
Il ricercatore BobDaHacker ha scoperto che la convalida dei punti premio dell’App di McDonalds veniva gestita solo lato client, consentendo agli utenti di richiedere articoli gratuiti come i nuggets anche senza punti sufficienti. BobDaHacker ha segnalato il problema ma un ingegnere informatico lo ha liquidarlo come “troppo impegnativo”, sebbene il bug sia stato corretto giorni dopo, probabilmente dopo che l’ingegnere stesso lo aveva esaminato.
Successivamente il ricercatore ha analizzato a fondo i sistemi di McDonald’s e ha scoperto vulnerabilità nel Design Hub, una piattaforma utilizzata per le risorse del brand da team in 120 paesi. Questa piattaforma si basava su una password lato client per la protezione.
Dopo aver segnalato il problema, l’azienda ha intrapreso una revisione di tre mesi per implementare accessi corretti per dipendenti e partner. Tuttavia, rimaneva un difetto significativo: semplicemente sostituendo “login” con “register” nell’URL, era possibile accedere a un endpoint aperto.
L’API forniva inoltre indicazioni agli utenti su eventuali campi mancanti, rendendo la creazione di un account incredibilmente semplice. Ancora più preoccupante era il fatto che le password venivano inviate via email in chiaro, una pratica estremamente rischiosa nel 2025.

Test successivi hanno confermato che l’endpoint era ancora accessibile, consentendo l’accesso non autorizzato a materiali riservati destinati esclusivamente all’uso interno, ha affermato BobDaHacker .
I file JavaScript nel Design Hub hanno rivelato ulteriori dettagli: le chiavi API e i segreti di Magicbell esposti consentivano di elencare gli utenti e inviare notifiche di phishing tramite l’infrastruttura di McDonald’s. Questi sono stati ruotati dopo la segnalazione. Anche gli indici di ricerca di Algolia erano elencabili, esponendo dati personali come nomi, indirizzi email e richieste di accesso.
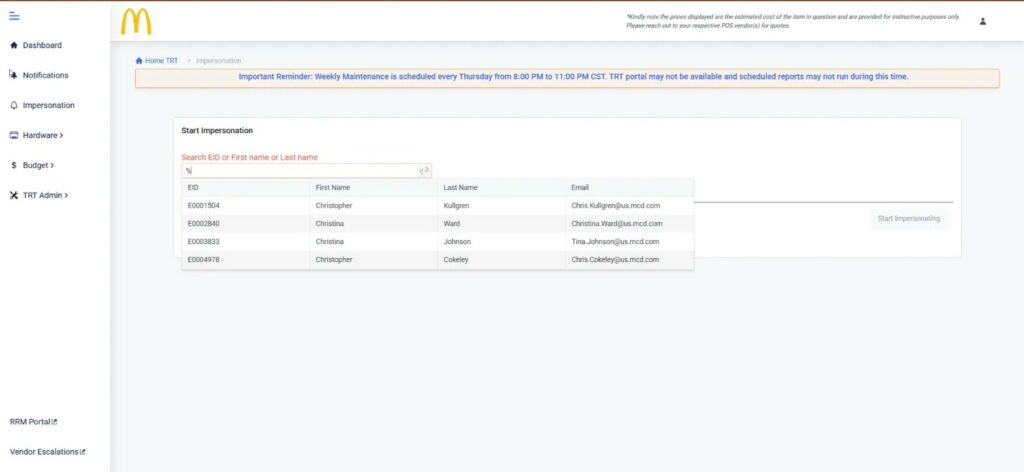
Anche i portali dei dipendenti si sono dimostrati altrettanto vulnerabili. Gli account base dei membri del team di McDonalds potevano accedere a TRT, uno strumento aziendale, per cercare i dati globali dei dipendenti, comprese le email dei dirigenti, e persino utilizzare una funzione di “impersonificazione”.
Il panel Global Restaurant Standards (GRS) non disponeva di autenticazione per le funzioni di amministrazione, consentendo a chiunque di iniettare HTML tramite API. Per dimostrarlo, il ricercatore ha modificato brevemente la homepage in “Sei stato Shreked” prima di ripristinarla.
Ulteriori problemi includevano un accesso non configurato correttamente, l’esposizione di documenti interni al personale di basso livello e exploit nell’app sperimentale per ristoranti di CosMc, come l’utilizzo illimitato di coupon e l’iniezione arbitraria di dati sugli ordini.
Ricordiamo che il mese scorso una grave vulnerabilità di sicurezza nel sistema di assunzione basato sull’intelligenza artificiale di McDonald’s ha esposto i dati personali di 64 milioni di candidati tramite una debole sicurezza basata sulla password “123456”.
Ti è piaciuto questo articolo? Ne stiamo discutendo nella nostra Community su LinkedIn, Facebook e Instagram. Seguici anche su Google News, per ricevere aggiornamenti quotidiani sulla sicurezza informatica o Scrivici se desideri segnalarci notizie, approfondimenti o contributi da pubblicare.

 Cybercrime
CybercrimeLe autorità tedesche hanno recentemente lanciato un avviso riguardante una sofisticata campagna di phishing che prende di mira gli utenti di Signal in Germania e nel resto d’Europa. L’attacco si concentra su profili specifici, tra…
 Innovazione
InnovazioneL’evoluzione dell’Intelligenza Artificiale ha superato una nuova, inquietante frontiera. Se fino a ieri parlavamo di algoritmi confinati dietro uno schermo, oggi ci troviamo di fronte al concetto di “Meatspace Layer”: un’infrastruttura dove le macchine non…
 Cybercrime
CybercrimeNegli ultimi anni, la sicurezza delle reti ha affrontato minacce sempre più sofisticate, capaci di aggirare le difese tradizionali e di penetrare negli strati più profondi delle infrastrutture. Un’analisi recente ha portato alla luce uno…
 Vulnerabilità
VulnerabilitàNegli ultimi tempi, la piattaforma di automazione n8n sta affrontando una serie crescente di bug di sicurezza. n8n è una piattaforma di automazione che trasforma task complessi in operazioni semplici e veloci. Con pochi click…
 Innovazione
InnovazioneArticolo scritto con la collaborazione di Giovanni Pollola. Per anni, “IA a bordo dei satelliti” serviva soprattutto a “ripulire” i dati: meno rumore nelle immagini e nei dati acquisiti attraverso i vari payload multisensoriali, meno…