
Last week, Oracle warned customers of a critical zero-day vulnerability in its E-Business Suite (CVE-2025-61882), which allows remote execution of arbitrary code without authentication. It has now been revealed that the Clop hacker group has been actively exploiting this vulnerability for cyberattacks since August 2025.
The vulnerability was discovered in the Oracle Concurrent Processing component of Oracle E-Business Suite (BI Publisher integration module) and received a CVSS score of 9.8. This high score is due to the lack of authentication and ease of exploitation.
Oracle representatives announced that the zero-day vulnerability affects Oracle E-Business Suite versions 12.2.3-12.2.14 and released an emergency update . The company also emphasized that customers must first install the October 2023 critical patch update before installing the patch.
Because a public proof-of-concept exploit for the vulnerability existed and had already been used in attacks, Oracle administrators were advised to install the patch as soon as possible.
According to Charles Carmakal, Chief Technology Officer at cybersecurity firm Mandiant, CVE-2025-61882 and several other bugs fixed in the July update were used by the Clop hacker group to steal data from Oracle E-Business Suite servers as early as August 2025.
Furthermore, even before the patch was released, experts from Mandiant and the Google Threat Intelligence Group (GTIG) had reported that they were tracking a new malicious campaign targeting Oracle E-Business Suite . At the time, several companies had received emails from the attackers. In these messages, Clop representatives claimed to have stolen data from Oracle E-Business Suite and demanded a ransom, threatening to publish the stolen information if they failed to do so.
CrowdStrike analysts confirm they first noticed Clop attacks targeting CVE-2025-61882 in early August of this year. Researchers believe other groups may have been involved in the attacks.
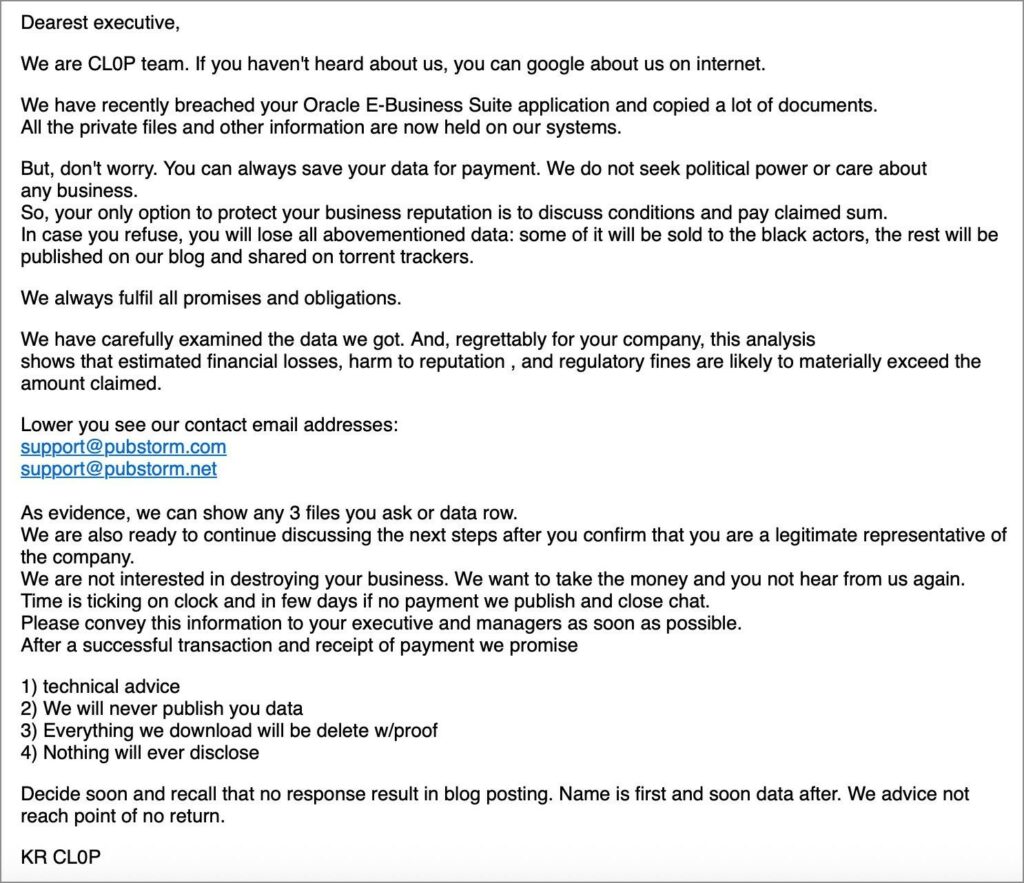
“CrowdStrike Intelligence believes with moderate confidence that GRACEFUL SPIDER is likely involved in this campaign. We cannot rule out the possibility that CVE-2025-61882 is being exploited by multiple threat actors. The first known exploit was discovered on August 9, 2025, but investigations are ongoing and this date may change,” the researchers stated.
As Bleeping Computer points out, although the Clop group is behind the data theft and zero-day exploitation, information about this vulnerability was first published by the Scattered Lapsus$ Hunters group (an association of members of the Scattered Spider, LAPSUS$, and Shiny Hunters hacker groups), who posted two files mentioning Clop on Telegram.
One of these (GIFT_FROM_CL0P.7z) contained Oracle source code, presumably related to support.oracle.com. Later, several Lapsus$ hackers claimed that this code had been stolen during the Oracle Cloud hack in February 2025.
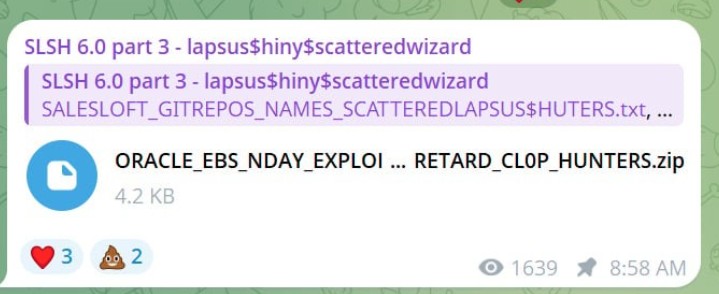
The second file (ORACLE_EBS_NDAY_EXPLOIT_POC_SCATTERED_LAPSUS_RETARD_CL0P_HUNTERS.zip) purportedly contained the Oracle E-Business Suite exploit used by Clop . The archive contained a readme.md statement and two Python scripts: exp.py and server.py. These scripts are used to exploit vulnerable Oracle E-Business Suite installations by executing arbitrary commands or opening reverse shells, connecting to the attacker’s servers.
It’s still unclear how the Scattered Lapsus$ Hunters gained access to the exploit and their connection to Clop. The hackers themselves claim that one of the people they shared the exploit with may have passed it on or sold it to Clop.
“It was my exploit, like SAP’s, which was later stolen by Clop. I was angry that another of my exploits was being misused by another group, so we leaked it. No complaints against Clop,” said one group member.
As researchers at watchTowr Labs discovered after reverse engineering an exploit leaked by Scattered Lapsus$ Hunters and dated May 2025, CVE-2025-61882 is actually a chain of vulnerabilities that allows attackers to achieve unauthenticated remote code execution using a single HTTP request.
Follow us on Google News to receive daily updates on cybersecurity. Contact us if you would like to report news, insights or content for publication.
