
A cancellation message from Booking.com with a high penalty seems like a typical business practice for hotels and apartments. But it’s precisely this type of email that triggered a new malware campaign, tracked by Securonix specialists under the name PHALT#BLYX. It clearly demonstrates how modern attacks are increasingly based not on vulnerabilities, but on user psychology and trust in built-in Windows tools.
The attack targets the hotel industry and was actively used during the peak holiday season. Victims receive phishing emails supposedly requesting the cancellation of a reservation, with payment details in euros. This creates a sense of urgency and encourages the recipient to click on the link as quickly as possible. Instead of the genuine Booking.com website, the user is redirected to a high-quality fake , almost indistinguishable from the original. The logos, fonts, and colors appear convincing and therefore do not arouse suspicion.
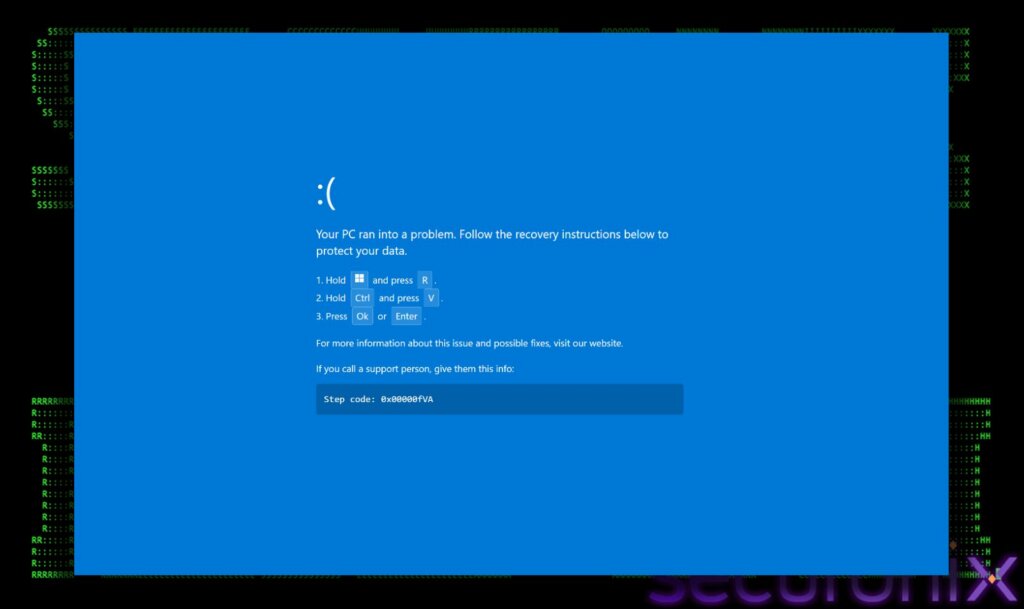
The fake page displays a message about a supposed download error and prompts the victim to refresh the page. After clicking, the browser expands to full screen and simulates the Windows blue screen of death. The user is offered a simple solution: open the Run window, paste the copied command, and press Enter. In reality, a malicious PowerShell script has been placed in the clipboard. This allows the victim to initiate the infection, bypassing many automatic protection mechanisms.
The attack then proceeds in several stages. The PowerShell script downloads a special MSBuild project file and runs it using Microsoft’s native build tool. This is a key step in the entire chain. Using a trusted system binary allows the attack to appear legitimate and often bypass antivirus software and application control policies. As a diversion, the legitimate Booking.com administration site opens in the browser to evade detection.
The downloaded MSBuild project contains embedded code that initially weakens system security. Specifically, it adds exclusions to Windows Defender for important directories and file types and, if administrator privileges are present, completely disables real-time protection. This opens the way for the main malicious component to be downloaded. If administrator privileges are not present, the malware constantly displays User Account Control (UAC) prompts, hoping the user will agree to these pop-ups.
The final payload is a modified DCRat , a well-known remote control tool closely associated with Russian-speaking cybercriminals. It establishes persistent access to the system, infiltrates legitimate Windows processes, intercepts keystrokes, collects system data, and can download additional modules, including miners and other malware. To establish persistence, it uses an unusual technique involving .url links in the startup folder, which point to a local executable file.
Researchers also detected traces of Russian in service strings and debug messages within the malicious code. The wording appears natural and grammatically correct, indicating that the malware was developed by native speakers or used a pre-made toolkit found on Russian-language underground forums. This aligns perfectly with DCRat’s choice, which has long been popular in this segment.
The PHALT#BLYX campaign demonstrates how dangerous a combination of social engineering and so-called “living off the land” (LotL) techniques, which use standard operating system tools for attacks, can be. In such scenarios, traditional signature-based protection often proves insufficient, and user behavior becomes the key factor. Experts recommend paying particular attention to employee training, being wary of urgent financial emails, and carefully monitoring for unusual activity in system utilities like MSBuild. It is precisely in these details that the first signs of a serious incident increasingly lie hidden.
Follow us on Google News to receive daily updates on cybersecurity. Contact us if you would like to report news, insights or content for publication.
