
I ricercatori hanno individuato una vulnerabilità nel nuovo ransomware Midnight, basato sul vecchio codice sorgente di Babuk. Il malware viene commercializzato come una versione “avanzata” del malware, ma i tentativi di accelerare e potenziare il processo di crittografia si sono rivelati infruttuosi: i ricercatori Norton sono riusciti a creare un decryptor gratuito per i dati interessati.
Gli esperti affermano che Midnight si basa sul codice sorgente di Babuk, che è trapelato nel pubblico dominio nel 2021 e successivamente utilizzato come base per decine di progetti malware.
Midnight replica quasi interamente la struttura del suo predecessore, ma gli sviluppatori hanno deciso di modificarne lo schema di crittografia: il malware utilizza ChaCha20 per crittografare il contenuto dei file e RSA per crittografare la chiave ChaCha20.
Tuttavia, i ricercatori hanno scoperto un bug nell’utilizzo della chiave RSA, che ha permesso loro di recuperare parzialmente i dati e poi di creare un decryptor completo. Lo strumento è gratuito ed è già stato rilasciato pubblicamente.
Come Babuk, Midnight crittografa solo porzioni di file per agire più velocemente e paralizzare il sistema. La dimensione dei blocchi crittografati dipende dalle dimensioni del file: documenti o database di grandi dimensioni diventano illeggibili quasi istantaneamente. Nelle ultime build, il malware ha ampliato il suo elenco di obiettivi per coprire quasi tutti i formati di file, ad eccezione dei file eseguibili (.exe, .dll e .msi).
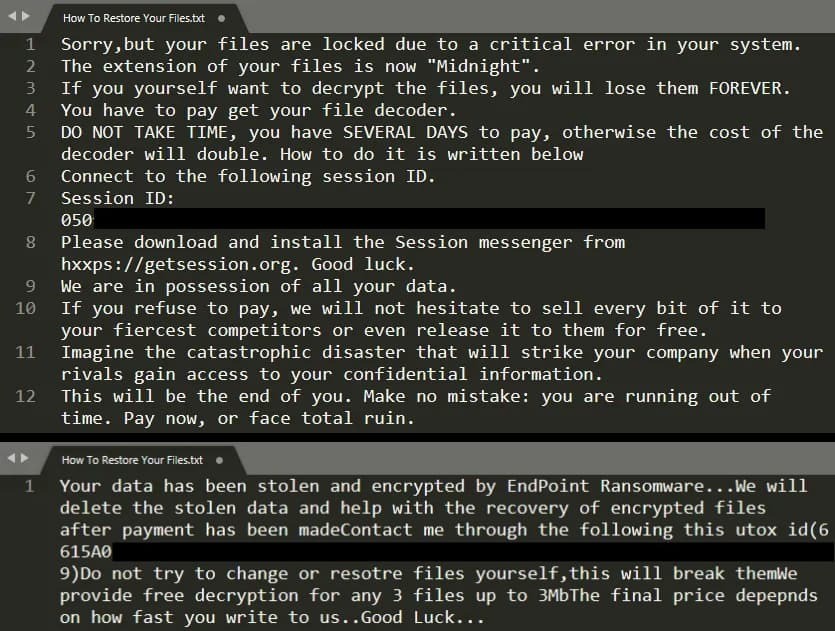
I dispositivi infetti finiscono per ricevere file con estensione .midnight o .endpoint, e a volte questo tag è incorporato direttamente nel contenuto del file. Alla vittima viene lasciata una richiesta di riscatto standard (How To Restore Your Files.txt) e talvolta persino un file di registro come report.midnight o debug.endpoint, che mostra il funzionamento dello script.
Ti è piaciuto questo articolo? Ne stiamo discutendo nella nostra Community su LinkedIn, Facebook e Instagram. Seguici anche su Google News, per ricevere aggiornamenti quotidiani sulla sicurezza informatica o Scrivici se desideri segnalarci notizie, approfondimenti o contributi da pubblicare.

 Cybercrime
CybercrimeLe autorità tedesche hanno recentemente lanciato un avviso riguardante una sofisticata campagna di phishing che prende di mira gli utenti di Signal in Germania e nel resto d’Europa. L’attacco si concentra su profili specifici, tra…
 Innovazione
InnovazioneL’evoluzione dell’Intelligenza Artificiale ha superato una nuova, inquietante frontiera. Se fino a ieri parlavamo di algoritmi confinati dietro uno schermo, oggi ci troviamo di fronte al concetto di “Meatspace Layer”: un’infrastruttura dove le macchine non…
 Cybercrime
CybercrimeNegli ultimi anni, la sicurezza delle reti ha affrontato minacce sempre più sofisticate, capaci di aggirare le difese tradizionali e di penetrare negli strati più profondi delle infrastrutture. Un’analisi recente ha portato alla luce uno…
 Vulnerabilità
VulnerabilitàNegli ultimi tempi, la piattaforma di automazione n8n sta affrontando una serie crescente di bug di sicurezza. n8n è una piattaforma di automazione che trasforma task complessi in operazioni semplici e veloci. Con pochi click…
 Innovazione
InnovazioneArticolo scritto con la collaborazione di Giovanni Pollola. Per anni, “IA a bordo dei satelliti” serviva soprattutto a “ripulire” i dati: meno rumore nelle immagini e nei dati acquisiti attraverso i vari payload multisensoriali, meno…