
Gli analisti di AquaSec hanno scoperto un nuovo malware per Linux. Il malware si chiama Koske e si ritiene sia stato sviluppato utilizzando l’intelligenza artificiale. Utilizza immagini JPEG di panda per iniettarsi direttamente nella memoria. I ricercatori descrivono Koske come una “minaccia Linux sofisticata” il cui comportamento adattivo suggerisce che il malware è sviluppato utilizzando modelli linguistici di grandi dimensioni (LLM) o framework di automazione.
L’obiettivo principale di Koske è implementare miner ottimizzati per CPU e GPU che utilizzino le risorse di elaborazione dell’host per estrarre varie criptovalute. Poiché durante lo studio del malware sono stati scoperti indirizzi IP e frasi serbi negli script, nonché la lingua slovacca nel repository GitHub in cui si trovavano i miner, gli esperti non sono stati in grado di stabilire un’attribuzione esatta.
Gli aggressori ottengono l’accesso iniziale sfruttando configurazioni errate di JupyterLab che consentono l’esecuzione di comandi. Quindi, caricano due immagini panda in formato .JPEG sul sistema della vittima, che vengono archiviate su servizi legittimi come OVH Images, FreeImage e PostImage. Queste immagini contengono il payload dannoso.
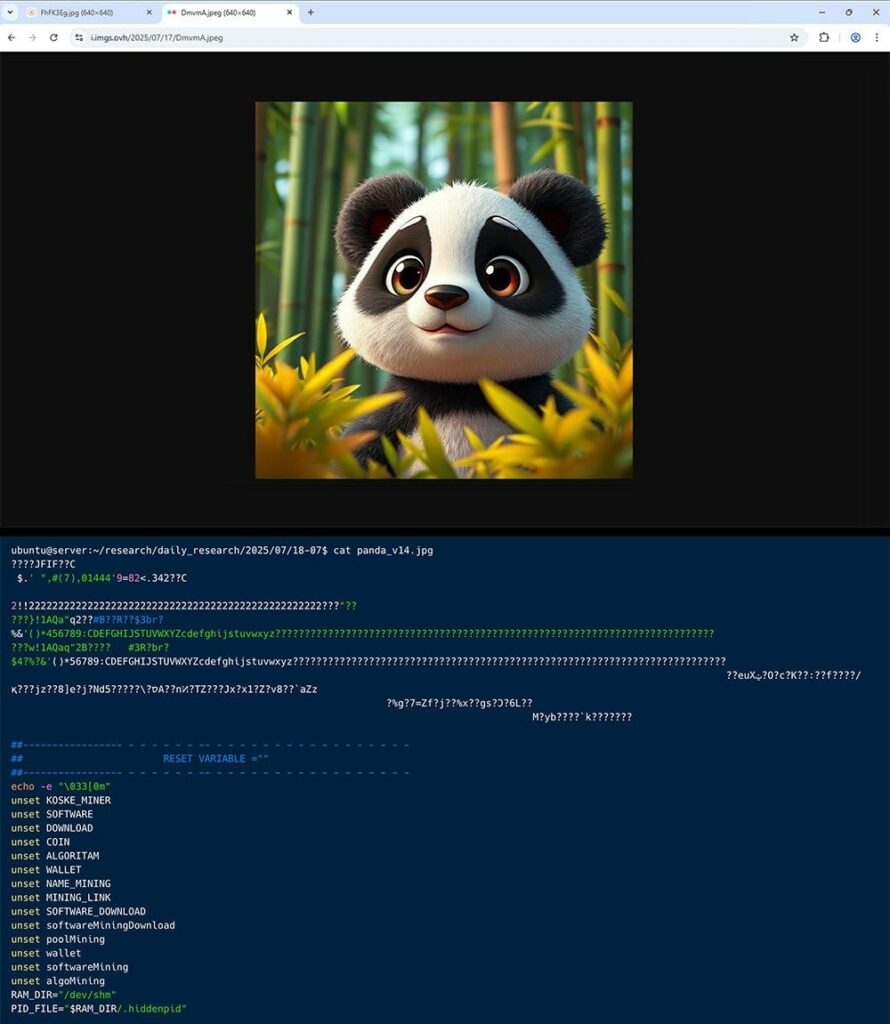
È importante sottolineare che gli hacker non utilizzano la steganografia per nascondere malware all’interno delle immagini. Si affidano invece a file poliglotti, che possono essere letti e interpretati in diversi formati. Negli attacchi Koske, lo stesso file può essere interpretato come un’immagine o uno script, a seconda dell’applicazione che lo apre o lo elabora.
Le immagini del panda contengono non solo l’immagine stessa, con le intestazioni corrette per il formato JPEG, ma anche script shell dannosi e codice scritto in C, che consentono di interpretare separatamente entrambi i formati. In altre parole, aprendo un file di questo tipo, l’utente vedrà solo un simpatico panda, ma l’interprete dello script eseguirà il codice aggiunto alla fine del file.
I ricercatori scrivono che ogni immagine contiene un carico utile ed entrambi vengono lanciati in parallelo. “Un payload è codice C che viene scritto direttamente in memoria, compilato ed eseguito come oggetto condiviso (file .so) e funziona come un rootkit”, spiegano gli esperti. “Il secondo payload è uno script shell che viene eseguito anch’esso dalla memoria. Utilizza le utilità di sistema standard di Linux per rimanere invisibile e persistente, lasciando una traccia minima.”
Lo script garantisce anche la stabilità della connessione e aggira le restrizioni di rete: riscrive /etc/resolv.conf per utilizzare i DNS di Cloudflare e Google, e protegge questo file con chattr +i. Il malware reimposta anche le regole di iptables, cancella le variabili di sistema relative al proxy ed esegue un modulo personalizzato per forzare l’avvio dei proxy funzionanti tramite curl, wget e richieste TCP dirette.
È proprio per questa adattabilità e questo comportamento che i ricercatori suggeriscono che il malware potrebbe essere stato sviluppato utilizzando LLM o piattaforme di automazione. Prima di distribuirsi al computer della vittima, il malware valuta le capacità dell’host (CPU e GPU) per selezionare il miner più adatto: Koske supporta il mining di 18 diverse criptovalute, tra cui Monero, Ravencoin, Zano, Nexa e Tari.
Se una valuta o un pool non è disponibile, il malware passa automaticamente a un’opzione di backup dal suo elenco interno, il che indica anche un elevato grado di automazione e flessibilità.
Ti è piaciuto questo articolo? Ne stiamo discutendo nella nostra Community su LinkedIn, Facebook e Instagram. Seguici anche su Google News, per ricevere aggiornamenti quotidiani sulla sicurezza informatica o Scrivici se desideri segnalarci notizie, approfondimenti o contributi da pubblicare.
