
È stato scoperto un nuovo toolkit di phishing, MatrixPDF, che consente agli aggressori di trasformare normali file PDF in esche interattive che aggirano la sicurezza della posta elettronica e reindirizzano le vittime a siti Web che rubano credenziali o scaricano malware.
I ricercatori di Varonis, che hanno scoperto lo strumento, sottolineano che MatrixPDF viene pubblicizzato come un simulatore di phishing e una soluzione per specialisti di red team. Tuttavia, sottolineano che è stato individuato per la prima volta su forum di hacker.
“MatrixPDF: è uno strumento avanzato per la creazione di PDF di phishing realistici, progettato per i team di red team e per la formazione sulla sicurezza informatica”, si legge nell’annuncio. “Con l’importazione di PDF tramite trascinamento della selezione, l’anteprima in tempo reale e le sovrapposizioni personalizzabili, MatrixPDF consente di creare scenari di phishing di livello professionale. Funzionalità di sicurezza integrate come la sfocatura dei contenuti, i reindirizzamenti sicuri, la crittografia dei metadati e il bypass di Gmail garantiscono affidabilità e distribuzione in ambienti di test.”
Il toolkit è disponibile con diversi piani tariffari, che vanno da $ 400 al mese a $ 1.500 all’anno.
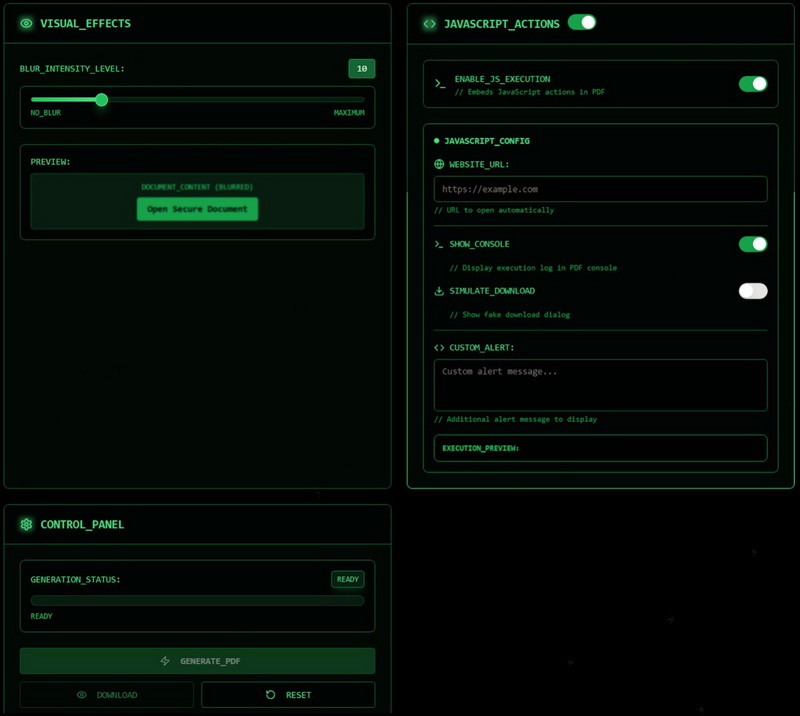
I ricercatori spiegano che il builder MatrixPDF consente agli aggressori di caricare un file PDF legittimo e poi di aggiungervi funzionalità dannose, come l’offuscamento del contenuto, falsi prompt “Documento protetto” e sovrapposizioni cliccabili che puntano a un URL esterno con il payload.
Inoltre, MatrixPDF consente azioni JavaScript, che vengono attivate quando un utente apre un documento o clicca su un pulsante. In questo caso, il codice JavaScript tenta di aprire un sito web o di eseguire altre azioni dannose.
La funzione di sfocatura crea file PDF il cui contenuto appare protetto, sfocato e contiene un pulsante “Apri documento protetto“. Cliccando su questo pulsante si apre un sito web che può essere utilizzato per rubare credenziali o distribuire malware.
Un test condotto da specialisti ha dimostrato che i PDF dannosi creati utilizzando MatrixPDF possono essere inviati a una casella di posta Gmail e che l’email riesce a bypassare i filtri anti-phishing. Questo perché questi file non contengono file binari dannosi, ma solo link esterni.
Un altro test condotto dai ricercatori dimostra come la semplice apertura di un PDF dannoso provochi l’apertura di un sito web esterno. Questa funzionalità è più limitata, poiché i moderni visualizzatori di PDF avvisano l’utente che il file sta tentando di connettersi a un sito remoto.
Gli esperti di Varonis ci ricordano che i file PDF restano uno strumento popolare per gli attacchi di phishing perché sono ampiamente distribuiti e le piattaforme di posta elettronica possono visualizzarli senza preavviso.
Ti è piaciuto questo articolo? Ne stiamo discutendo nella nostra Community su LinkedIn, Facebook e Instagram. Seguici anche su Google News, per ricevere aggiornamenti quotidiani sulla sicurezza informatica o Scrivici se desideri segnalarci notizie, approfondimenti o contributi da pubblicare.

 Cybercrime
CybercrimeLe autorità tedesche hanno recentemente lanciato un avviso riguardante una sofisticata campagna di phishing che prende di mira gli utenti di Signal in Germania e nel resto d’Europa. L’attacco si concentra su profili specifici, tra…
 Innovazione
InnovazioneL’evoluzione dell’Intelligenza Artificiale ha superato una nuova, inquietante frontiera. Se fino a ieri parlavamo di algoritmi confinati dietro uno schermo, oggi ci troviamo di fronte al concetto di “Meatspace Layer”: un’infrastruttura dove le macchine non…
 Cybercrime
CybercrimeNegli ultimi anni, la sicurezza delle reti ha affrontato minacce sempre più sofisticate, capaci di aggirare le difese tradizionali e di penetrare negli strati più profondi delle infrastrutture. Un’analisi recente ha portato alla luce uno…
 Vulnerabilità
VulnerabilitàNegli ultimi tempi, la piattaforma di automazione n8n sta affrontando una serie crescente di bug di sicurezza. n8n è una piattaforma di automazione che trasforma task complessi in operazioni semplici e veloci. Con pochi click…
 Innovazione
InnovazioneArticolo scritto con la collaborazione di Giovanni Pollola. Per anni, “IA a bordo dei satelliti” serviva soprattutto a “ripulire” i dati: meno rumore nelle immagini e nei dati acquisiti attraverso i vari payload multisensoriali, meno…