
Cybercriminals are getting smarter and have found a new way to exploit corporate security protocols. It seems incredible, but it’s true: they’re using a legitimate Microsoft authentication feature to steal user accounts.
Proofpoint’s research team has detected a rise in “Device Code Phishing,” a phishing technique that tricks victims into granting complete control over their accounts simply by entering a code on a trusted website. It’s as if attackers have found a way to exploit security protocols as a weakness. But how exactly does this technique work? And what can companies do to protect themselves? Let’s find out!
“Traditional phishing awareness often emphasizes verifying the legitimacy of URLs. This approach does not effectively address device code phishing, in which users are asked to enter a device code on the Microsoft trusted portal,” the experts wrote in their report.
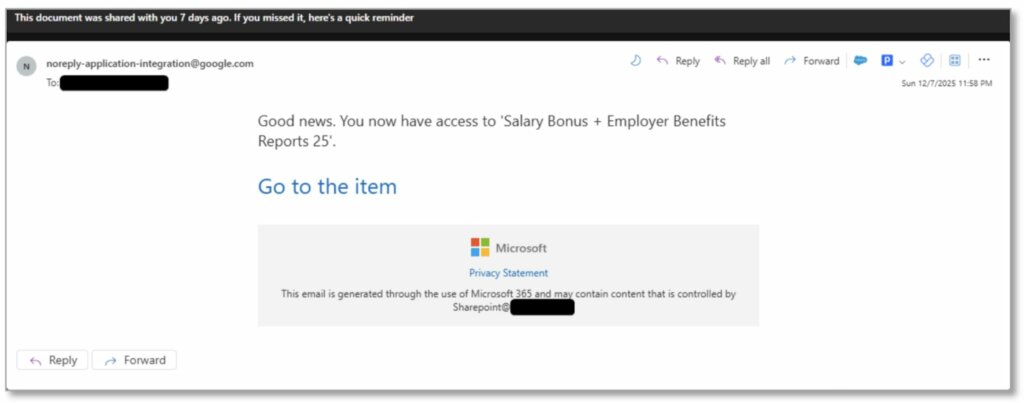
The campaign highlights a shift in tactics : instead of stealing passwords directly, hackers steal the account “keys” themselves via the OAuth 2.0 protocol. The attack exploits the device authorization flow , a feature designed to help users access devices with limited input capabilities, such as smart TVs or printers. When the device is legitimate, it displays a code, and the user enters it on a separate computer or phone to authorize access.
Attackers have hijacked this process. They send phishing emails containing a code and a link to Microsoft’s official login portal ( microsoft.com/devicelogin ). Because the URL is legitimate, standard phishing training often fails. This isn’t an isolated technique used by a single group. Proofpoint researchers have observed “multiple threat clusters, both state-sponsored and financially motivated,” using this method.
Once the user enters the code, the attacker’s malicious application is granted a token that allows persistent access to the victim’s Microsoft 365 account . This access can be used to “exfiltrate data and more,” often bypassing the need to know the user’s password in future sessions.
Account Takeover (ATO) is a cyberattack technique in which a criminal gains complete control of a legitimate account by impersonating the real user without arousing immediate suspicion. Unlike traditional breaches, ATO doesn’t necessarily require password theft: attackers can exploit authentication tokens, OAuth flows, or legitimate login mechanisms to gain technically valid access to the account. This makes the attack particularly insidious, because security systems register the access as legitimate.
Once an account is compromised, the attacker can read emails, access confidential documents, create invisible forwarding rules, launch internal fraud, or maintain persistent access over time , even after a password change. Account takeover is one of the most dangerous threats to organizations today, as it exploits the trust placed in modern authentication mechanisms and in the user’s digital identity itself, turning legitimate access into a vector for compromise.
The key to the success of these attacks lies in manipulating user psychology. A sense of urgency is created by lures, which often mimic security warnings or administrative requests . Attackers, by portraying the attack as a mandatory check or security update, trick users into taking the action that leaves them vulnerable.
As organizations strengthen their defenses with multi-factor authentication (MFA) and FIDO keys, attackers are forced to find alternative solutions. Abuse of valid authorization flows appears to be the next frontier. “Proofpoint estimates that abuse of OAuth authentication flows will continue to grow with the adoption of FIDO-compliant MFA controls,” the researchers concluded.
Defending against this type of attack requires a paradigm shift: simply teaching users to check URLs is no longer enough . Device Code Phishing exploits legitimate portals and valid authentication flows, making training based solely on recognizing fake sites ineffective. It is therefore essential to combine user awareness with targeted technical controls on OAuth flows.
From an operational standpoint, organizations should limit or disable Device Code Flow where not strictly necessary and apply more restrictive Conditional Access policies , including MFA for OAuth flows as well as for interactive login. Controlling the access context (location, device, session risk) becomes crucial to intercept anomalous uses of seemingly legitimate tokens.
Finally, it’s essential to monitor and govern authorized OAuth applications in the tenant. The use of unverified or overly privileged apps represents an often overlooked compromise vector. Regularly reviewing consents, following the principle of least privilege, and monitoring authentication logs related to Device Code Flow can make the difference in detecting and containing an account takeover before access becomes persistent.
Follow us on Google News to receive daily updates on cybersecurity. Contact us if you would like to report news, insights or content for publication.
