
Check Point Research recently discovered a sophisticated phishing campaign orchestrated by KONNI , a threat group linked to North Korea . Historically focused on diplomatic targets in South Korea, the malicious actor has now expanded its reach to the APAC region, targeting Japan, Australia, and India.
The peculiarity of this offensive lies in its target: no longer just officials, but teams of engineers and software developers with access to blockchain infrastructure and crypto resources.
The attack is notable for its use of extremely carefully crafted technical decoys, which mimic legitimate project documents complete with architectures, timelines, and budgets.
The primary objective seems clear: to infiltrate development environments to steal API credentials, digital wallet keys, and crypto assets. This evolution suggests a shift toward purely financial objectives, exploiting the complexity of decentralized systems to maximize illicit profits.
The most surprising element of the analysis is the discovery of a PowerShell backdoor that shows unmistakable signs of AI assistance . The code doesn’t appear to be a typical script written by a human operator under pressure, but follows an exceedingly clean and commented modular structure.
The presence of placeholders with explicit instructions suggests that the KONNI group is using language patterns to accelerate the creation of increasingly complex malicious tools.
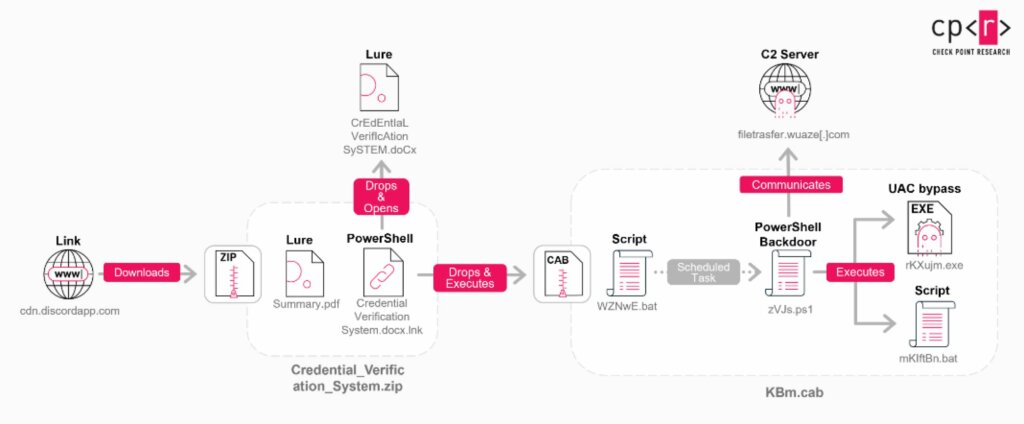
The attack chain, researchers report, begins with a link hosted on Discord that downloads a ZIP archive containing a decoy file and a malicious Windows shortcut.
Once activated, the system runs a series of anti-analysis checks to detect the presence of sandboxes or monitoring tools like Wireshark. To ensure persistence, the malware creates a scheduled task that mimics a OneDrive update process, running every hour to maintain control.
The backdoor is designed to adapt to the privileges of the affected user. If rights are limited, it attempts to bypass Windows UAC to gain administrative privileges and disable security notifications. In advanced scenarios, attackers deploy SimpleHelp, a legitimate remote management tool, to maintain long-term interactive access.
This allows criminals to move laterally across the network, turning a single infection into a complete compromise of the development infrastructure.
Follow us on Google News to receive daily updates on cybersecurity. Contact us if you would like to report news, insights or content for publication.
