Gli specialisti del Genians Security Center hanno scoperto una versione migliorata del malware RoKRAT, associato al gruppo nordcoreano APT37. La nuova versione si distingue per un insolito modo di nascondere il codice dannoso: nel corpo delle normali immagini JPEG. Questo approccio consente di bypassare i sistemi antivirus tradizionali, poiché la funzionalità dannosa non viene scritta direttamente sul disco, ma viene estratta nella RAM.
L’infezione iniziale inizia con l’avvio di un collegamento .LNK dannoso contenuto in un archivio ZIP. Un esempio è un archivio chiamato “National Intelligence and Counterintelligence Manuscript.zip”. La sua struttura include un file .LNK di grandi dimensioni (oltre 50 MB) che contiene documenti esca e componenti codificati: shellcode (ttf01.dat), script PowerShell (ttf02.dat) e file batch (ttf03.bat).
Quando il file viene eseguito, PowerShell viene attivato, utilizzando un XOR a un byte con la chiave 0x33, decrittografando lo shellcode a 32 bit. Il passaggio successivo prevede l’iniezione di un secondo livello di codice crittografato, che viene decrittografato all’offset 0x590 utilizzando la chiave 0xAE. Questo crea un file eseguibile contenente riferimenti a informazioni di debug, come il percorso “D:WorkUtilInjectShellcodeReleaseInjectShellcode.pdb”.
Il frammento decrittografato viene quindi iniettato in processi Windows legittimi come “mspaint.exe” o “notepad.exe” situati nella directory SysWOW64. Questa procedura crea una memoria virtuale in cui vengono scritti blocchi di dati di circa 892.928 byte. Questi vengono nuovamente decrittografati utilizzando XOR, questa volta con la chiave 0xD6. A questo punto, la parte principale di RoKRAT viene attivata.
Il file non viene salvato su disco, rendendo molto più difficile l’analisi post-infezione. I segnali di affiliazione ad APT37 includono timestamp del file, come 21 aprile 2025 alle 00:39:59 UTC, e costrutti univoci come “-wwjaughalvncjwiajs-“.
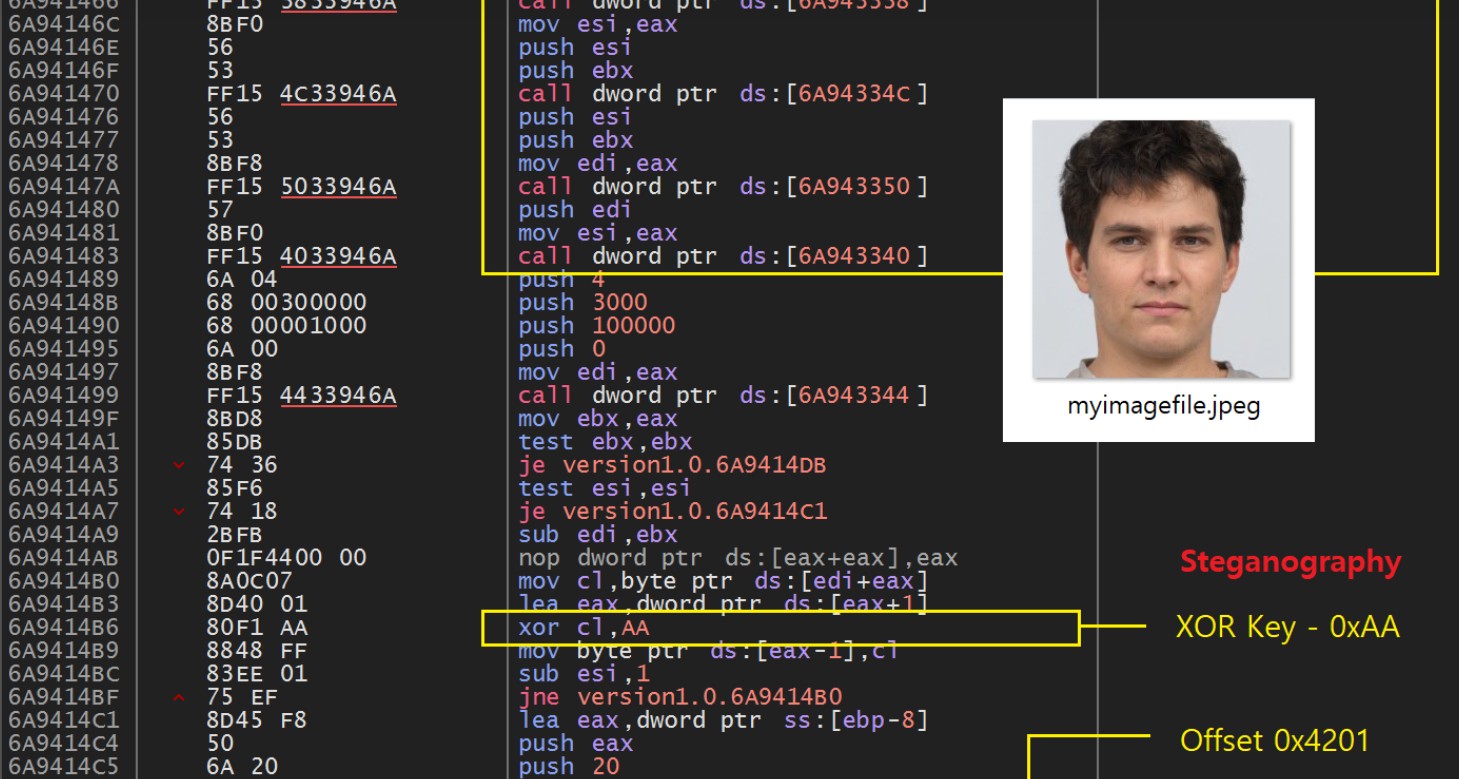
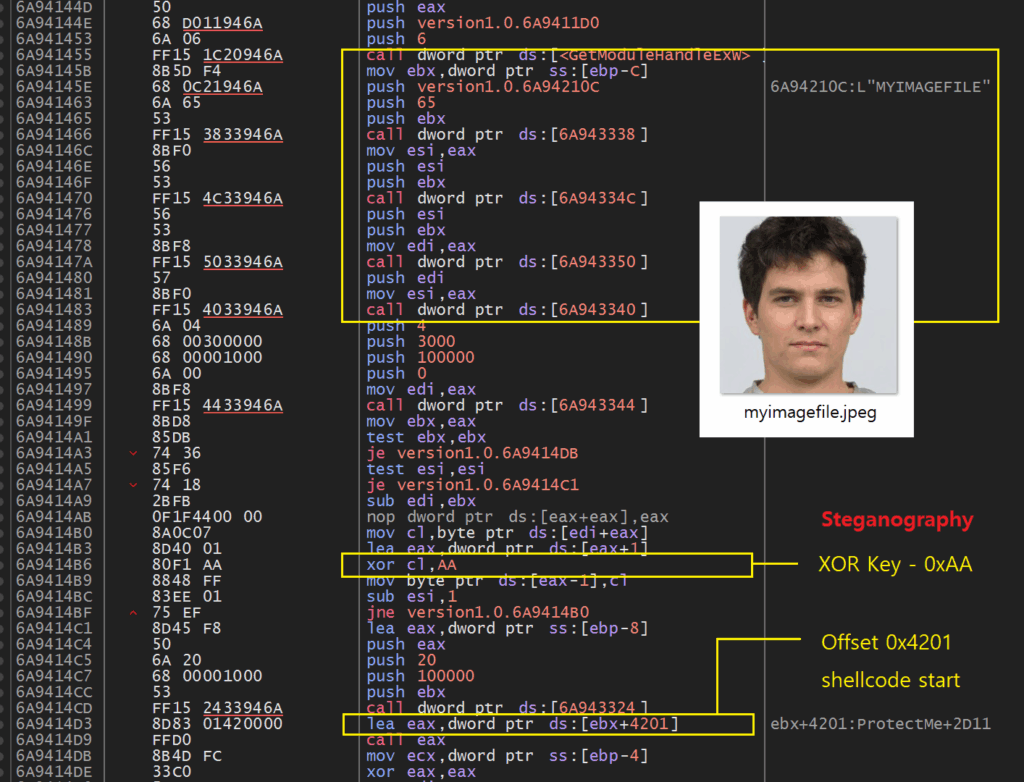
L’innovazione significativa è l’uso della steganografia. Il loader dannoso RoKRAT è incorporato in un’immagine JPEG, come “Father.jpg”, ospitata su Dropbox. Questo file conserva un’intestazione Exif valida, ma a partire dall’offset 0x4201 contiene uno shellcode codificato. Per estrarlo, viene utilizzata una doppia trasformazione XOR: prima con la chiave 0xAA, poi con 0x29. RoKRAT viene quindi caricato direttamente in memoria ed eseguito senza lasciare traccia sul file system.

Per avviare il file DLL dannoso, vengono utilizzate tecniche di sideload tramite utility legittime, come ShellRunas.exe o AccessEnum.exe, incorporate nei documenti HWP. I download vengono effettuati da piattaforme cloud, tra cui Dropbox, pCloud e Yandex.Disk, utilizzando API e token di accesso scaduti, come ad esempio: “hFkFeKn8jJIAAAAAAAAAAZr14zutJmQzoOx-g5k9SV9vy7phb9QiNCIEO7SAp1Ch”.
Oltre a raccogliere informazioni e documenti di sistema, RoKRAT acquisisce screenshot e li invia a server esterni. Gli ultimi campioni, datati luglio 2025, sono distribuiti tramite scorciatoie come “Academy Operation for Successful Resettlement of North Korean Defectors in South Korea.lnk”. Queste versioni utilizzano già “notepad.exe” come processo di destinazione per l’iniezione e nuovi percorsi come “D:WorkWeapon” sono specificati all’interno del codice, a indicare il continuo perfezionamento del toolkit.
I sistemi di rilevamento e risposta agli endpoint (EDR) svolgono un ruolo importante nella protezione da tali attacchi. Queste soluzioni monitorano le attività insolite, tra cui iniezioni di codice e connessioni di rete alle API cloud. La visualizzazione tramite EDR consente di ricostruire l’intera catena di attacco, dall’avvio di LNK alla trasmissione dei dati al server di comando, nonché di isolare rapidamente la minaccia utilizzando la metodologia MITRE ATT&CK.
Con i metodi sempre più sofisticati dei gruppi APT basati sul diniego di accesso ai file e sul trasferimento occulto di dati, è chiaro che le tradizionali difese basate sulle firme non sono più sufficienti. Soprattutto quando vengono presi di mira i sistemi Windows in Corea del Sud e in altri paesi della regione.
Ti è piaciuto questo articolo? Ne stiamo discutendo nella nostra Community su LinkedIn, Facebook e Instagram. Seguici anche su Google News, per ricevere aggiornamenti quotidiani sulla sicurezza informatica o Scrivici se desideri segnalarci notizie, approfondimenti o contributi da pubblicare.

 Vulnerabilità
VulnerabilitàVenerdì sera l’exchange di criptovalute sudcoreano Bithumb è stato teatro di un incidente operativo che ha rapidamente scosso il mercato locale di Bitcoin, dimostrando quanto anche un singolo errore umano possa avere effetti immediati e…
 Cybercrime
CybercrimeLe autorità tedesche hanno recentemente lanciato un avviso riguardante una sofisticata campagna di phishing che prende di mira gli utenti di Signal in Germania e nel resto d’Europa. L’attacco si concentra su profili specifici, tra…
 Innovazione
InnovazioneL’evoluzione dell’Intelligenza Artificiale ha superato una nuova, inquietante frontiera. Se fino a ieri parlavamo di algoritmi confinati dietro uno schermo, oggi ci troviamo di fronte al concetto di “Meatspace Layer”: un’infrastruttura dove le macchine non…
 Cybercrime
CybercrimeNegli ultimi anni, la sicurezza delle reti ha affrontato minacce sempre più sofisticate, capaci di aggirare le difese tradizionali e di penetrare negli strati più profondi delle infrastrutture. Un’analisi recente ha portato alla luce uno…
 Vulnerabilità
VulnerabilitàNegli ultimi tempi, la piattaforma di automazione n8n sta affrontando una serie crescente di bug di sicurezza. n8n è una piattaforma di automazione che trasforma task complessi in operazioni semplici e veloci. Con pochi click…