
Microsoft has quietly patched a long-standing Windows vulnerability that has been exploited in real-world attacks for several years. The update was released on November’s Patch Tuesday, despite the company having previously been slow to address the issue. This information was revealed by 0patch , which indicated that the flaw had been actively exploited by various groups since 2017.
The issue, designated CVE-2025-9491, affects Windows’ handling of LNK shortcuts. A user interface error caused part of the command embedded in the shortcut to remain hidden when viewing its properties. This allowed malicious code to run as a harmless file . Experts observed that the shortcuts were designed to deceive users by using invisible characters and masquerading as documents.
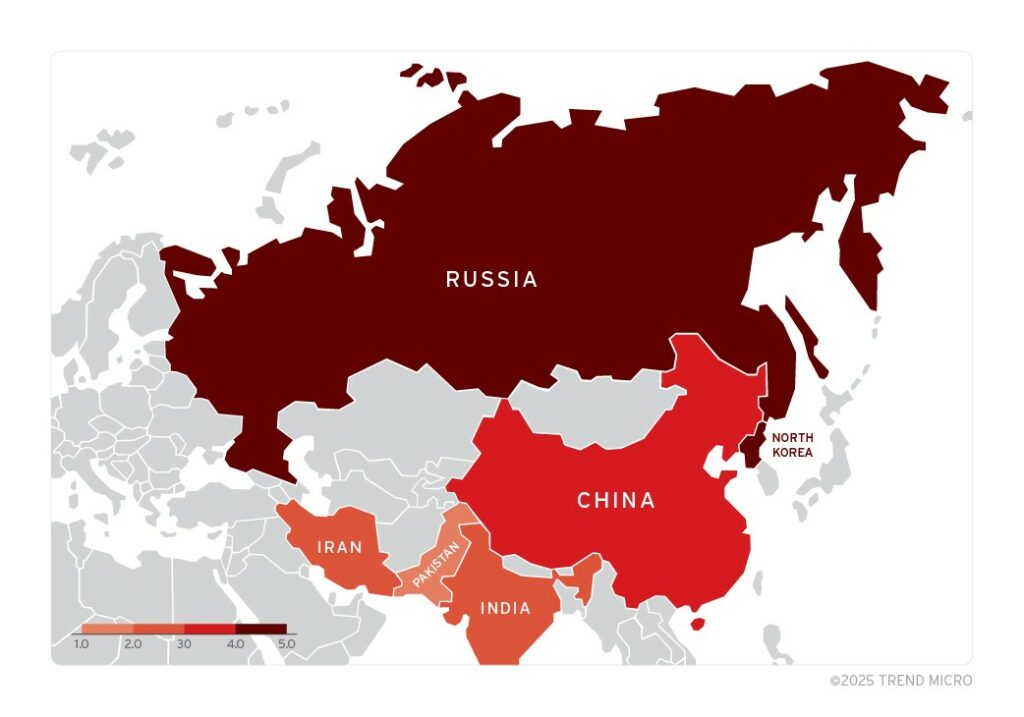
The first details emerged in the spring of 2025, when researchers reported that this mechanism was being used by eleven state-sponsored groups from China, Iran, and North Korea for espionage, data theft, and financial attacks .
At the time, the flaw was also known as ZDI-CAN-25373 . Microsoft stated at the time that the issue did not require immediate attention, citing the blocking of the LNK format in many Office applications and warnings when attempting to open such files.
HarfangLab later reported that the vulnerability had been exploited by the XDSpy group to distribute the XDigo malware in attacks on Eastern European governments. In the fall of 2025, Arctic Wolf detected another wave of abuse, this time targeting Chinese online groups targeting European diplomatic and government institutions and using the PlugX malware. Microsoft later issued a clarification, reiterating that it did not consider the issue critical due to the requirement for user intervention and the presence of system warnings.
According to 0patch, the problem went beyond simply hiding the command tail. The link format allows strings up to tens of thousands of characters long, but the properties window only displayed the first 260 characters, truncating the rest without warning. This allowed a significant portion of the executed command to be hidden. A third-party fix for 0patch addressed the issue differently : it added a warning when attempting to open a link with arguments longer than 260 characters.
A Microsoft update fixed the issue by expanding the Target field so that the entire command is displayed, even if it exceeds the previous length limit.
A company representative, when contacted, did not directly confirm the release of the update, but referred to general security recommendations and assured that the company continues to improve the interface and security mechanisms.
Follow us on Google News to receive daily updates on cybersecurity. Contact us if you would like to report news, insights or content for publication.
