
Quattro vulnerabilità, denominate PerfektBlue, interessano lo stack Bluetooth BlueSDK di OpenSynergy. Le vulnerabilità consentono l’esecuzione remota di codice arbitrario e potrebbero contribuire all’accesso a componenti critici nei veicoli di produttori come Mercedes-Benz AG, Volkswagen e Škoda. OpenSynergy ha confermato i problemi a giugno 2024 e ha rilasciato le patch a settembre. Tuttavia, molte case automobilistiche non hanno ancora implementato gli aggiornamenti nel loro firmware.
Le vulnerabilità sono state scoperte dagli specialisti di PCA Cyber Security, un’azienda specializzata in sicurezza automobilistica. È importante sottolineare che l’azienda partecipa regolarmente alla competizione Pwn2Own Automotive e ha scoperto più di 50 bug in diversi sistemi automobilistici dall’anno scorso. Secondo i ricercatori, i problemi di PerfektBlue riguardano “milioni di dispositivi nel settore automobilistico e non solo”. Tuttavia, gli esperti hanno studiato il binario compilato di BlueSDK, poiché semplicemente non disponevano del codice sorgente.
Le vulnerabilità variano in gravità e possono consentire l’accesso ai componenti interni di diversi veicoli tramite il sistema di infotainment.
Sebbene i ricercatori non rendano noti tutti i dettagli tecnici, scrivono che un aggressore connesso a un dispositivo vulnerabile ha la capacità di manipolare il sistema, aumentare i privilegi e passare ad altri componenti. PerfektBlue è un attacco RCE a 1 clic, perché l’attaccante deve solo convincere l’utente ad accettare la richiesta di associazione con il proprio dispositivo. Alcune case automobilistiche configurano i loro sistemi in modo tale che l’associazione sia possibile anche senza conferma.
PCA Cyber Security ha dimostrato che PerfektBlue funziona con le unità principali di Volkswagen ID.4 (sistema ICSA3), Mercedes-Benz (NTG6) e Skoda Superb (MIB3).
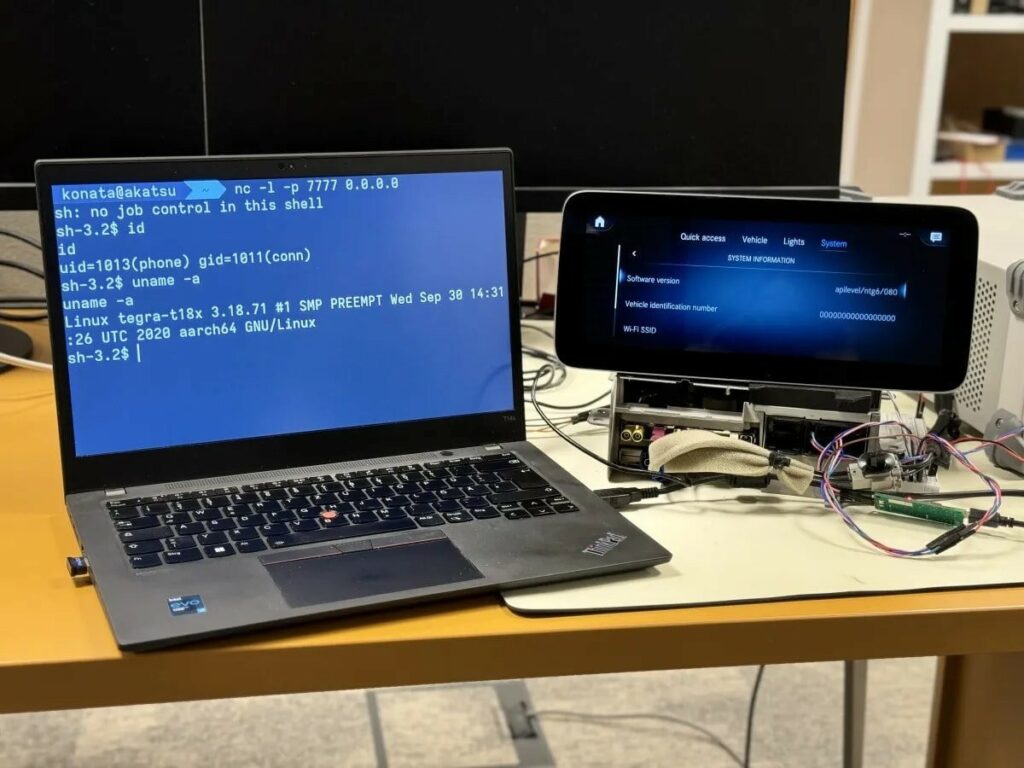
Guscio posteriore per Mercedes-Benz NTG6
Si sottolinea che dopo l’esecuzione di codice remoto nel contesto del sistema di infotainment dell’auto, un aggressore può tracciare le coordinate GPS, origliare le conversazioni in auto, accedere ai contatti telefonici del proprietario e anche eseguire movimenti laterali e raggiungere sottosistemi critici dell’auto. BlueSDK di OpenSynergy è ampiamente utilizzato al di fuori del settore automobilistico, ma è difficile individuare chi altro lo utilizzi nei propri prodotti (a causa della personalizzazione, del rebranding e della mancanza di trasparenza).
I ricercatori hanno informato Volkswagen, Mercedes-Benz e Škoda dei problemi riscontrati, concedendo loro tempo sufficiente per implementare le soluzioni. Tuttavia, gli esperti non hanno mai ricevuto risposta dalle case automobilistiche. I rappresentanti della Mercedes-Benz non hanno risposto alle richieste dei giornalisti e la Volkswagen ha affermato di aver avviato un’indagine subito dopo aver ricevuto informazioni sulle vulnerabilità. “L’indagine ha dimostrato che in determinate condizioni è possibile connettersi al sistema di infotainment del veicolo tramite Bluetooth senza autorizzazione”, ha affermato la Volkswagen.
Ma l’azienda ha sottolineato che l’exploit funzionerà solo se saranno soddisfatte alcune condizioni:
Anche se queste condizioni sono soddisfatte, durante l’attacco l’aggressore deve rimanere entro un raggio di 5-7 metri dall’auto per mantenere l’accesso. L’azienda ha fatto notare separatamente che, anche in caso di compromissione riuscita, un hacker non sarà in grado di compromettere le funzioni critiche dell’auto, tra cui lo sterzo, i sistemi di assistenza alla guida, il funzionamento del motore e l’impianto frenante (che sono controllati da un’unità separata con meccanismi di protezione propri).
Ti è piaciuto questo articolo? Ne stiamo discutendo nella nostra Community su LinkedIn, Facebook e Instagram. Seguici anche su Google News, per ricevere aggiornamenti quotidiani sulla sicurezza informatica o Scrivici se desideri segnalarci notizie, approfondimenti o contributi da pubblicare.

 Cybercrime
CybercrimeLe autorità tedesche hanno recentemente lanciato un avviso riguardante una sofisticata campagna di phishing che prende di mira gli utenti di Signal in Germania e nel resto d’Europa. L’attacco si concentra su profili specifici, tra…
 Innovazione
InnovazioneL’evoluzione dell’Intelligenza Artificiale ha superato una nuova, inquietante frontiera. Se fino a ieri parlavamo di algoritmi confinati dietro uno schermo, oggi ci troviamo di fronte al concetto di “Meatspace Layer”: un’infrastruttura dove le macchine non…
 Cybercrime
CybercrimeNegli ultimi anni, la sicurezza delle reti ha affrontato minacce sempre più sofisticate, capaci di aggirare le difese tradizionali e di penetrare negli strati più profondi delle infrastrutture. Un’analisi recente ha portato alla luce uno…
 Vulnerabilità
VulnerabilitàNegli ultimi tempi, la piattaforma di automazione n8n sta affrontando una serie crescente di bug di sicurezza. n8n è una piattaforma di automazione che trasforma task complessi in operazioni semplici e veloci. Con pochi click…
 Innovazione
InnovazioneArticolo scritto con la collaborazione di Giovanni Pollola. Per anni, “IA a bordo dei satelliti” serviva soprattutto a “ripulire” i dati: meno rumore nelle immagini e nei dati acquisiti attraverso i vari payload multisensoriali, meno…