
Can an encrypted email cause a macOS/iOS system to crash immediately? The answer is YES!
This is not a science fiction plot, but a real attack, as revealed by the latest research findings from Alibaba Security. To effectively prevent this type of attack, Alibaba Security and Indiana University Bloomington jointly explored and discovered an attack vector to detect potential DoS (Denial-of-Service) security issues in cryptographic algorithm libraries: malformed X.509 certificates.
They then conducted a series of searches for related problems in cryptographic algorithm libraries based on this vector. This result was made public at the USENIX Security ’25 conference and was nominated for the Pwnie Awards, the “Oscars of the hacker world.”
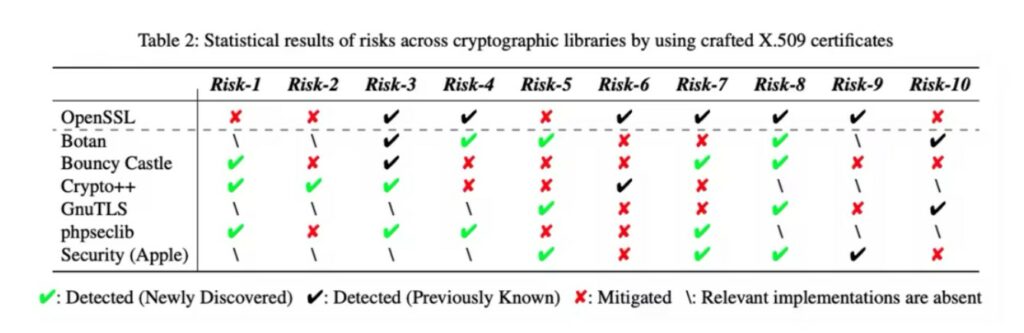
Using malformed X.509 certificates, the researchers conducted experiments on six open-source cryptographic algorithm libraries. traditional: OpenSSL, Botan, Bouncy Castle, Crypto++, GnuTLS, and phpseclib, as well as a cryptographic library specifically designed for the Apple ecosystem.
18 new CVE vulnerabilities have been discovered and 12 known CVE vulnerabilities identified.
With the widespread use of the Internet, network security issues are becoming increasingly important. To ensure the security and reliability of network communications, digital certificates have become a fundamental tool for ensuring identity authentication and data security.
A digital certificate is like an “ID card”” in the online world. It is issued by a trusted third-party organization (called a certificate authority, CA) and is used to verify the identity of both communicating parties and ensure that information is not tampered with during transmission.
Currently, X.509 is one of the most widely adopted digital certification standards internationally. It defines the basic structure and content of a certificate, including fields such as subject information, public key, signature algorithm, and validity period, and supports certificate chain verification mechanisms, thus creating a trusted public key infrastructure (PKI).
Furthermore, X.509 certificates have become a fundamental component of modern network security, used in various protocols (such as TLS and S/MIME) to ensure secure communications. Even modern operating systems (such as macOS and iOS) use X.509 certificates to verify signatures, ensuring the authenticity and integrity of applications.
Cryptography-related APIs are often complex in design, and many developers lack specific knowledge. The contradiction between these two aspects leads to frequent misuse of cryptographic APIs in practice, which has prompted existing research to focus on how to best counteract the misuse of cryptographic APIs.
However, even if users strictly adhere to the usage specifications and correctly call the API in a cryptographic library, security risks may still arise due to security issues in the API implementation itself.
Current research on security issues in cryptographic implementations mainly focuses on confidentiality (such as side-channel attacks) and integrity (such as hash collisions) in the CIA (confidentiality, integrity, and availability) triplet, while less attention is paid to availability issues. However, the research team noted that cryptographic libraries are often more vulnerable to DoS attacks than other types of projects due to the following two characteristics:
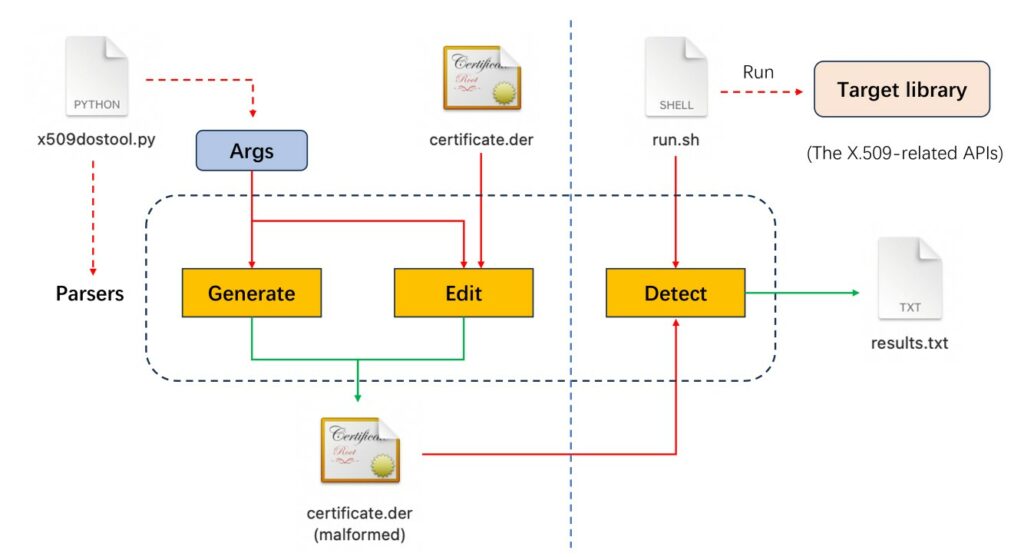
To further validate this observation, the research team conducted a systematic analysis of code implementations in several cryptographic libraries vulnerable to DoS attacks. In the process, they demonstrated the feasibility of using malformed X.509 certificates as an attack vector to exploit and detect DoS issues in cryptographic libraries.
The main contributions of this work include the following three points:
This section is detailed in Section 1 of the article. Additionally, to better understand the content of subsequent chapters, readers are advised to refer to the basic knowledge introduction in Section 2 of the article for a deeper understanding of the mathematical aspects of elliptic curves, ASN.1, and X.509.
In this work, researchers focused on this attack and further analyzed the mechanisms and exploitation methods of a series of DoS-related vulnerabilities in cryptographic libraries. Using automated tools, they discovered 18 new vulnerabilities in seven major cryptographic libraries. They then demonstrated these vulnerabilities in two real-world scenarios: the reciprocal TLS handshake on HTTPS websites and signature verification on Apple macOS/iOS systems.
The experimental results demonstrate the feasibility of their malformed X.509 certificates in detecting and exploiting DoS vulnerabilities in cryptographic libraries. They also reveal that X.509 DoS attacks represent a widespread but understudied security threat, deserving of greater attention. They also discuss the root causes of these attacks and propose a series of possible mitigation strategies.
In the future, the research team hopes that this work will further raise the security community’s awareness of cryptographic vulnerabilities and attack methods and inspire more researchers to explore effective detection and defense mechanisms, jointly promoting the construction of cryptographic systems and protecting user security.
Follow us on Google News to receive daily updates on cybersecurity. Contact us if you would like to report news, insights or content for publication.
