
Una recente analisi di Cyber Threat Intelligence (CTI) condotta da DREAM ha svelato i dettagli di una complessa campagna di spear-phishing avvenuta nell’agosto 2025. L’attacco, attribuito a un gruppo allineato all’Iran, noto come Homeland Justice, ha sfruttato un’infrastruttura già compromessa per raggiungere obiettivi sensibili a livello globale. La peculiarità di questa operazione risiede nell’utilizzo di un account di posta elettronica violato appartenente al Ministero degli Affari Esteri dell’Oman, che ha fornito una copertura di legittimità per le comunicazioni malevole.
Le e-mail di phishing contenevano un allegato dannoso, un documento di Microsoft Word, che rappresentava il primo anello della catena di infezione. All’interno di questo file si nascondeva una macro VBA (Visual Basic for Applications) appositamente codificata per eludere i controlli di sicurezza standard. Una volta attivata, la macro procedeva con la decodifica e l’installazione di un payload, un file eseguibile battezzato come sysProcUpdate.exe, che rappresentava il cuore dell’attacco informatico.
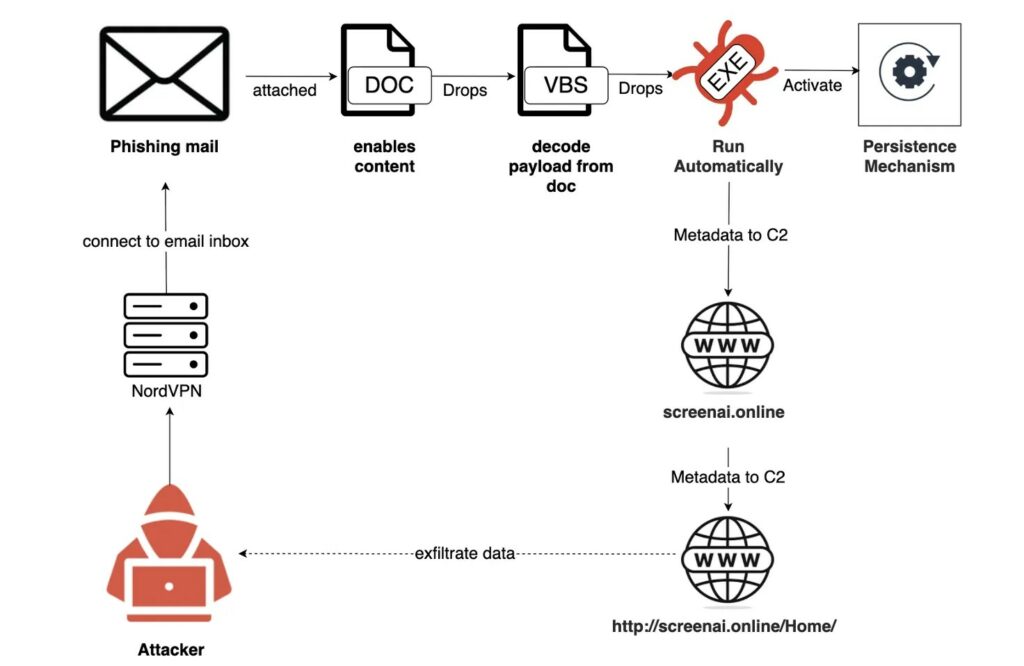
Il malware sysProcUpdate.exe era progettato per svolgere un’attività di ricognizione dettagliata del sistema compromesso. Il suo compito principale era quello di raccogliere metadati specifici del sistema, tra cui informazioni sulla configurazione e sui software installati. Questi dati venivano successivamente crittografati per garantirne la riservatezza e poi trasmessi in modo sicuro a un server di comando e controllo (C2), da cui gli aggressori potevano gestire la campagna e ricevere le informazioni esfiltrate.
Per sfuggire ai sistemi di difesa e all’analisi, gli attaccanti hanno implementato diverse tecniche di evasione sofisticate. Hanno occultato la propria origine instradando il traffico attraverso un nodo di uscita VPN in Giordania, rendendo difficile la loro localizzazione. Inoltre, il payload dannoso veniva scritto in un file con estensione .log, un formato di file generalmente non associato al malware, con l’obiettivo di eludere i controlli automatici. L’uso di ritardi nel codice contribuiva ulteriormente a confondere i sistemi di analisi comportamentale.

I principali obiettivi di questa campagna erano istituzioni diplomatiche e governative. L’attacco ha preso di mira entità in un’ampia varietà di aree geografiche, inclusi il Medio Oriente, l’Africa, l’Europa, l’Asia e le Americhe. Per l’Europa i paesi colpiti sono Italia, Francia Romania, Spagna, Paesi Bassi, Ungheria, Germania, Austria, e Svezia. La campagna dimostra una chiara preferenza per obiettivi di alto valore, mirati a ottenere informazioni strategiche attraverso l’accesso a reti di governi e organizzazioni internazionali, sottolineando la natura politica o geopolitica della minaccia.
Per mitigare l’attacco, gli esperti di sicurezza consigliano diverse contromisure tecniche. La prima e più immediata è il blocco degli Indicatori di Compromissione (IOC), come gli indirizzi IP dei server C2 e gli hash dei file dannosi. Un’altra raccomandazione cruciale è il monitoraggio proattivo delle richieste POST sospette dirette ai server C2 e la verifica delle modifiche al registro di Windows, che possono segnalare l’attività del malware.
Tra le altre misure di mitigazione, viene sottolineata l’importanza di imporre la sicurezza delle macro nei programmi di Office per prevenire l’esecuzione di codice arbitrario. Si suggerisce inoltre di condurre un’analisi approfondita del traffico VPN in uscita, al fine di identificare eventuali flussi di dati anomali. Infine, l’implementazione della segmentazione della rete è vista come una difesa efficace per limitare la propagazione del malware e ridurre l’impatto di attacchi simili in futuro.
Ti è piaciuto questo articolo? Ne stiamo discutendo nella nostra Community su LinkedIn, Facebook e Instagram. Seguici anche su Google News, per ricevere aggiornamenti quotidiani sulla sicurezza informatica o Scrivici se desideri segnalarci notizie, approfondimenti o contributi da pubblicare.

 Cybercrime
CybercrimeLe autorità tedesche hanno recentemente lanciato un avviso riguardante una sofisticata campagna di phishing che prende di mira gli utenti di Signal in Germania e nel resto d’Europa. L’attacco si concentra su profili specifici, tra…
 Innovazione
InnovazioneL’evoluzione dell’Intelligenza Artificiale ha superato una nuova, inquietante frontiera. Se fino a ieri parlavamo di algoritmi confinati dietro uno schermo, oggi ci troviamo di fronte al concetto di “Meatspace Layer”: un’infrastruttura dove le macchine non…
 Cybercrime
CybercrimeNegli ultimi anni, la sicurezza delle reti ha affrontato minacce sempre più sofisticate, capaci di aggirare le difese tradizionali e di penetrare negli strati più profondi delle infrastrutture. Un’analisi recente ha portato alla luce uno…
 Vulnerabilità
VulnerabilitàNegli ultimi tempi, la piattaforma di automazione n8n sta affrontando una serie crescente di bug di sicurezza. n8n è una piattaforma di automazione che trasforma task complessi in operazioni semplici e veloci. Con pochi click…
 Innovazione
InnovazioneArticolo scritto con la collaborazione di Giovanni Pollola. Per anni, “IA a bordo dei satelliti” serviva soprattutto a “ripulire” i dati: meno rumore nelle immagini e nei dati acquisiti attraverso i vari payload multisensoriali, meno…