi is based on a cellular architecture, the Service Sets , which define how devices talk to each other:
IBSS (Ad Hoc): Direct communication between devices
In an Independent Basic Service Set (IBSS) network, there is no Access Point (AP): devices connect directly to each other. This scheme, also known as Ad Hoc mode , is useful for emergency scenarios or temporary networks.
Example : Industrial sensors in a factory or remote drilling site can use IBSS to exchange data directly, without the need for a complex network architecture.
Operation : The sensors connect in Ad Hoc mode , transmitting critical information to each other to generate a local alert in case of danger.
In the Basic Service Set (BSS) , an AP acts as a coordinator , managing Wi-Fi clients and optimizing communication. This model is standard for home and business environments.
Example : Wi-Fi 6 network for small offices , with a single AP that uses OFDMA (Orthogonal Frequency-Division Multiple Access) and MU-MIMO to handle multiple simultaneous connections, assigning portions of spectrum more efficiently.

The Extended Service Set (ESS) connects multiple BSSs through a Distribution System (DS) , usually via Ethernet or wireless backhaul. It is the model used to ensure uninterrupted coverage over large areas.
Example :
In 2025, Wi-Fi 7 raises the bar: MLO allows you to use multiple bands in parallel, reducing latency and increasing reliability. The result? A device can switch from 2.4 GHz (long range) to 6 GHz (high capacity) without you even noticing. Add 320 MHz channels and bidirectional MU-MIMO, and you have a network that can handle up to 50 devices in a room without a hitch.
After seeing how Wi-Fi architecture with IBSS, BSS and ESS works to ensure connectivity and seamless roaming, the natural question is: what physically happens to the signal as we move from one Access Point to another?
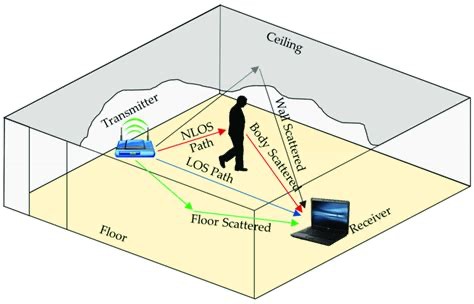
Wi-Fi isn’t just software and networks, but electromagnetic waves that must overcome distances and obstacles to connect devices. Its frequencies operate in the ISM (2.4 and 5 GHz) and U-NII (6 GHz) bands, and their propagation is governed by precise physical laws. Frequency dictates everything: at 2.4 GHz, the wavelength is 12.5 cm, ideal for passing through walls; at 6 GHz, it drops to 5 cm, perfect for speed but fragile against obstacles.
The received power drops with distance according to the inverse square law:
Pr=(4πR)2Pt
Add absorption (10-15 dB for a concrete wall) and reflections, and you understand why the signal drops out at 50 meters indoors. But there are tricks: beamforming focuses the waves like a lighthouse, and OFDM splits the data into subchannels to avoid interference. Wi-Fi 7 takes things further, with 4096-QAM that crams more bits into each symbol, increasing throughput by 20% compared to Wi-Fi 6.
In 2025, Wi-Fi 7 is the new gold standard, taking wireless connectivity to new heights:
The result? You can stream 8K, manage an army of IoT devices, and work remotely without lag. But there’s a price: more APs mean more costs, and security must keep pace with increasingly sophisticated threats.

Wi-Fi is powerful, but it’s also vulnerable if not properly secured. WPA3 represents a step forward, but threats persist:
MLO helps distribute traffic and reduce risks, but without encryption and proper segmentation, a compromised access point can act as a Trojan horse . Furthermore, the spread of the 6 GHz band will lead to increased device density, necessitating the adoption of AI algorithms for dynamic interference management and real-time channel optimization .
The IEEE 802.11 protocol is an engineering masterpiece that has made Wi-Fi synonymous with speed, flexibility, and ubiquity . With Wi-Fi 7 , the future of connectivity enters a new era, but not without compromises:
For those involved in cybersecurity and network management , the message is clear: design with foresight, secure every layer, and prepare for an increasingly wireless – and increasingly risk-prone – world.
Follow us on our WiFi Column to stay up to date!
References :
[1] IEEE (2024). Wi-Fi 7 Technical Overview .
[2] Higher Order Feature Extraction and Selection for Robust Human Gesture Recognition using CSI of COTS Wi-Fi Devices https://www.mdpi.com/1424-8220/19/13/2959
Follow us on Google News to receive daily updates on cybersecurity. Contact us if you would like to report news, insights or content for publication.
