
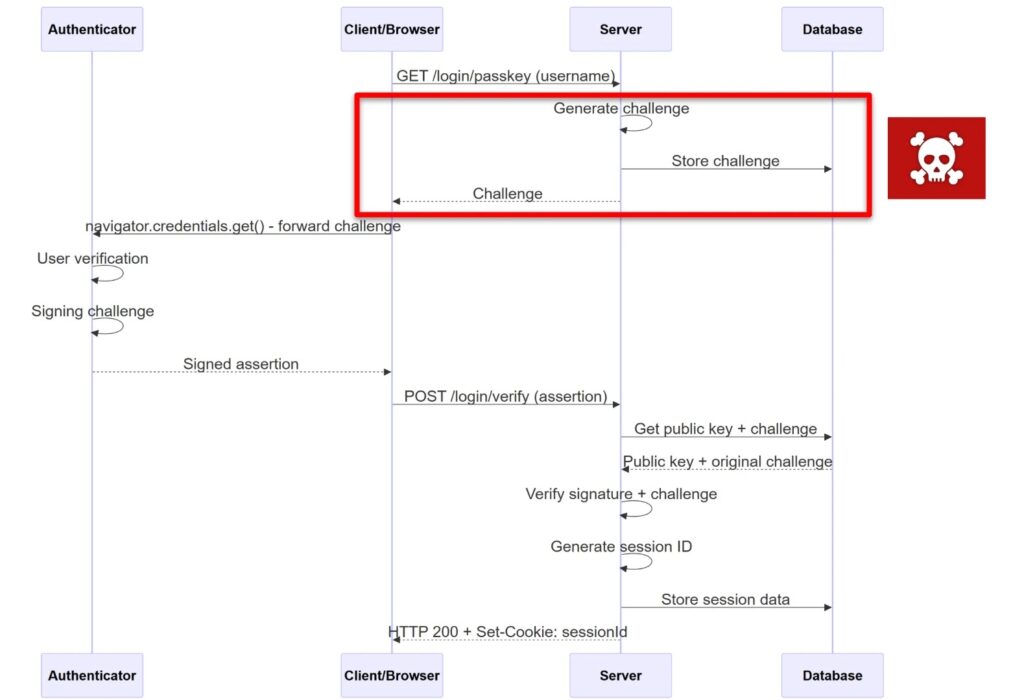
Un esperto di sicurezza informatica ha individuato falle zero-day che coinvolgono undici noti gestori di password, mettendo a rischio potenzialmente decine di milioni di utenti per il furto di credenziali con un semplice clic malevolo.
Un’innovativa strategia di attacco, conosciuta come \”DOM-based Extension Clickjacking\”, segna un avanzamento sostanziale rispetto ai metodi tradizionali di clickjacking online.
La ricerca, condotta dall’esperto di sicurezza Marek Tóth, rivela che gli aggressori possono sfruttare queste vulnerabilità per rubare dati di carte di credito, informazioni personali, credenziali di accesso e persino codici di autenticazione a due fattori da utenti ignari.
Catena di attacco di estensione basata su DOM
Diversamente dagli approcci tradizionali, che colpiscono le applicazioni web attraverso iframe non visibili, questa strategia altera gli elementi dell’interfaccia utente inseriti dalle estensioni del gestore di password nelle strutture DOM delle pagine web, facendoli diventare non visibili ma ancora cliccabili.
Quando gli utenti incontrano elementi apparentemente legittimi, come banner di consenso ai cookie o domande CAPTCHA su siti web compromessi, un singolo clic può attivare la compilazione automatica di moduli nascosti con i dati sensibili memorizzati.
L’attacco funziona creando script dannosi che nascondono gli elementi dell’interfaccia utente dell’estensione tramite manipolazione. JavaScript , in particolare tramite regolazioni dell’opacità e tecniche di sovrapposizione DOM. La ricerca approfondita di Tóth ha testato undici noti gestori di password, tra cui leader del settore come 1Password, Bitwarden, LastPass, Dashlane, Keeper e altri.
I risultati sono stati allarmanti: tutti i gestori di password testati erano inizialmente vulnerabili ad almeno una variante della tecnica Extension Clickjacking basata su DOM. Le vulnerabilità interessano circa 40 milioni di installazioni attive sulle piattaforme Chrome Web Store, Firefox Add-ons ed Edge Add-ons.
Sei gestori di password su nove testati erano vulnerabili all’estrazione dei dati delle carte di credito, mentre otto su dieci potevano essere sfruttati per esfiltrare informazioni personali memorizzate.
Forse la cosa più preoccupante è che dieci gestori di password su undici erano soggetti a furto di credenziali, compresi i codici TOTP (Time-based One-Time Password) utilizzati per l’autenticazione a due fattori.
Ti è piaciuto questo articolo? Ne stiamo discutendo nella nostra Community su LinkedIn, Facebook e Instagram. Seguici anche su Google News, per ricevere aggiornamenti quotidiani sulla sicurezza informatica o Scrivici se desideri segnalarci notizie, approfondimenti o contributi da pubblicare.

 Cybercrime
CybercrimeLe autorità tedesche hanno recentemente lanciato un avviso riguardante una sofisticata campagna di phishing che prende di mira gli utenti di Signal in Germania e nel resto d’Europa. L’attacco si concentra su profili specifici, tra…
 Innovazione
InnovazioneL’evoluzione dell’Intelligenza Artificiale ha superato una nuova, inquietante frontiera. Se fino a ieri parlavamo di algoritmi confinati dietro uno schermo, oggi ci troviamo di fronte al concetto di “Meatspace Layer”: un’infrastruttura dove le macchine non…
 Cybercrime
CybercrimeNegli ultimi anni, la sicurezza delle reti ha affrontato minacce sempre più sofisticate, capaci di aggirare le difese tradizionali e di penetrare negli strati più profondi delle infrastrutture. Un’analisi recente ha portato alla luce uno…
 Vulnerabilità
VulnerabilitàNegli ultimi tempi, la piattaforma di automazione n8n sta affrontando una serie crescente di bug di sicurezza. n8n è una piattaforma di automazione che trasforma task complessi in operazioni semplici e veloci. Con pochi click…
 Innovazione
InnovazioneArticolo scritto con la collaborazione di Giovanni Pollola. Per anni, “IA a bordo dei satelliti” serviva soprattutto a “ripulire” i dati: meno rumore nelle immagini e nei dati acquisiti attraverso i vari payload multisensoriali, meno…