
Di recente, un sottogruppo avanzato legato al noto autore della minaccia Lazarus è stato individuato, mentre distribuiva tre diversi trojan di accesso remoto (RAT) all’interno di organizzazioni operanti nel settore finanziario e delle criptovalute che erano state compromesse. L’accesso iniziale è stato realizzato prevalentemente attraverso campagne di ingegneria sociale condotte su Telegram, dove gli attaccanti fingevano di essere dipendenti legittimi di importanti società commerciali.
Siti web di incontri contraffatti, tra cui falsi portali come Calendly e Picktime, attirano le vittime, che vengono raggiunte tramite un exploit zero-day di Chrome che consente l’esecuzione silenziosa di codice sul loro computer. Gli aggressori, una volta dentro la rete, impiegano PondRAT come prima fase, mentre in seguito utilizzano ThemeForestRAT, più difficile da rilevare, che viene eseguito solo in memoria.
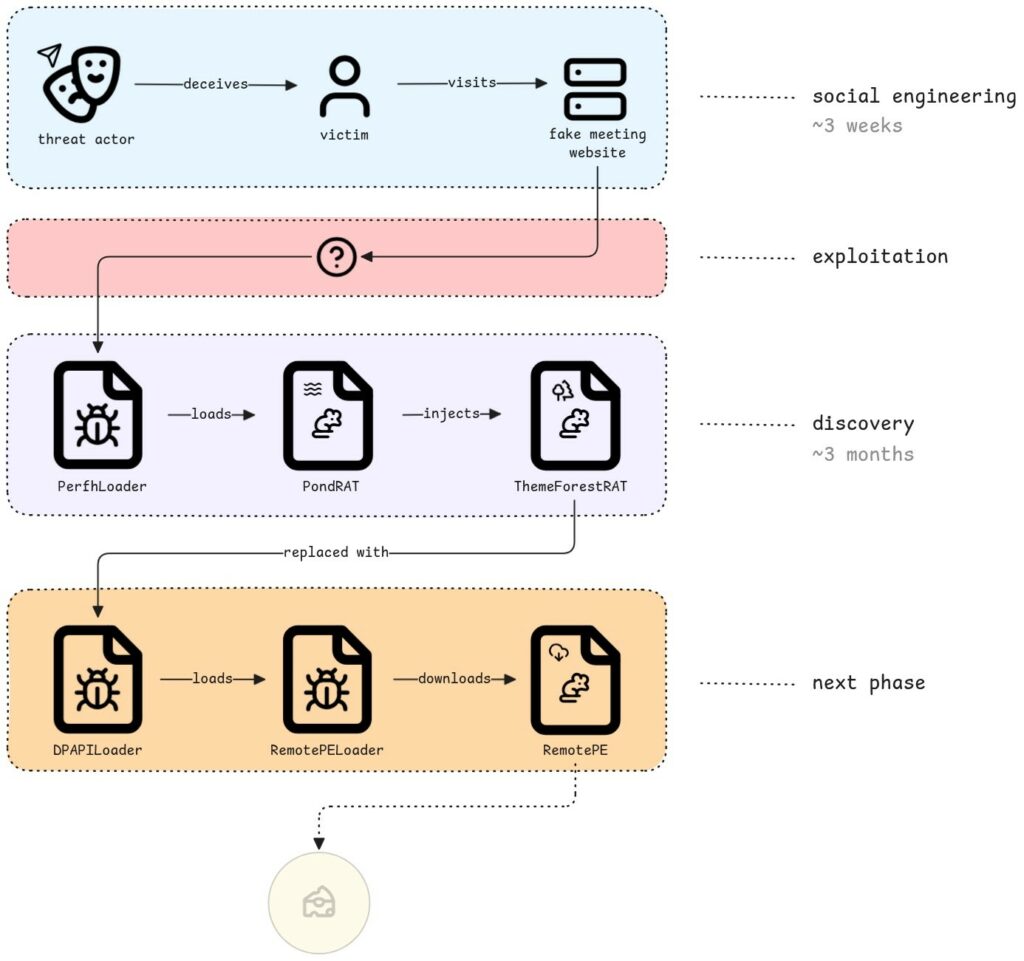
L’uso di nuove famiglie di malware e di sospetti exploit zero-day ha colto di sorpresa molti difensori. A rendere il tutto ancora più urgente, la raffinata sicurezza operativa del gruppo che dimostra la capacità di combinare loader personalizzati con il dirottamento di DLL di Windows e la crittografia DPAPI.
A seguito di mesi di esplorazione e movimenti strategici, Lazarus ottimizza l’accesso precedente eliminando gli artefatti superflui, e procede con l’installazione di un avanzato RemotePE RAT al fine di assicurare un controllo prolungato.
Di seguito i 3 RAT (Remote Access Trojan) utilizzati nella campagna:
Gli analisti di Fox-IT e NCC Group hanno osservato che la velocità e la precisione di questa catena di infezioni evidenziano le capacità avanzate dell’autore e la sua profonda familiarità con gli strumenti personalizzati e disponibili al pubblico.
E’ stato notato dagli analisti che il servizio SessionEnv viene sfruttato da PerfhLoader attraverso il caricamento di DLL fasulle al fine di eseguire in modo continuativo PondRAT oppure il suo predecessore POOLRAT. Un file di payload non trasparente (come ad esempio perfh011.dat) viene decodificato dal loader utilizzando un algoritmo di cifratura XOR prima di essere eseguito nella memoria.
Dopo la decrittazione, PerfhLoader sfrutta un caricatore DLL manuale open source per iniettare PondRAT nella memoria senza scrivere file eseguibili sul disco, consentendo operazioni di ricognizione furtiva e di esfiltrazione dei dati..
Ti è piaciuto questo articolo? Ne stiamo discutendo nella nostra Community su LinkedIn, Facebook e Instagram. Seguici anche su Google News, per ricevere aggiornamenti quotidiani sulla sicurezza informatica o Scrivici se desideri segnalarci notizie, approfondimenti o contributi da pubblicare.

 Vulnerabilità
VulnerabilitàVenerdì sera l’exchange di criptovalute sudcoreano Bithumb è stato teatro di un incidente operativo che ha rapidamente scosso il mercato locale di Bitcoin, dimostrando quanto anche un singolo errore umano possa avere effetti immediati e…
 Cybercrime
CybercrimeLe autorità tedesche hanno recentemente lanciato un avviso riguardante una sofisticata campagna di phishing che prende di mira gli utenti di Signal in Germania e nel resto d’Europa. L’attacco si concentra su profili specifici, tra…
 Innovazione
InnovazioneL’evoluzione dell’Intelligenza Artificiale ha superato una nuova, inquietante frontiera. Se fino a ieri parlavamo di algoritmi confinati dietro uno schermo, oggi ci troviamo di fronte al concetto di “Meatspace Layer”: un’infrastruttura dove le macchine non…
 Cybercrime
CybercrimeNegli ultimi anni, la sicurezza delle reti ha affrontato minacce sempre più sofisticate, capaci di aggirare le difese tradizionali e di penetrare negli strati più profondi delle infrastrutture. Un’analisi recente ha portato alla luce uno…
 Vulnerabilità
VulnerabilitàNegli ultimi tempi, la piattaforma di automazione n8n sta affrontando una serie crescente di bug di sicurezza. n8n è una piattaforma di automazione che trasforma task complessi in operazioni semplici e veloci. Con pochi click…