
The ransomware landscape is changing. The most exposed actors—LockBit, Hunters International, and Trigona—have paid the price for overexposure, including international operations, infiltrations, deliberate leaks, and operational collapses.
After years dominated by quasi-industrial models—affiliate panels, leak sites, public chats, and aggressive marketing—groups are emerging that reject the “LockBit-style” logic and are moving toward a more opaque, minimal, almost “SIGINT operator” approach. Low-profile , technical, almost “professional,” they adopt strategies of operational invisibility .
The most recent case is MONOLOCK , a new ransomware group that appeared on DarkForums on October 19, 2025 with a manifesto that seems more like it was written by a senior red team than a traditional cybercriminal.
Their presentation is unusual, and above all, much more technical than the average emerging group. And the details offered deserve in-depth analysis.
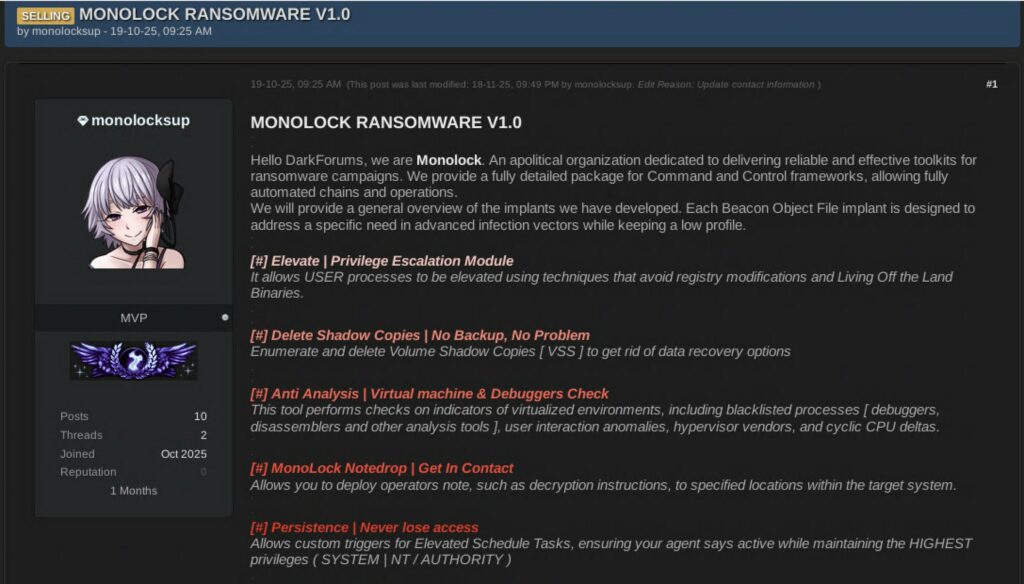
MONOLOCK defines itself as an apolitical organization specialized in the development of toolkits for fully automated ransomware campaigns , with a modular structure based on BOF (Beacon Object File) and payloads loaded directly into memory.
So far, it might seem like just another group. But the turning point comes when it declares what it won’t do:
The reason? Their priority is OPSEC, both for themselves and their affiliates. They openly criticize leak sites: according to MONOLOCK, publishing victims’ names reduces the likelihood of payment, destroys their reputation even if a ransom is paid, and draws excessive attention from law enforcement. It’s a counterintuitive approach—and precisely for this reason, much more sophisticated.
MONOLOCK features a whole suite of modules, all built as BOF (Beacon Object File) , Cobalt Strike’s native technology for executing code directly in memory without file drops.
To the question: “Do you have a TOR site? Have you already had victims?”
They answer like this:
“Hosting extortion updates adds unnecessary weight.
We want to give companies the ability to recover their data and reputation .”
And above all:
An affiliate panel exposes builders, decryptors, affiliate databases, and keys. The FBI, CERTs, and researchers love these infrastructures. We don’t want to make them an easy target.
It’s an almost “intelligence” philosophy.
Their posts reveal a rare awareness: they understand why the great RaaS companies failed. And they don’t want to make the same mistakes.
MONOLOCK is looking for:
And above all: “We don’t accept script kiddies.” A message designed to filter out unprepared affiliates—a strategy also used by groups like Muliaka and former Team Two accounts.
Initial fee: $500
Revenue share: 20% fixed
The developers of the BOF modules have advanced skills:
The team is likely to come from:
One of the most interesting — and rare — passages in MONOLOCK’s communication concerns the theme of EDR evasion .
Unlike many RaaS groups that boast “total UD,” MONOLOCK approaches the topic in a technical, almost professional manner, acknowledging limitations, execution chain, and weaknesses.
In their post they state:
“Our implants beat EDRs, we have tested Windows Defender Endpoint Detection, SentinelOne, Crowdstrike and all of the commercial AVs.”
A strong statement, but immediately accompanied by an explanation unusual for its transparency and technical precision.
Immediately afterwards, in fact, they specify:
“Since we utilize the BoF implant format, our implant execution is based on the C2 connection, meaning that if the shellcode is detected, there is no pipe through which the implants are being loaded . We offer a shellcode loader […] to mitigate precisely this.”
This sentence is crucial.
MONOLOCK is explicitly stating that:
And they add:
“Long story short, if the C2 gets a connection, implants will run no matter what .”
In other words: if the loader manages to get through even once, the beacon will load the BOFs and the entire tool chain will become extremely difficult to detect.
And here’s the most surprising—and in some ways professional—part. When asked why they don’t advertise their toolset as “undetectable,” they reply:
“Why don’t we explicitly mention the ‘UD’ status? We will be straightforward: utilizing UD is a vague expression… it eventually bolds down to each company infrastructure.”
In summary:
This is a level of self-awareness that is very rare in emerging groups.
MONOLOCK isn’t just another ransomware clone. It’s an evolution of the model, a more silent, professional, decentralized, and technical form of ransomware.
It’s the archetype of “boutique ransomware”: small team, advanced code, minimal visibility, maximum efficiency.
We expect the first real campaigns to emerge soon, likely through Initial Access Brokers already active in the Western market. And when they do start, it won’t be easy to notice.
( Actor Profile , MITER ATT&CK, Expected TTPs, IOC )
Follow us on Google News to receive daily updates on cybersecurity. Contact us if you would like to report news, insights or content for publication.
