
A new scheme called ” ConsentFix ” expands the capabilities of the already known ClickFix social media attack and allows Microsoft accounts to be hijacked without a password or multi-factor authentication. To do this, attackers leverage a legitimate Azure CLI application and OAuth authentication capabilities, turning the standard sign-in process into a hijacking tool.
ClickFix relies on displaying pseudo-system instructions to the user, asking them to execute commands or perform various steps, supposedly to fix an error or prove their identity.
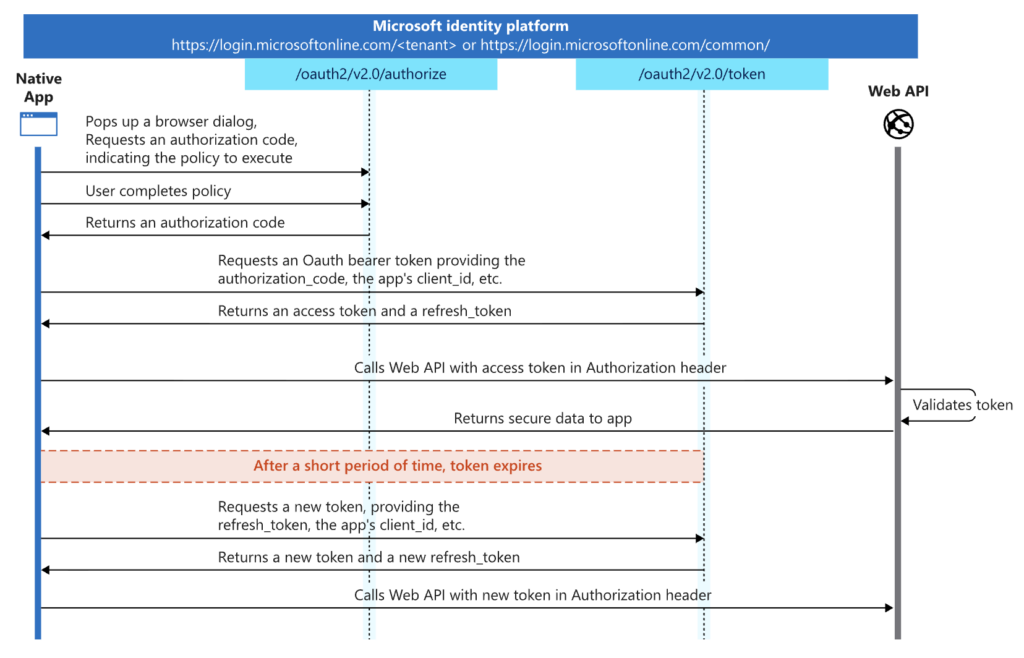
The “ConsentFix” variant, described by the Push Security team, maintains the general deception scenario, but instead of installing malware, it aims to steal an OAuth 2.0 authorization code, which is then used to obtain an access token for the Azure CLI.
The attack begins with a visit to a compromised legitimate website, well-indexed on Google for relevant queries. A fake Cloudflare Turnstile widget appears on the page, requesting a valid email address. The attackers’ script compares the entered address against a predefined list of targets and excludes bots, analysts, and random visitors. Only selected victims are presented with the next step, structured like a typical ClickFix script with seemingly innocuous verification steps.
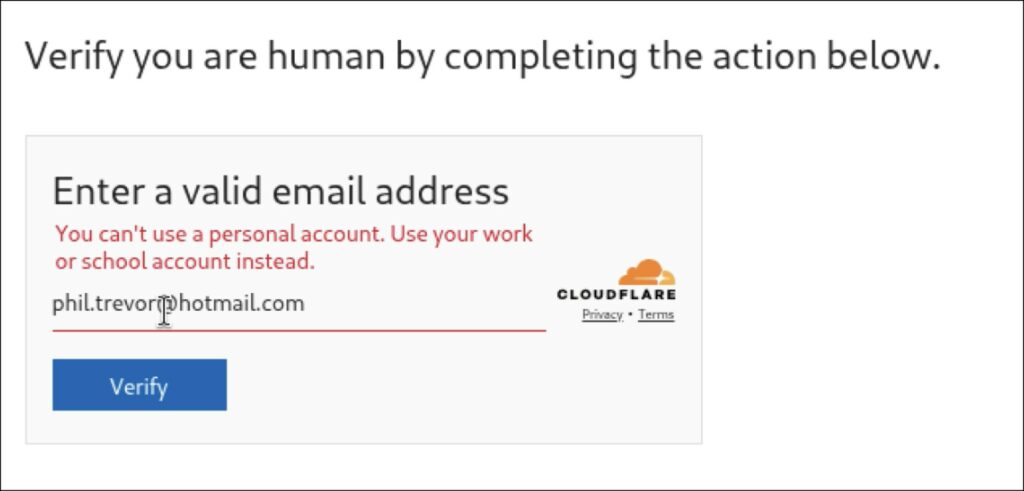
The victim is prompted to click the sign-in button, after which the real Microsoft domain opens in a separate tab. However, instead of the usual sign-in form, it uses an Azure authorization page that generates a specific OAuth code for the Azure CLI. If the user is signed in with a Microsoft account, they simply select it; otherwise, they log in normally using the authentic form.
After authorization, the browser is redirected to localhost, and a URL with the Azure CLI authorization code associated with the account appears in the address bar . The final step in the deception is to paste this address back into the malicious page, as shown. The attacker can then exchange the code for an access token and manage the account via the Azure CLI without knowing the password or completing multi-factor authentication . During an active session, no login is actually required. To reduce the risk of disclosure, the script is executed only once from each IP address.
Push Security experts recommend that security teams monitor the Azure CLI for unusual activity , including logins from unusual IP addresses, and monitor the use of legacy Graph permissions, which this scheme relies on to evade standard detection tools.
Follow us on Google News to receive daily updates on cybersecurity. Contact us if you would like to report news, insights or content for publication.
