
The U.S. National Security Agency (NSA) has released the first two documents in its Zero Trust Implementation Guidelines (ZIGs) series, aimed at providing practical and operational guidance to support organizations in adopting the Zero Trust security model.
The guidelines are part of the Zero Trust Maturity Engineer Guidelines framework. They describe the steps required to implement technologies and processes that can achieve the capabilities, activities and expected results defined at the “Target” level.
The two documents released outline the Primer and Discovery Phases , representing the introductory phases of the Zero Trust journey. Their purpose is to prepare organizations for the adoption of the subsequent operational phases, called Phase 1 and Phase 2, which will be published later.
The Primer illustrates the strategic approach used to develop the entire ZIG series and provides an overview of how to best leverage these tools. A key element is the modular structure of the guidelines, designed to allow organizations with varying levels of Zero Trust maturity to select and apply only the capabilities most relevant to their operational context.
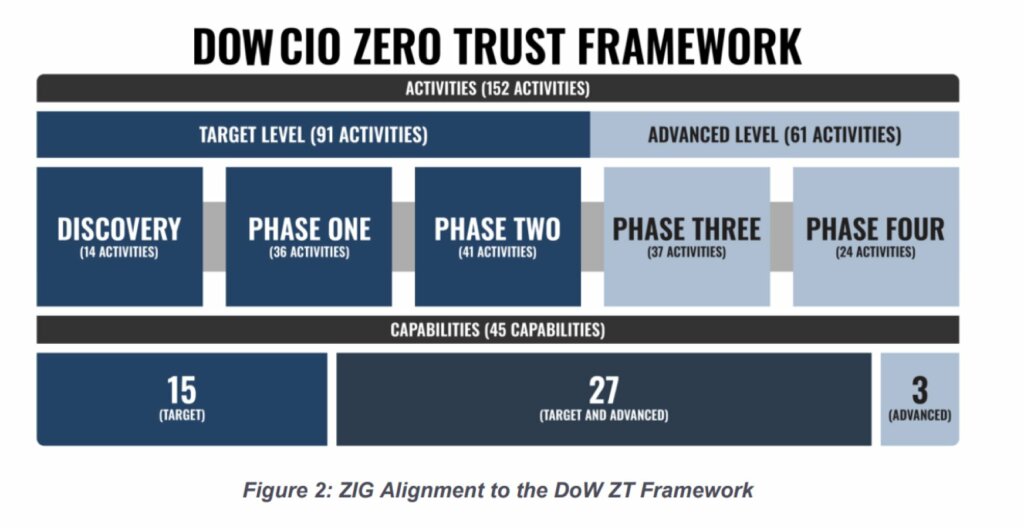
The Discovery Phase is dedicated to building the foundation. The goal is to increase visibility into the IT environment by identifying critical data, applications, assets, services, and access flows already present in the architecture. This phase allows for the establishment of a reliable baseline, essential for prioritizing and planning consistent interventions in subsequent phases.
According to the NSA, system managers, cybersecurity professionals, and stakeholders should carefully review these preliminary documents to gain a thorough understanding of Zero Trust activities and their operational perimeter before the next guidance is released.
ZIGs clarify a fundamental point: Zero Trust is not a product or a single technology , but a security operating model. Unlike traditional approaches, which rely on the idea of a trusted perimeter, Zero Trust assumes that every access request is potentially hostile, regardless of its origin.
The spread of cloud computing, remote working, API architectures, and SaaS applications has rendered models based solely on perimeter defense ineffective. In this context, Zero Trust aims to limit lateral movement, reduce the impact of compromises, and prevent an initial breach from escalating into a systemic incident.
The phrase “never trust, always verify” doesn’t imply indiscriminately blocking activities. Rather, it means that trust must be explicit, limited in time, circumscribed, and continually reassessed . Network location or ownership of a company device are no longer sufficient to grant access.
In the Zero Trust model, the focus shifts from networks to resources. The security question is no longer “where is the traffic coming from,” but “can this identity, with this device and in this context, perform this action on this resource at this time?”
Traditional systems assumed that threats were predominantly external. Today, many breaches occur through valid credentials obtained through phishing or other identity-based attacks. Once the perimeter is breached, flat networks and weak internal controls facilitate privilege escalation and data exfiltration.
Zero Trust assumes that a breach is inevitable at some point and focuses efforts on limiting the impact and the ability to quickly contain an attack.
A Zero Trust architecture defines how access decisions are made, enforced, and monitored. Conceptually, it includes three main functions: a decision-making component that evaluates requests, an administrative layer that translates decisions into operational rules, and enforcement points that apply controls.
This approach allows you to centralize policies while maintaining distributed control enforcement, whether on-premises, in the cloud, or in hybrid environments. The separation of policy logic and network topology ensures consistency even across heterogeneous environments.
In the Zero Trust model, identity represents the primary security boundary. It concerns not only users, but also applications, services, and infrastructure components. Strong authentication, privilege management, and account separation become key elements.
Multi-factor authentication is considered the minimum requirement, while phishing-resistant solutions are preferred for high-risk contexts. The principle of least privilege limits permanent access and favors the use of temporary, just-in-time privileges.
Identity alone isn’t enough. Even a legitimate user can pose a risk if they use a compromised device. Therefore, endpoint security status becomes a crucial signal in access decisions.
Zero Trust doesn’t necessarily require the exclusive use of corporate devices, but it does require that the device’s risk level influence the permissions granted. Loss of compliance can lead to dynamic access revocation, reducing attackers’ dwell time.
The network isn’t disappearing, but it’s losing its role as a trusted element. Access is no longer based on membership in an internal network, but rather on criteria related to identity and context. Users access individual applications, not entire network segments.
This approach dramatically limits lateral movement and simplifies access management, especially in complex, distributed environments.
The success of Zero Trust depends on applications’ ability to support fine-grained authorization controls. Modern architectures use tokens with limited permissions and robust service identities, avoiding static credentials embedded in code.
The ultimate goal remains data protection . Security must extend to the information layer, with controls based on identity, device status, and contextual risk, even at the level of individual records or fields.
Policies are not static: they are continuously reevaluated based on the signals collected. Access valid at the time of login can be revoked if risk conditions change.
Visibility is a prerequisite. Every login event generates data useful for detecting anomalies. Automation allows you to react quickly, isolating devices or revoking credentials without manual intervention.
Zero Trust also requires a shared governance model, involving multiple teams and providing for structured exception management, which is always documented and time-limited.
Progress isn’t measured by the tools adopted, but by risk reduction. Key indicators include a reduction in standing privileges, increased use of MFA, reduced opportunities for lateral movement, and faster incident response.
A mature environment does not eliminate breaches, but it limits their impact and improves early detection capabilities.
Implementing Zero Trust represents a long-term strategic transformation. It doesn’t eliminate trust, but makes it managed, temporary, and measurable. Organizations that successfully adopt this model don’t just introduce new technologies, they also structurally rethink the very concept of access.
Follow us on Google News to receive daily updates on cybersecurity. Contact us if you would like to report news, insights or content for publication.
