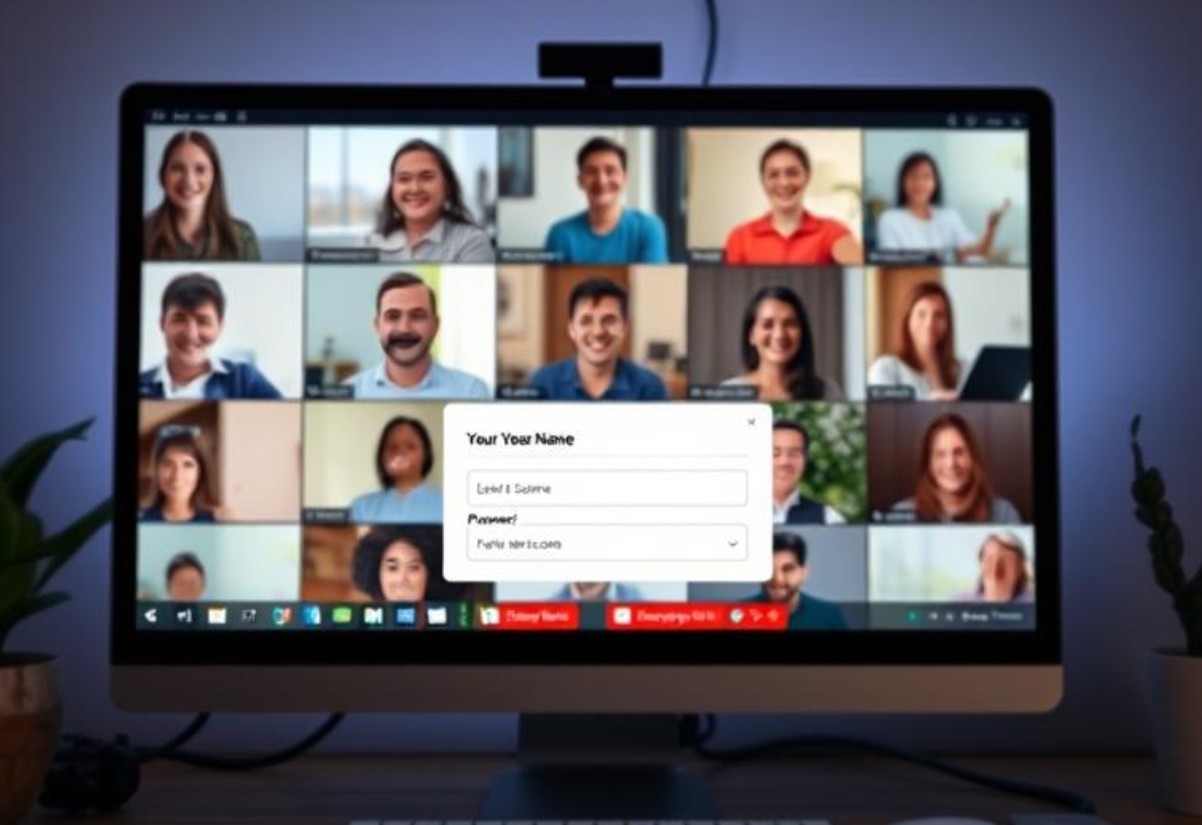
Un attacco di phishing che imita una riunione urgente su Zoom viene utilizzato dai criminali informatici per rubare credenziali aziendali, utilizzando un’interfaccia falsificata così realistica che è quasi impossibile distinguerla da una vera videoconferenza. Cofense, l’azienda che ha scoperto la campagna, afferma di utilizzare un oggetto dell’email allarmante come “Situazione critica – Riunione di emergenza”, per indurre i destinatari a cliccare immediatamente sul link.
Dopo aver cliccato sul link, l’utente vede quella che sembra una connessione alla riunione. Per un po’, vede persino una finta animazione di “partecipazione alla riunione” e un’interfaccia video con immagini di partecipanti che si suppone siano già presenti – alcuni che salutano, altri che annuiscono.
Ma poi arriva il bello: appare un messaggio di errore di connessione e una richiesta di accesso ripetuto.
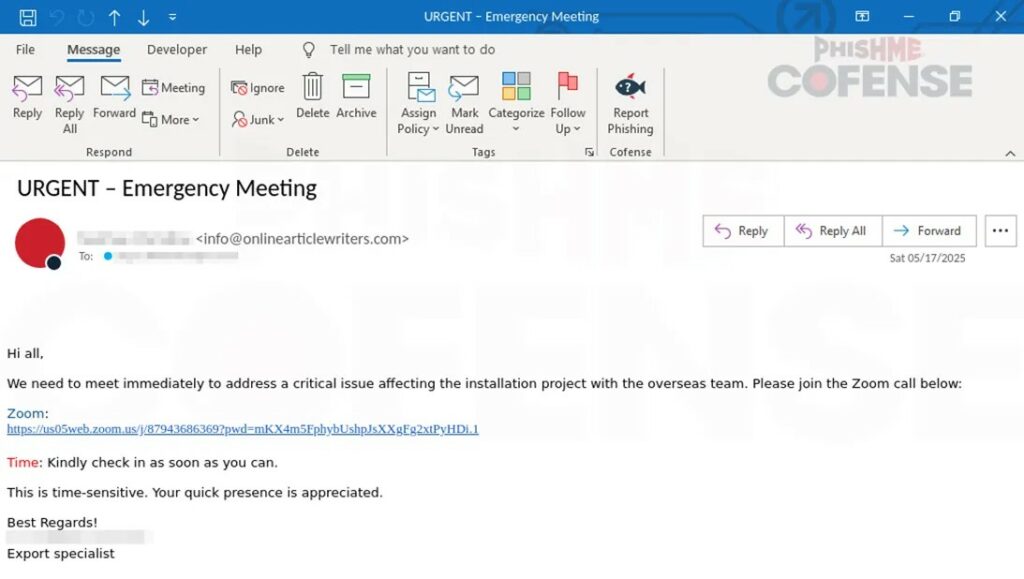
Il falso modulo di accesso a Zoom Workplace compila automaticamente l’indirizzo email aziendale della vittima, aumentando l’effetto di autenticità. I dati inseriti vengono immediatamente inoltrati agli aggressori.
L’attacco si è distinto per l’utilizzo di una tecnica di mascheramento dei link: la catena di reindirizzamenti inizia con l’indirizzo della legittima piattaforma Cirrus Insight CRM, ma alla fine porta a una falsa pagina Zoom ospitata su un dominio cloud poco appariscente.
Gli ideatori di questo schema sperano che la combinazione di autenticità visiva, dati precompilati e senso di urgenza riduca il livello di sospetto e porti a un rapido trasferimento di login e password. Cofense sottolinea che tali attacchi sono particolarmente efficaci quando imitano le comunicazioni aziendali o strumenti aziendali familiari, come Zoom, Teams, Slack e altri. L’elevato tasso di clic di tali email è dovuto al fatto che si integrano nei processi quotidiani, senza causare ansia nei destinatari.
Approcci simili che prevedono falsi relativi a videoconferenze o moduli di accesso sono già stati utilizzati in precedenza, ma questa campagna ne porta la sofisticatezza a nuovi livelli. Animazioni, transizioni fluide dello schermo ed elementi visivi della vera interfaccia Zoom rendono l’attacco quasi indistinguibile da una connessione di riunione legittima. Ciò è particolarmente pericoloso in un ambiente di lavoro ibrido in cui Zoom è diventato parte integrante delle operazioni aziendali.
Gli esperti raccomandano alle organizzazioni di informare ulteriormente i dipendenti su tali scenari, di rafforzare il filtraggio della posta elettronica e di limitare la possibilità di reindirizzamento a risorse esterne utilizzando policy di sicurezza interne. È inoltre importante verificare regolarmente l’autenticità degli URL utilizzati e, in caso di dubbio, aprire i link manualmente anziché cliccandoci sopra.
Come sempre, la consapevolezza al rischio degli esseri umani è l’arma più importante da sviluppare!
Ti è piaciuto questo articolo? Ne stiamo discutendo nella nostra Community su LinkedIn, Facebook e Instagram. Seguici anche su Google News, per ricevere aggiornamenti quotidiani sulla sicurezza informatica o Scrivici se desideri segnalarci notizie, approfondimenti o contributi da pubblicare.

 Cybercrime
CybercrimeLe autorità tedesche hanno recentemente lanciato un avviso riguardante una sofisticata campagna di phishing che prende di mira gli utenti di Signal in Germania e nel resto d’Europa. L’attacco si concentra su profili specifici, tra…
 Innovazione
InnovazioneL’evoluzione dell’Intelligenza Artificiale ha superato una nuova, inquietante frontiera. Se fino a ieri parlavamo di algoritmi confinati dietro uno schermo, oggi ci troviamo di fronte al concetto di “Meatspace Layer”: un’infrastruttura dove le macchine non…
 Cybercrime
CybercrimeNegli ultimi anni, la sicurezza delle reti ha affrontato minacce sempre più sofisticate, capaci di aggirare le difese tradizionali e di penetrare negli strati più profondi delle infrastrutture. Un’analisi recente ha portato alla luce uno…
 Vulnerabilità
VulnerabilitàNegli ultimi tempi, la piattaforma di automazione n8n sta affrontando una serie crescente di bug di sicurezza. n8n è una piattaforma di automazione che trasforma task complessi in operazioni semplici e veloci. Con pochi click…
 Innovazione
InnovazioneArticolo scritto con la collaborazione di Giovanni Pollola. Per anni, “IA a bordo dei satelliti” serviva soprattutto a “ripulire” i dati: meno rumore nelle immagini e nei dati acquisiti attraverso i vari payload multisensoriali, meno…