
Negli ultimi anni Microsoft Teams è diventato uno degli strumenti di collaborazione più diffusi all’interno delle aziende, trasformandosi in un canale strategico non solo per la comunicazione, ma anche per la gestione di documenti, meeting e processi operativi.
Questa crescente centralità, tuttavia, non è passata inosservata ai criminali informatici, che stanno sviluppando tecniche sempre più sofisticate di attacco e ingegneria sociale proprio su questa piattaforma, con l’obiettivo di infiltrarsi nelle reti aziendali e sottrarre informazioni sensibili. La combinazione tra fiducia implicita nello strumento e l’elevato volume di comunicazioni quotidiane crea infatti un terreno fertile per campagne mirate di compromissione.
Un esempio emblematico è l’operazione di ingegneria sociale d’avanguardia orchestrata dal gruppo malintenzionato EncryptHub, che ha messo in campo una strategia perversa capace di fondere tecniche di spoofing con exploit tecnici mirati. Come anticipato nell’analisi di ieri, si tratta di una campagna avanzata che sfrutta congiuntamente tattiche di impersonificazione e vettori di attacco informatici, riuscendo così a compromettere in maniera significativa la sicurezza delle infrastrutture aziendali.
Questo nuovo approccio, impersonando gli addetti IT, dimostra come i confini tra ingegneria sociale e attacchi tecnici si stiano assottigliando, aprendo scenari sempre più complessi per la difesa cyber.
L’attacco inizia con gli autori della minaccia che affermano di appartenere a reparti IT interni e inviano richieste di connessione a Microsoft Teams ai dipendenti presi di mira.
Una volta che le vittime accettano la richiesta e stabiliscono una sessione remota, gli aggressori le guidano nell’esecuzione di comandi PowerShell che sembrano legittimi ma in realtà scaricano ed eseguono script dannosi.
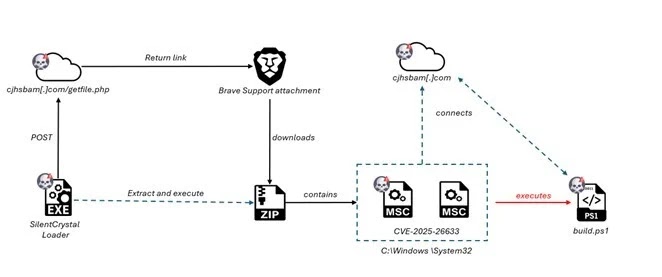
Il comando iniziale eseguito ignora i criteri di sicurezza di Windows e scarica uno script di PowerShell denominato “runner.ps1” dai domini controllati dagli aggressori, come cjhsbam[.]com.
Questo script è progettato per sfruttare il CVE-2025-26633 una vulnerabilità nel framework Management Console di Microsoft denominata “MSC EvilTwin”.
La vulnerabilità CVE-2025-26633 è stata ufficialmente rivelata come vulnerabilità zero-day a marzo 2025, sebbene esempi di attacchi correlati siano stati osservati in circolazione già nel febbraio 2025. Da allora Microsoft ha rilasciato patch di sicurezza, ma la vulnerabilità continua a essere sfruttata attivamente contro sistemi privi di patch.
La vulnerabilità ha un punteggio CVSS di 7,0, che indica un’elevata gravità, ed è stata aggiunta al catalogo delle vulnerabilità note sfruttate del CISA, sottolineandone la natura critica per le agenzie federali e gli ambienti aziendali.
La campagna evidenzia la persistente efficacia degli attacchi di ingegneria sociale combinati con lo sfruttamento tecnico. “L’ingegneria sociale rimane uno degli strumenti più efficaci nell’arsenale di un criminale informatico e il gruppo emergente EncryptHub si è subito unito a questa tendenza“, hanno osservato i ricercatori di Trustwave.
Gli esperti di sicurezza informatica raccomandano di implementare strategie di difesa multilivello, tra cui l’immediata correzione di CVE-2025-26633, un monitoraggio avanzato delle attività di Microsoft Management Console e una formazione completa sulla consapevolezza degli utenti incentrata sulle tattiche di ingegneria sociale.
Le organizzazioni dovrebbero inoltre limitare le capacità di accesso remoto e implementare rigide procedure di verifica per le interazioni con il supporto IT.
Ti è piaciuto questo articolo? Ne stiamo discutendo nella nostra Community su LinkedIn, Facebook e Instagram. Seguici anche su Google News, per ricevere aggiornamenti quotidiani sulla sicurezza informatica o Scrivici se desideri segnalarci notizie, approfondimenti o contributi da pubblicare.

 Cybercrime
CybercrimeLe autorità tedesche hanno recentemente lanciato un avviso riguardante una sofisticata campagna di phishing che prende di mira gli utenti di Signal in Germania e nel resto d’Europa. L’attacco si concentra su profili specifici, tra…
 Innovazione
InnovazioneL’evoluzione dell’Intelligenza Artificiale ha superato una nuova, inquietante frontiera. Se fino a ieri parlavamo di algoritmi confinati dietro uno schermo, oggi ci troviamo di fronte al concetto di “Meatspace Layer”: un’infrastruttura dove le macchine non…
 Cybercrime
CybercrimeNegli ultimi anni, la sicurezza delle reti ha affrontato minacce sempre più sofisticate, capaci di aggirare le difese tradizionali e di penetrare negli strati più profondi delle infrastrutture. Un’analisi recente ha portato alla luce uno…
 Vulnerabilità
VulnerabilitàNegli ultimi tempi, la piattaforma di automazione n8n sta affrontando una serie crescente di bug di sicurezza. n8n è una piattaforma di automazione che trasforma task complessi in operazioni semplici e veloci. Con pochi click…
 Innovazione
InnovazioneArticolo scritto con la collaborazione di Giovanni Pollola. Per anni, “IA a bordo dei satelliti” serviva soprattutto a “ripulire” i dati: meno rumore nelle immagini e nei dati acquisiti attraverso i vari payload multisensoriali, meno…