
A new and formidable enemy has emerged in the cyber threat landscape: Kimwolf, a fearsome DDoS botnet, is having a devastating impact on devices worldwide. The consequences of this threat can be extremely serious, and its reach is constantly growing.
To understand the true extent of this problem, it’s essential to consider that Kimwolf is a network of malware-infected devices that can be remotely controlled by attackers. Kimwolf’s primary goal is to conduct DDoS attacks, aimed at overloading and rendering systems or networks inaccessible.
According to the Chinese company QiAnXin , Kimwolf managed to compromise at least 1.8 million heterogeneous devices, including Android-based smart TVs, set-top boxes, and tablets. This number is truly impressive, and the variety of devices affected makes the situation even more worrying.
Ultimately, Kimwolf represents a problem that cannot be ignored: its ability to rapidly propagate across multiple devices and carry out DDoS attacks. Given the large number of devices already affected, Kimwolf represents a significant threat that requires attention and action.
Kimwolf is compiled using the Native Development Kit (NDK) and goes beyond conventional DDoS capabilities. In addition to launching large-scale denial-of-service attacks, it integrates proxy forwarding, reverse shell access, and file management capabilities. As a result, attackers can not only recruit devices as bots, but also leverage them for broader offensive operations.
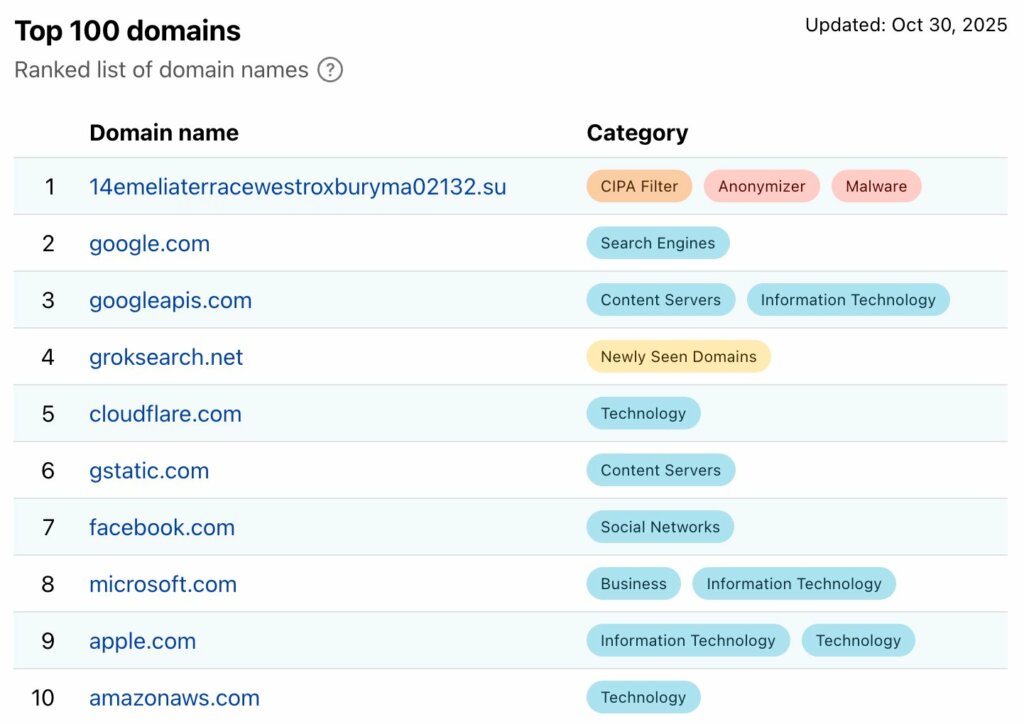
According to QiAnXin estimates, the botnet generated a total of 1.7 billion DDoS attacks between November 19 and 22, 2025. Due to the high volume of activity, its command-and-control domain, 14emeliaterracewestroxburyma02132[.]su, ranked at the top of Cloudflare’s DNS rankings .
The primary targets of this botnet are models such as TV BOX, SuperBOX, HiDPTAndroid, P200, X96Q, XBOX, SmartTB, MX10, and various others. Infections have been observed worldwide, with particularly high concentrations in Brazil, India, the United States, Argentina, South Africa, and the Philippines. QiAnXin has not yet determined how the initial malware was distributed to these devices.
Notably, Kimwolf’s command and control domains were successfully taken down at least three times in December by unidentified individuals, likely rival actors or independent security researchers. This disruption forced the botnet’s operators to change strategy and adopt the Ethereum Name Service (ENS) to harden their infrastructure against further takedowns.
The Kimwolf botnet is also linked to the infamous AISURU botnet. Investigators have discovered that attackers reused AISURU code during its early development stages, before creating Kimwolf as a more evasive successor. QiAnXin suspects that some DDoS campaigns previously attributed to AISURU may have involved Kimwolf, or even been primarily orchestrated by it.
Android smart TV and set-top box users are advised to check whether their devices are still using the default passwords and, if so, change them immediately . If any unusual behavior is detected, a full device reset may be necessary.
Firmware or system updates should be applied promptly as soon as they are available. However, many of these devices receive little or no update support after release, making long-term fixes difficult even when vulnerabilities are identified.
Follow us on Google News to receive daily updates on cybersecurity. Contact us if you would like to report news, insights or content for publication.
