
An in-depth security analysis of Livewire , an essential framework for developing dynamic interfaces in Laravel, has revealed a significant vulnerability.
Synacktiv security experts have identified a critical flaw and design error that, if exploited, could allow attackers to execute arbitrary code on servers hosting more than 130,000 applications globally.
Livewire is widely used, appearing in approximately a third of newly developed Laravel projects, to generate interactive frontends with minimal JavaScript code. It works by “dehydrating” a component’s state, transforming it into a serialized format and sending it to the client, which is then “rehydrated” upon its return.
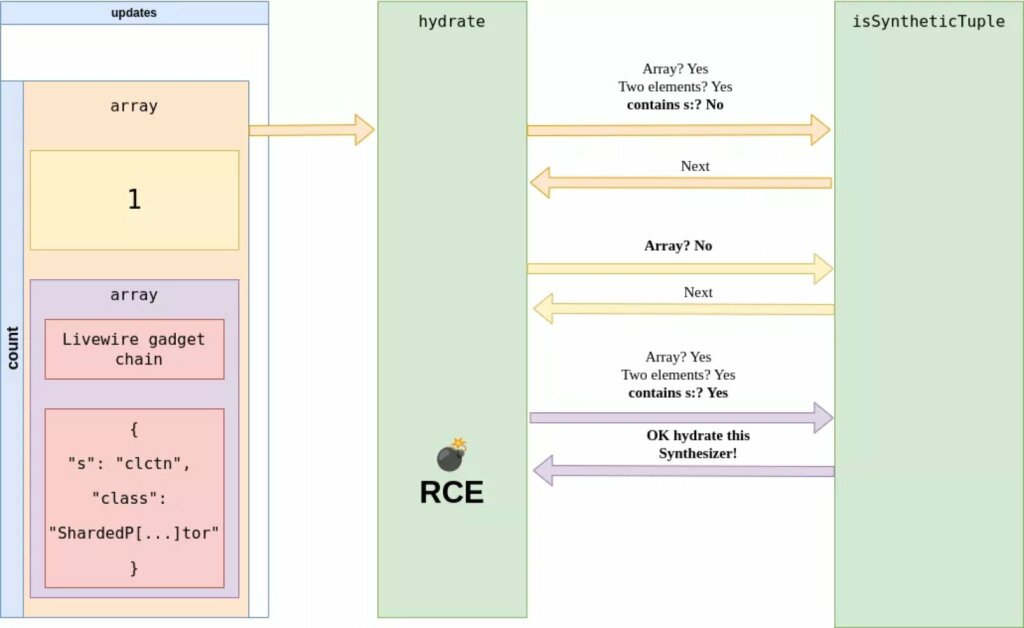
The bug, tracked as CVE-2025-54068, exploits Livewire’s internal “hydration” mechanism, the process used to synchronize state between the server and the browser. Although a patch has been released, researchers warn that a key design feature remains a ticking time bomb for applications with leaked credentials.
The main problem lay in the way Livewire handled updates. “By default, if developers don’t enforce strong typing on their component parameters, they will be vulnerable to type juggling,” the report explains.
Attackers could send a specially crafted request that converts a simple integer counter into a malicious array, tricking the server into executing code.
Synacktiv researchers discovered they could manipulate this process. By identifying a chain of gadgets involving PHP’s unserialize() behavior, they found a way to achieve “stealthy remote command execution.”
To demonstrate the severity of these flaws, Synacktiv has released a proof-of-concept tool called Livepyre . The tool automates the exploit process, verifying the vulnerability and delivering the payload.
“The discovery of CVE-2025-54068 further highlighted a critical flaw: the ability to break the update mechanism, completely bypassing the need for APP_KEY,” the researchers said.
Livewire typically protects its state with a checksum signed by the application’s APP_KEY. However, the CVE-2025-54068 vulnerability allowed attackers to completely bypass this requirement.
This means that even without the secret key, an attacker could inject malicious objects, particularly using a technique involving GuzzleHttpPsr7FnStream and destruct magic methods, to trigger remote code execution (RCE).
Although CVE-2025-54068 has been fixed in versions 3.6.4 and later, a more serious risk remains. Research shows that if an attacker manages to obtain the APP_KEY (a common occurrence due to leaks or default values), the application is essentially defenseless against RCE.
“The version of the exploit that requires APP_KEY has not been patched because it exploits the way Livewire is designed… The Livewire team has not considered this to be a security issue.”
Synacktiv argues that this position understates the risk, noting that “having the APP_KEY to a Livewire-based application later than version 3 means you can completely compromise it.”
Follow us on Google News to receive daily updates on cybersecurity. Contact us if you would like to report news, insights or content for publication.
