
A settembre 2025 è emersa una nuova incarnazione del noto ransomware LockBit, denominata LockBit 5.0. Non è solo un “aggiornamento”: è un adattamento operativo pensato per essere rapido, meno rumoroso e più impattante sulle infrastrutture virtualizzate. La caratteristica che va sottolineata fin da subito è che la 5.0 è cross-platform: sono stati identificati campioni per Windows, Linux e VMware ESXi — il che amplia la superficie d’attacco e richiede coordinamento tra team diversi (endpoint, server, virtualizzazione).
La catena d’attacco resta la stessa, ma LockBit 5.0 la porta avanti più velocemente e con accorgimenti pensati per ridurre al minimo le tracce:
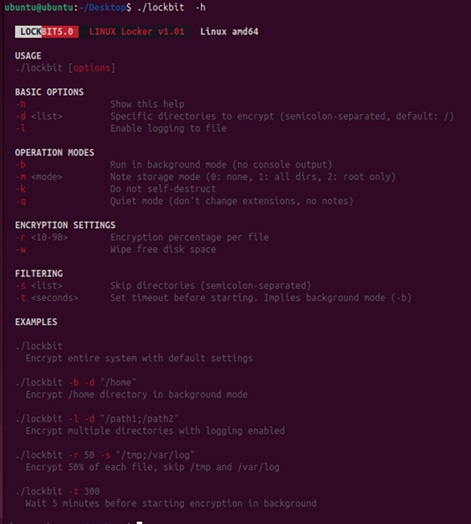
L’immagine mostra i parametri, e come utilizzarli. per lanciare la cifratura
LockBit 5.0 sposta il gioco sulla memoria e allarga il perimetro: non basta più l’endpoint, vanno protetti anche gli ambienti che lo orchestrano. La risposta efficace combina patching costante, hardening degli host ESXi, monitoraggio proattivo dei log e protezione endpoint e di rete”. Backup isolate, meglio se immutabili, e testati restano essenziali per il recovery. In parallelo, è necessario ridurre la superficie d’attacco (funzionalità non essenziali off), applicare least privilege e sorvegliare le anomalie di rete. Investire in MDR e threat hunting proattivo è cruciale per individuare attività stealth prima che diventino crittografia massiva
Ti è piaciuto questo articolo? Ne stiamo discutendo nella nostra Community su LinkedIn, Facebook e Instagram. Seguici anche su Google News, per ricevere aggiornamenti quotidiani sulla sicurezza informatica o Scrivici se desideri segnalarci notizie, approfondimenti o contributi da pubblicare.

 Cybercrime
CybercrimeLe autorità tedesche hanno recentemente lanciato un avviso riguardante una sofisticata campagna di phishing che prende di mira gli utenti di Signal in Germania e nel resto d’Europa. L’attacco si concentra su profili specifici, tra…
 Innovazione
InnovazioneL’evoluzione dell’Intelligenza Artificiale ha superato una nuova, inquietante frontiera. Se fino a ieri parlavamo di algoritmi confinati dietro uno schermo, oggi ci troviamo di fronte al concetto di “Meatspace Layer”: un’infrastruttura dove le macchine non…
 Cybercrime
CybercrimeNegli ultimi anni, la sicurezza delle reti ha affrontato minacce sempre più sofisticate, capaci di aggirare le difese tradizionali e di penetrare negli strati più profondi delle infrastrutture. Un’analisi recente ha portato alla luce uno…
 Vulnerabilità
VulnerabilitàNegli ultimi tempi, la piattaforma di automazione n8n sta affrontando una serie crescente di bug di sicurezza. n8n è una piattaforma di automazione che trasforma task complessi in operazioni semplici e veloci. Con pochi click…
 Innovazione
InnovazioneArticolo scritto con la collaborazione di Giovanni Pollola. Per anni, “IA a bordo dei satelliti” serviva soprattutto a “ripulire” i dati: meno rumore nelle immagini e nei dati acquisiti attraverso i vari payload multisensoriali, meno…