
Gli aggressori hanno iniziato a utilizzare un trucco insolito per mascherare i link di phishing, facendoli apparire come indirizzi di Booking.com. La nuova campagna malware utilizza il carattere hiragana giapponese “ん” (U+3093). In alcuni font e interfacce, assomiglia visivamente a una barra, facendo apparire l’URL come un normale percorso sul sito, sebbene in realtà conduca a un dominio falso.
Il ricercatore JAMESWT ha scoperto che nelle e-mail di phishing il collegamento si presenta così:
https://admin.booking.com/hotel/hoteladmin/…
ma in realtà indirizza l’utente a un indirizzo del tipo
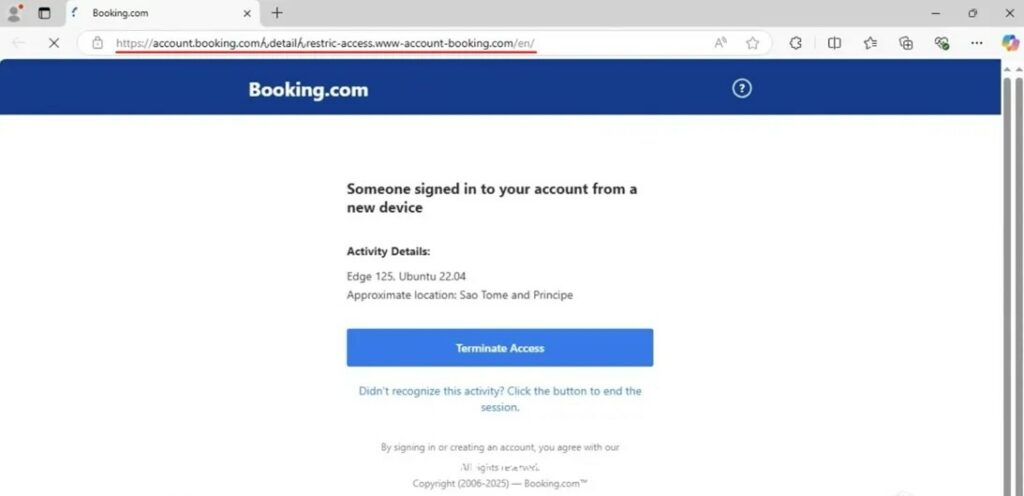
https://account.booking.comんdetailんrestric-access.www-account-booking.com/en/.
Tutto ciò che precede “www-account-booking[.]com” è solo un sottodominio che imita la struttura del sito reale. Il vero dominio registrato appartiene agli aggressori. Cliccandoci sopra, la vittima finisce sulla pagina
www-account-booking[.]com/c.php?a=0
da cui viene scaricato un file MSI dannoso dal nodo CDN updatessoftware.b-cdn[.]net.
Secondo l’analisi di MalwareBazaar e ANY.RUN , il programma di installazione distribuisce componenti aggiuntivi, probabilmente infostealer o strumenti di accesso remoto.
La tecnica si basa sull’uso di omoglifi ovvero simboli che sembrano altri ma appartengono ad altri alfabeti o set Unicode. Tali simboli sono spesso utilizzati in attacchi omografi e phishing. Un esempio è la “O” cirillica (U+041E), che è quasi indistinguibile dalla “O” latina (U+004F). Nonostante gli sviluppatori di browser e servizi aggiungano protezioni contro tali sostituzioni, gli attacchi continuano a verificarsi.
Non è la prima volta che Booking.com diventa un’esca per il phishing. A marzo, Microsoft Threat Intelligence ha segnalato email mascherate da servizio di prenotazione che utilizzavano la tecnica ClickFix per infettare i computer dei dipendenti degli hotel. E ad aprile, i ricercatori di Malwarebytes hanno segnalato uno schema simile.
Tuttavia, l’uso di omoglifi come “ん” può ingannare anche gli utenti più attenti, quindi è importante integrare la cautela con un software antivirus aggiornato in grado di bloccare il download di contenuti dannosi.
Ti è piaciuto questo articolo? Ne stiamo discutendo nella nostra Community su LinkedIn, Facebook e Instagram. Seguici anche su Google News, per ricevere aggiornamenti quotidiani sulla sicurezza informatica o Scrivici se desideri segnalarci notizie, approfondimenti o contributi da pubblicare.

 Cybercrime
CybercrimeLe autorità tedesche hanno recentemente lanciato un avviso riguardante una sofisticata campagna di phishing che prende di mira gli utenti di Signal in Germania e nel resto d’Europa. L’attacco si concentra su profili specifici, tra…
 Innovazione
InnovazioneL’evoluzione dell’Intelligenza Artificiale ha superato una nuova, inquietante frontiera. Se fino a ieri parlavamo di algoritmi confinati dietro uno schermo, oggi ci troviamo di fronte al concetto di “Meatspace Layer”: un’infrastruttura dove le macchine non…
 Cybercrime
CybercrimeNegli ultimi anni, la sicurezza delle reti ha affrontato minacce sempre più sofisticate, capaci di aggirare le difese tradizionali e di penetrare negli strati più profondi delle infrastrutture. Un’analisi recente ha portato alla luce uno…
 Vulnerabilità
VulnerabilitàNegli ultimi tempi, la piattaforma di automazione n8n sta affrontando una serie crescente di bug di sicurezza. n8n è una piattaforma di automazione che trasforma task complessi in operazioni semplici e veloci. Con pochi click…
 Innovazione
InnovazioneArticolo scritto con la collaborazione di Giovanni Pollola. Per anni, “IA a bordo dei satelliti” serviva soprattutto a “ripulire” i dati: meno rumore nelle immagini e nei dati acquisiti attraverso i vari payload multisensoriali, meno…