
During a coordinated international operation dubbed Operation Checkmate, law enforcement officials have dealt a major blow to the BlackSuit ransomware group (onion link here, which has fallen into the hands of law enforcement, by seizing their Data Leak Sites (DLS). This targeted action was conducted to counter attacks that have targeted and compromised the networks of hundreds of organizations globally in recent years.
The U.S. Department of Justice confirmed the seizure of the BlackSuit domains, with the .onion websites replaced with a banner announcing their closure by authorities, underscoring the breadth of the internationally coordinated investigation. Among the seized sites were data leak blogs and trading platforms used to extort money from victims.
The Forces Involved The operation involved extensive collaboration between various security and law enforcement agencies worldwide. Key participants include:

The BlackSuit ransomware operation emerged between April and May 2023. The group is a multi-pronged extortion organization that encrypts and exfiltrates victims’ data and hosts public data leak sites for victims who do not They comply with their demands. The group was known for its significant attacks against healthcare and education entities, among other critical sectors. BlackSuit is a private operation as it has no public affiliates. BlackSuit payloads share many technical similarities with the Royal ransomware payloads, such as similar encryption mechanisms and command-line parameters.
Large enterprises and small and medium-sized businesses (SMBs) are targeted, although there does not appear to be any specific discrimination in terms of sector or target type. Similar to Royal, it appears that CIS (Commonwealth of Independent States) entities are excluded. To date, BlackSuit attacks have benefited companies in the healthcare, education, information technology (IT), government, retail, and manufacturing sectors.
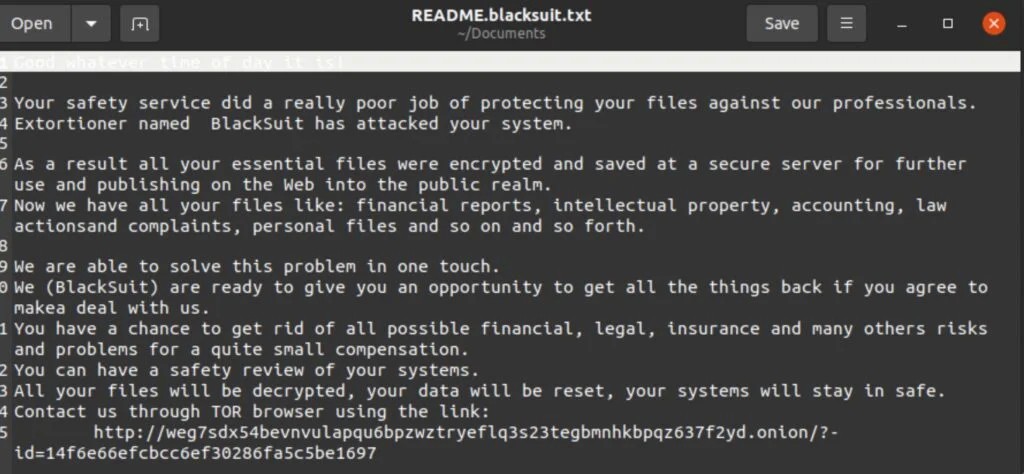
“Operation Checkmate” represents a Another significant step forward in the global fight against cybercrime, demonstrating the effectiveness of international cooperation in disrupting ransomware networks and providing support to victims.
In recent months, law enforcement agencies have been enjoying considerable success in operations against cybercriminal groups, and cybercriminals know this well. It’s not uncommon to find discussions in underground forums where malicious actors themselves comment on recent police operations, admitting that their job is becoming increasingly risky.
However, the significant profits derived from ransomware continue to be an irresistible motivator, keeping criminals’ attention focused on this business: the number of attacks suffered by companies and the sums spent to combat them show no sign of decreasing.
As in other similar successful situations against ransomware groups, a decryptor has been produced and made available to allow affected companies to regain access to their data and break the encryption. This crucial step aims to mitigate the damage suffered by victims and support organizations in restoring their operations.
Follow us on Google News to receive daily updates on cybersecurity. Contact us if you would like to report news, insights or content for publication.
